filmov
tv
Hacker's Gave me a Game and I Found a Virus
Показать описание
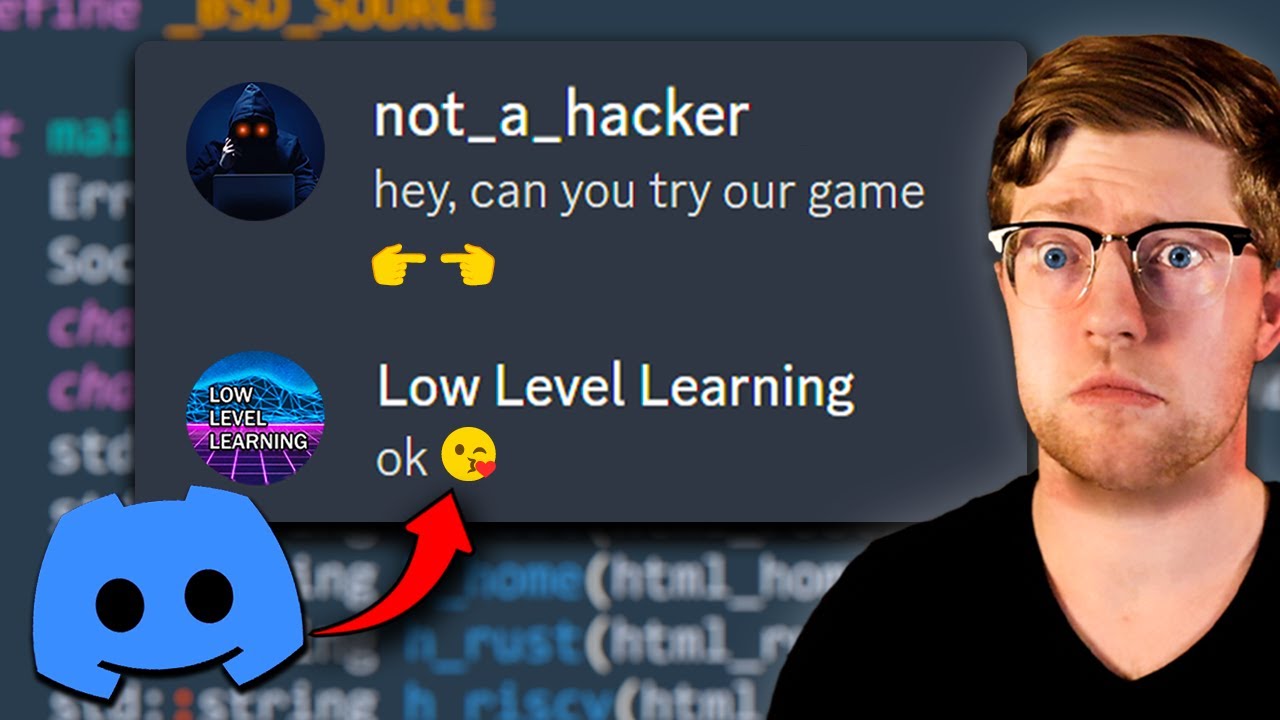
A hacker put malware on a Discord server that I hang out on, so naturally I downloaded it to see what it did. Instead of just running the software, I tried to reverse engineer it to get a peek underneath the hood at the assembly and see what was going on. I quickly found out there was MUCH more than what meets the eye with this malware.
🛒 GREAT BOOKS FOR THE LOWEST LEVEL🛒
🏫 COURSES 🏫
🔥🔥🔥 SOCIALS 🔥🔥🔥
🛒 GREAT BOOKS FOR THE LOWEST LEVEL🛒
🏫 COURSES 🏫
🔥🔥🔥 SOCIALS 🔥🔥🔥
Hacker's Gave me a Game and I Found a Virus
Watch This Russian Hacker Break Into Our Computer In Minutes | CNBC
25 Hackers That TROLLED YouTubers
Me Hacking in Jailbreak (apparently)
I Trolled Streamers With Hacks!
Watch these hackers crack an ATM in seconds
20 Fortnite Hackers That TROLLED Youtubers
24 GAMING Easter Eggs FOUND BY HACKERS!
'Stop Hackers Hacking Your PlayStation 5 Account!'
How to LEARN HACKING
Learning to Hack as a Kid
Trolling Fake Hackers with a Real One...
Hackers Destroyed This Roblox Game
I tricked everyone into thinking I HACK and got BANNED..
Minecraft but Hackers beat the game for me
Introduction to Hacking | How to Start Hacking
I secretly spectated HACKERS in Roblox Bedwars..
Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoC
19 Video Games That ROAST Hackers
HACKERS STOLE LANA?! 😨 Dress To Impress LANA LORE UPDATE?! #dresstoimpress #dti
How to CLAIM a FREE SKIN in FORTNITE
Hacking 🔥 Expectation vs Reality | Coding Status For WhatsApp
This is how Hackers can *OWN YOU* with just a link!
This Roblox Video Made Me Cry...
Комментарии
 0:02:23
0:02:23
 0:02:56
0:02:56
 0:07:45
0:07:45
 0:09:13
0:09:13
 0:10:02
0:10:02
 0:05:42
0:05:42
 0:08:07
0:08:07
 0:08:07
0:08:07
 0:01:01
0:01:01
 0:04:31
0:04:31
 0:05:03
0:05:03
 0:08:05
0:08:05
 0:09:00
0:09:00
 0:08:04
0:08:04
 0:14:05
0:14:05
 0:06:55
0:06:55
 0:08:25
0:08:25
 0:00:34
0:00:34
 0:08:32
0:08:32
 0:00:13
0:00:13
 0:00:24
0:00:24
 0:00:31
0:00:31
 0:08:05
0:08:05
 0:10:34
0:10:34