filmov
tv
#37 Digital Signature In Cryptography |CNS|

Показать описание
Abroad Education Channel :
Company Specific HR Mock Interview :
A seasoned professional with over 18 years of experience with Product, IT Services and Agri industry of valuable experience in Human Resource Management, Extensive Experience in Talent Acquisition, Personnel Management, Compensation and Benefits, Performance Reviews, Training & Development and all facets of Human Resources will be performing mock HR Interviews and provides feedback on the session and guides with interview techniques.
paper presentation for semester exams :
Company Specific HR Mock Interview :
A seasoned professional with over 18 years of experience with Product, IT Services and Agri industry of valuable experience in Human Resource Management, Extensive Experience in Talent Acquisition, Personnel Management, Compensation and Benefits, Performance Reviews, Training & Development and all facets of Human Resources will be performing mock HR Interviews and provides feedback on the session and guides with interview techniques.
paper presentation for semester exams :
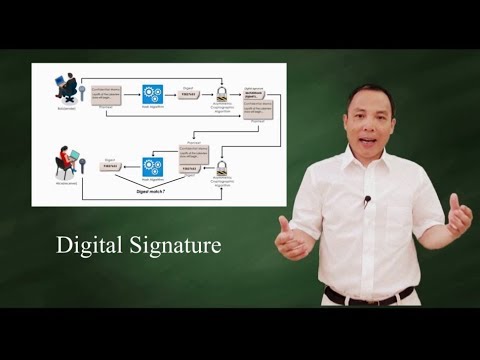
#37 Digital Signature In Cryptography |CNS|
2 - Cryptography Basics - Digital Signature
Digital Signatures
Digital Signatures
Digital Signature Algorithm (DSA) - Cryptography - Practical TLS
Introduction to Cryptography: Digital Signatures
Part 5 Encoding Crypto Digital Signature In Java - Digital Signature
Digital Signature | Cryptography and Network Security
Lab on Attack on Digital Signature/ Hash collision #cryptography #cyberinvestigation
Digital Signatures: Breaking the RSA Signature Scheme
Cryptography with Python 37: Non-repudiation as a security goal
What is digital signature?
Introduction to Digital Signatures
Digital Signature
Digital Signature Algorithm
PKI Public Key Infrastructure
Hashing and Digital Signatures - CompTIA Security+ SY0-701 - 1.4
Unveiling Post-Quantum Fusion Digital Signatures with Geometry Labs
Monero Ring Signatures Explained
Digital Signatures, Message Integrity, and Authentication | Computer Networks Ep 8.3 | Kurose & ...
Advanced Encryption Techniques⬇️
Chapter 12 - Digital Signature
TLS Essentials 7: Non-repudiation with digital signatures
Digital Signature in Cryptography - FarhanaSathath
Комментарии
 0:08:03
0:08:03
 0:05:17
0:05:17
 0:08:13
0:08:13
 0:03:36
0:03:36
 0:05:47
0:05:47
 0:12:18
0:12:18
 1:00:12
1:00:12
 0:16:17
0:16:17
 0:01:52
0:01:52
 0:05:55
0:05:55
 0:02:19
0:02:19
 0:05:03
0:05:03
 0:05:24
0:05:24
 0:35:45
0:35:45
 0:14:09
0:14:09
 0:00:06
0:00:06
 0:10:24
0:10:24
 0:38:33
0:38:33
 0:00:48
0:00:48
 0:14:37
0:14:37
 0:00:33
0:00:33
 0:09:16
0:09:16
 0:04:54
0:04:54
 0:05:36
0:05:36