filmov
tv
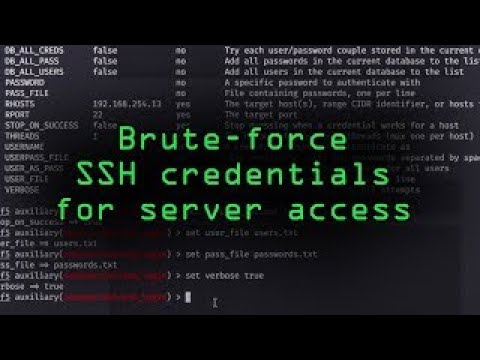
How Hackers Could Brute-Force SSH Credentials to Gain Access to Servers

Показать описание
Three Ways Hackers Can Hack into SSH Servers
Cyber Weapons Lab, Episode 181
The Secure Shell, or SSH, is a common way to access remote hosts. However, it's not as secure as the name would imply. In this episode of Cyber Weapons Lab, we are going to show three different ways to brute force username and password combinations on open SSH ports. Big thanks goes to Null Byte writer drd_ who wrote the article we're basing the video on.
Follow Null Byte on:
Комментарии