filmov
tv
How Ghidra Changed Reverse Engineering Forever

Показать описание
Explore how Ghidra, the powerful reverse engineering tool developed by the NSA, has revolutionized the field of cybersecurity and transformed the way professionals analyze and understand complex software systems. In this video, we dive into the features that make Ghidra a game-changer, from its disassembly and decompilation capabilities to its collaborative framework designed for teams. Whether you're an IT professional, cybersecurity enthusiast, or someone pursuing a career in ethical hacking or malware analysis, this video will provide valuable insights into how Ghidra simplifies reverse engineering tasks and supports cyber defense strategies.
Learn why cybersecurity professionals are leveraging Ghidra for malware detection, vulnerability research, and software security analysis. Discover how this free and open-source tool compares to other industry standards like IDA Pro, and why it’s become an essential part of any cybersecurity toolkit.
If you're looking to enhance your skills in reverse engineering, break into the exciting world of cybersecurity, or stay updated on top tools for IT and technology experts, this video is a must-watch. Don’t miss out—hit play now and take your cybersecurity knowledge to the next level! Subscribe for more cybersecurity tutorials and insights.
#Ghidra #ReverseEngineering #Cybersecurity #ITProfessionals #EthicalHacking
🐦 X (Twitter): @yanivhoffman
📚 OccupyTheWeb Books - Affiliate Links:
🌐 OccupyTheWeb Community - Hackers-Arise:
🎟️ 20% Coupon Code: "YANIV" (Use for everything in the store!)
⏱️ Chapters:
00:00-01:12 - 🗒️ What We'll Cover Today
01:12-02:13 - 📖 New OTW Book Announcement!
02:13-04:14 - 🛠️ The Most Important Tools in Cybersecurity
04:14-08:47 - 🔍 Introduction to Ghidra Tool
08:47-16:47 - 🚀 How to Use Ghidra (Step-by-Step)
16:47-28:59 - ⚙️ Simple vs. Advanced Ways to Use Ghidra
28:59-35:40 - 🖥️ SMBV1 Analysis
35:40-48:17 - 🧑💻 Decompiling the Main Function with Ghidra
48:17-57:51 - 🔓 How Do People Crack Software?
57:51-1:01:39 - 📌 Summary and Conclusion
🎥 Watch More Cybersecurity Fundamental Videos:
Learn why cybersecurity professionals are leveraging Ghidra for malware detection, vulnerability research, and software security analysis. Discover how this free and open-source tool compares to other industry standards like IDA Pro, and why it’s become an essential part of any cybersecurity toolkit.
If you're looking to enhance your skills in reverse engineering, break into the exciting world of cybersecurity, or stay updated on top tools for IT and technology experts, this video is a must-watch. Don’t miss out—hit play now and take your cybersecurity knowledge to the next level! Subscribe for more cybersecurity tutorials and insights.
#Ghidra #ReverseEngineering #Cybersecurity #ITProfessionals #EthicalHacking
🐦 X (Twitter): @yanivhoffman
📚 OccupyTheWeb Books - Affiliate Links:
🌐 OccupyTheWeb Community - Hackers-Arise:
🎟️ 20% Coupon Code: "YANIV" (Use for everything in the store!)
⏱️ Chapters:
00:00-01:12 - 🗒️ What We'll Cover Today
01:12-02:13 - 📖 New OTW Book Announcement!
02:13-04:14 - 🛠️ The Most Important Tools in Cybersecurity
04:14-08:47 - 🔍 Introduction to Ghidra Tool
08:47-16:47 - 🚀 How to Use Ghidra (Step-by-Step)
16:47-28:59 - ⚙️ Simple vs. Advanced Ways to Use Ghidra
28:59-35:40 - 🖥️ SMBV1 Analysis
35:40-48:17 - 🧑💻 Decompiling the Main Function with Ghidra
48:17-57:51 - 🔓 How Do People Crack Software?
57:51-1:01:39 - 📌 Summary and Conclusion
🎥 Watch More Cybersecurity Fundamental Videos:
Комментарии
 1:01:40
1:01:40
 0:13:56
0:13:56
 0:52:05
0:52:05
 0:17:44
0:17:44
 0:17:24
0:17:24
 1:00:11
1:00:11
 0:07:26
0:07:26
 0:02:23
0:02:23
 0:09:15
0:09:15
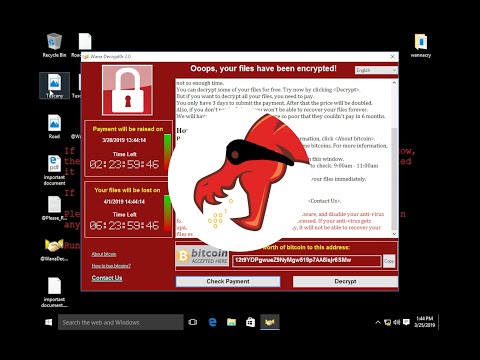 0:22:31
0:22:31
 0:54:46
0:54:46
 0:04:09
0:04:09
 0:02:35
0:02:35
 0:47:02
0:47:02
 0:17:17
0:17:17
 0:01:41
0:01:41
 0:48:32
0:48:32
 0:01:38
0:01:38
 0:12:35
0:12:35
 0:22:37
0:22:37
 0:11:33
0:11:33
 0:19:47
0:19:47
 0:35:19
0:35:19
 0:03:19
0:03:19