filmov
tv
Key and Keyless transposition techniques | Cryptography and Network Security

Показать описание
In this enlightening video, we delve into the dynamic world of Key and Keyless Transposition Techniques in Cryptography and Network Security. Join us on this exploration as we uncover the principles, mechanisms, and applications of both key-based and keyless transposition cipher algorithms, shedding light on their pivotal roles in securing data transmission. 🔐💻
👉 Key Topics Explored:
Introduction to Key and Keyless Transposition Techniques: Understanding the fundamental concepts and distinctions between key-based and keyless transposition ciphers.
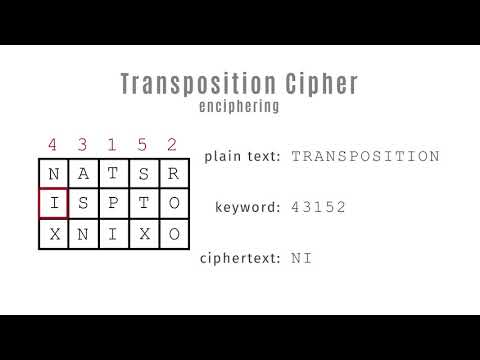
Key-based Transposition Algorithms: Exploring encryption and decryption processes using a key for rearranging plaintext.
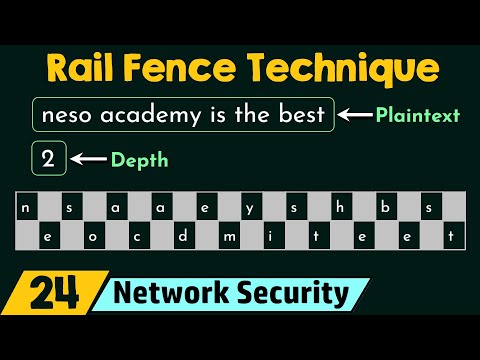
Keyless Transposition Algorithms: Examining methods that rearrange plaintext without the use of a key and their applications in network security.
🚀 Why Watch This Video?
Whether you're a cryptography enthusiast, a student exploring network security intricacies, or an IT professional interested in diverse encryption methods, this video provides valuable insights into both key and keyless transposition techniques and their crucial roles in ensuring secure communication.
🔍 What You'll Learn:
The distinctions between key-based and keyless transposition techniques.
A detailed exploration of algorithms for both types of transposition ciphers.
Real-world considerations for using these techniques in network security.
👉 Download Ekeeda Application & Learn from the best professors with 10+ years of experience.
Subscribe to a Course or Start a Free Trial of Package.
✤ Download the Ekeeda - Learning App for Engineering Courses App here:
✤ For More Such Classes Get Subscription Advantage:
👉 Key Topics Explored:
Introduction to Key and Keyless Transposition Techniques: Understanding the fundamental concepts and distinctions between key-based and keyless transposition ciphers.
Key-based Transposition Algorithms: Exploring encryption and decryption processes using a key for rearranging plaintext.
Keyless Transposition Algorithms: Examining methods that rearrange plaintext without the use of a key and their applications in network security.
🚀 Why Watch This Video?
Whether you're a cryptography enthusiast, a student exploring network security intricacies, or an IT professional interested in diverse encryption methods, this video provides valuable insights into both key and keyless transposition techniques and their crucial roles in ensuring secure communication.
🔍 What You'll Learn:
The distinctions between key-based and keyless transposition techniques.
A detailed exploration of algorithms for both types of transposition ciphers.
Real-world considerations for using these techniques in network security.
👉 Download Ekeeda Application & Learn from the best professors with 10+ years of experience.
Subscribe to a Course or Start a Free Trial of Package.
✤ Download the Ekeeda - Learning App for Engineering Courses App here:
✤ For More Such Classes Get Subscription Advantage:
 0:12:54
0:12:54
 0:02:26
0:02:26
 0:12:09
0:12:09
 0:06:31
0:06:31
 0:10:49
0:10:49
 0:01:14
0:01:14
 0:08:15
0:08:15
 0:05:45
0:05:45
 0:19:12
0:19:12
 0:09:59
0:09:59
 0:22:33
0:22:33
 0:05:14
0:05:14
 0:14:48
0:14:48
 0:06:46
0:06:46
 0:48:18
0:48:18
 0:02:37
0:02:37
 0:03:55
0:03:55
 0:08:47
0:08:47
 0:05:35
0:05:35
 0:39:30
0:39:30
 0:03:50
0:03:50
 0:10:16
0:10:16
 0:05:56
0:05:56
 0:05:34
0:05:34