filmov
tv
A Dangerous Crypto Scam is Targeting YouTubers
Показать описание
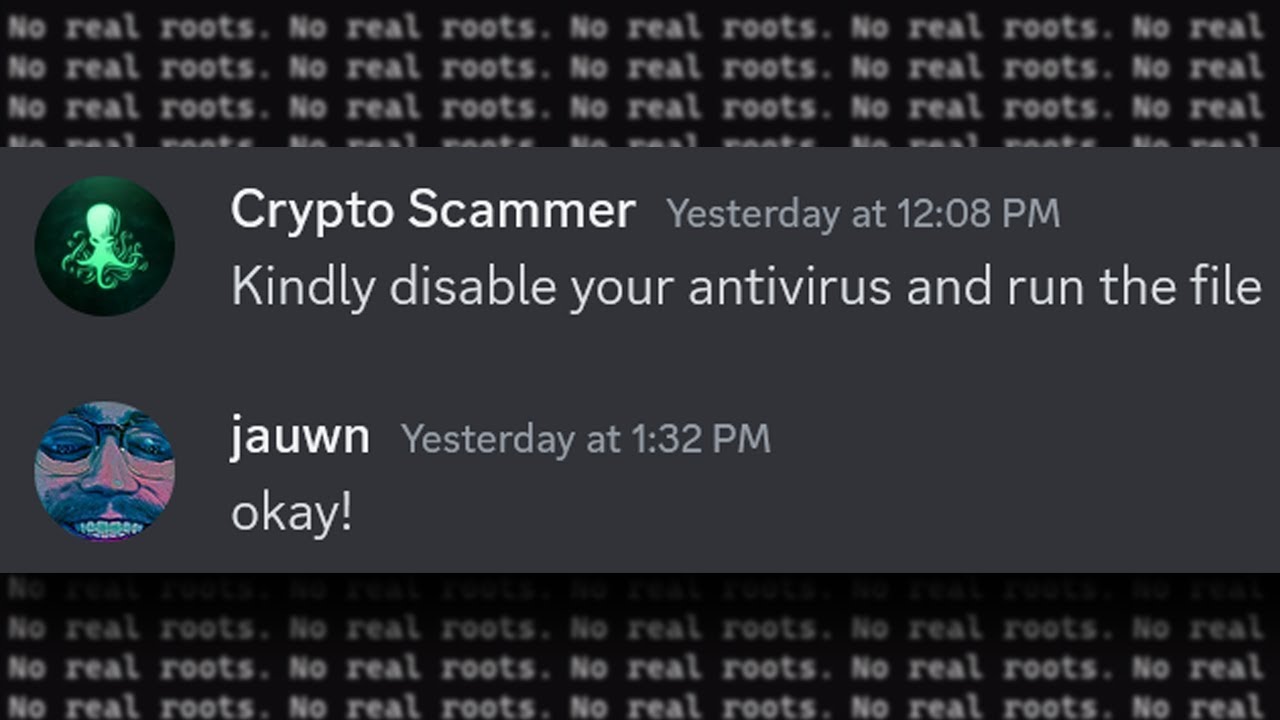
Yesterday, a pretty blatant #crypto #scam reached out to me via Discord to coordinate a promotional video. Obviously, I would never do a promotional video for a crypto game, so I decided to have a little bit of fun with them. However, what I uncovered was instead a very sophisticated and scary piece of malware.
I decided to perform a little bit of malware analysis on this and break their scam down to help raise awareness. While a scam like this may seem obvious if you have a strong technical background, this specific example was much more convincing than some of the others I've seen in the past.
They asked for a promotional video, I delivered!
Thanks for watching!
Subscribe:
Buy me a Coffee:
Follow me on Twitter:
Join our Discord!:
I decided to perform a little bit of malware analysis on this and break their scam down to help raise awareness. While a scam like this may seem obvious if you have a strong technical background, this specific example was much more convincing than some of the others I've seen in the past.
They asked for a promotional video, I delivered!
Thanks for watching!
Subscribe:
Buy me a Coffee:
Follow me on Twitter:
Join our Discord!:
A Dangerous Crypto Scam is Targeting YouTubers
The Most Dangerous Crypto Scam in the World
The Most Dangerous Crypto Scam: Victims Speak Out
TAPSWAP CODE:The most DANGEROUS crypto scams you SHOULD know about! #tapswap #tapcoin
The most DANGEROUS crypto scams you SHOULD know about
Why Bitcoin is a Scam
Free 0.31 BTC Promo Code XGRANT Scam Using Elon Musk EXPOSED! Vexorabit Review
Tapswap Task Code - The most Dangerous crypto scams
I Trusted the US Treasury - Here’s What Happened
Code TapSwap | The Most DANGEROUS Crypto Scams You SHOULD Know About! |
3 Crypto Scams YOU WILL Fall For & How To Avoid
The Discord Bitcoin Scam: This Never-Ending Crypto Exchange Scam is Dangerous
Crypto is a Giant Ponzi Scheme, Here's Why
Elon Musk: Why I HATE Bitcoin?
12 July Tapswap Code Today | The most DANGEROUS crypto scams you SHOULD know about!
ANDREW TATE SAYS THIS ABOUT CRYPTO FUTURE #shorts
Most Dangerous Crypto Scam Yet in 2020
How Crypto Scammed The World
This Guy Made 114 Crypto SCAMS In 1 Month...
Warren Buffett Exposes Bitcoin
Is Bitcoin a Scam? Peter Zeihan Tells All
The most dangerous crypto MEV scam
Yocoja.com Crypto Scam Review: Is It a Safe Investment or a Risky Fraud?
Edward Snowden | 'The Future of Crypto Is Not What It Seems'
Комментарии
 0:11:11
0:11:11
 0:13:57
0:13:57
 0:11:11
0:11:11
 0:00:22
0:00:22
 0:00:29
0:00:29
 0:07:40
0:07:40
 0:02:08
0:02:08
 0:03:02
0:03:02
 0:00:34
0:00:34
 0:01:10
0:01:10
 0:08:55
0:08:55
 0:11:11
0:11:11
 0:22:40
0:22:40
 0:00:35
0:00:35
 0:01:03
0:01:03
 0:00:34
0:00:34
 0:10:51
0:10:51
 0:18:04
0:18:04
 0:00:59
0:00:59
 0:15:52
0:15:52
 0:00:39
0:00:39
 0:09:59
0:09:59
 0:08:48
0:08:48
 0:09:07
0:09:07