filmov
tv
Ultimate MikroTik Wireguard Site-to-Site Guide

Показать описание
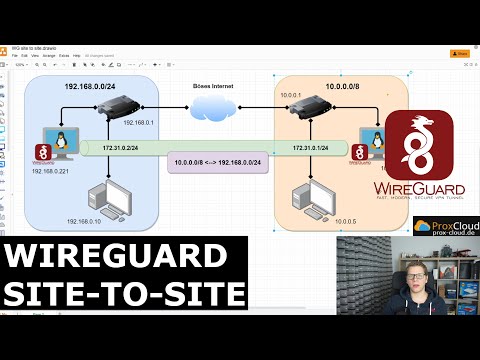
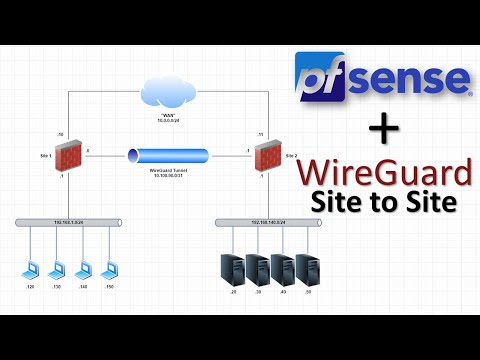
Hey there, hope you are having a wonderful day/evening. Many people have reached out to me about Wireguard, asking me to make videos about X or Y scenarios. So I decided to merge all those questions into one singular video where we will be configuring Wireguard for Site-to-Site VPN use cases and how we can setup wireguard to route between sites. It is an amazing protocol and I highly suggest reading the white paper about it. More reference material in the pinned comment below.
❗Help the channel grow by subscribing if you aren't subscribed already! A like is also very appreciated and feel free to leave a comment about what you liked or disliked in the video and what else you would like to see from me :) 👊❗
Timestamps:
📕00:00 - Introduction
📕00:46 - Wireguard Overview
📕03:11 - Lab Overview
📕06:27 - Configure Server (Site A)
📕10:23 - Configure Remote Site (Site B)
📕13:18 - MikroTik WG Quirks
📕18:43 - Configuring Remote Site (Site C)
📕24:43 - Access between Remote Sites
Support the Channel:
Social Media:
MTCRE Playlist:
MTCNA Playlist:
Thanks again for watching
❗Help the channel grow by subscribing if you aren't subscribed already! A like is also very appreciated and feel free to leave a comment about what you liked or disliked in the video and what else you would like to see from me :) 👊❗
Timestamps:
📕00:00 - Introduction
📕00:46 - Wireguard Overview
📕03:11 - Lab Overview
📕06:27 - Configure Server (Site A)
📕10:23 - Configure Remote Site (Site B)
📕13:18 - MikroTik WG Quirks
📕18:43 - Configuring Remote Site (Site C)
📕24:43 - Access between Remote Sites
Support the Channel:
Social Media:
MTCRE Playlist:
MTCNA Playlist:
Thanks again for watching
Комментарии
 0:28:29
0:28:29
 0:02:48
0:02:48
 0:07:29
0:07:29
 0:14:11
0:14:11
 0:25:55
0:25:55
 0:25:13
0:25:13
 0:16:10
0:16:10
 0:15:43
0:15:43
 0:00:24
0:00:24
 0:18:53
0:18:53
 0:00:12
0:00:12
 0:04:50
0:04:50
 0:00:40
0:00:40
 0:11:40
0:11:40
 0:45:07
0:45:07
 0:03:05
0:03:05
 0:18:15
0:18:15
 0:00:40
0:00:40
![[TUT] MikroTik -](https://i.ytimg.com/vi/bEfUWz6FlYg/hqdefault.jpg) 0:21:09
0:21:09
![[How To] Configure](https://i.ytimg.com/vi/ah0Kkkqqfcg/hqdefault.jpg) 0:20:32
0:20:32
 0:19:36
0:19:36
 0:12:31
0:12:31
 0:10:42
0:10:42
 0:19:40
0:19:40