filmov
tv
CN 38 : IDS (Intrusion Detection System) | NIDS | HIDS | Examples

Показать описание
Connect with me by:
LIKE & SHARE Videos with your friends.
SUBSCRIBE @csittutorialsbyvrushali
COMPUTER NETWORK & SECURITY
SOFTWARE ENGINEERING:
DATABASE MANAGEMENT SYSTEM:
MACHINE LEARNING USING PYTHON:
DATA STRUCTURE & ALGORITHMS:
HUMAN COMPUTER INTERACTION :
SYSTEM PROGRAMMING / COMPILER DESIGNING:
PROCESSOR ARCHITECTURE & INTERFACE:
EXAM / INTERVIEW PREPARATION:
PROJECT/ PRESENTATION & FREE CERTIFICATION IDEAS:
Keep Watching..!
Keep Learning..!
Thank You..!
#computernetwork #computernetworking #networking #networksecurity #idsoftware #ids2024 #intrusiondetection #nids #hids #engineering #csandittutorialsbyvrushali #vrushali #trending
LIKE & SHARE Videos with your friends.
SUBSCRIBE @csittutorialsbyvrushali
COMPUTER NETWORK & SECURITY
SOFTWARE ENGINEERING:
DATABASE MANAGEMENT SYSTEM:
MACHINE LEARNING USING PYTHON:
DATA STRUCTURE & ALGORITHMS:
HUMAN COMPUTER INTERACTION :
SYSTEM PROGRAMMING / COMPILER DESIGNING:
PROCESSOR ARCHITECTURE & INTERFACE:
EXAM / INTERVIEW PREPARATION:
PROJECT/ PRESENTATION & FREE CERTIFICATION IDEAS:
Keep Watching..!
Keep Learning..!
Thank You..!
#computernetwork #computernetworking #networking #networksecurity #idsoftware #ids2024 #intrusiondetection #nids #hids #engineering #csandittutorialsbyvrushali #vrushali #trending
CN 38 : IDS (Intrusion Detection System) | NIDS | HIDS | Examples
Monitor in Real-Time with OSSEC | See What’s Taking Place in Your Server
What is the Network Layer
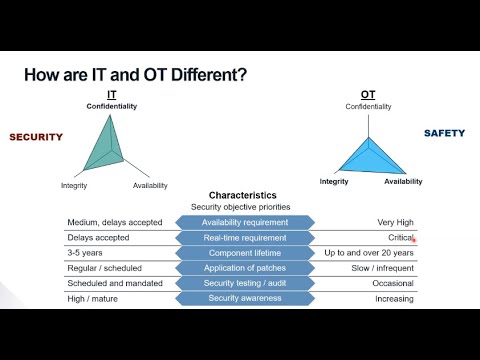
What is OT | What are OT Cyber Security Challenges | OT Security Solutions | What is ICS and SCADA
#55 IP Security - Applications Of IPSec, IPSec Architecture |CNS|
#40 Kerberos - Authentication Protocol, Working with diagram|CNS|
CISSP Review Program - Network Layer Threats, Security Concerns and Countermeasures
Cybersecurity A Comprehensive Guide to Protect Your Data webinar
CompTIA Network+ Certification Video Course
Xvci JLR install
68. Types Of Firewalls - 3 Types |CNS|
Use Process Explorer to scan running processes via virustotal
What is a process explorer?
#37 Digital Signature In Cryptography |CNS|
#15 Unified - Starting Point - Hack The Box || Complete Walkthrough
A Lustrum of Malware Network Communication: Evolution and Insights
#35 MAC ( Message Authentication Code ) - Working and Significance |CNS|
Using a Modular Approach to Network Design 2 - Structuring and Modularizing the Network
What are Advanced Persistent Threats and why Should your Organization Care?
Cyber Security Malicious code
Cai dat va cau hinh Snort IDS trên Linux
Professor Messer's Security+ Study Group - August 2018
#58 Combining Security Associations - Case 1,2,3,4 |CNS|
Introduction to Intruders in computer Network
Комментарии
 0:08:03
0:08:03
 0:41:23
0:41:23
 0:00:18
0:00:18
 1:38:23
1:38:23
 0:06:02
0:06:02
 0:07:01
0:07:01
 0:02:08
0:02:08
 0:58:51
0:58:51
 3:46:51
3:46:51
 0:06:38
0:06:38
 0:09:13
0:09:13
 0:00:29
0:00:29
 0:01:13
0:01:13
 0:08:03
0:08:03
 0:14:58
0:14:58
 0:18:59
0:18:59
 0:07:13
0:07:13
 0:28:54
0:28:54
 0:08:05
0:08:05
 0:01:16
0:01:16
 0:27:25
0:27:25
 2:19:10
2:19:10
 0:08:01
0:08:01
 0:18:22
0:18:22