filmov
tv
Crypto: Caesar Cipher explained | Java implementation

Показать описание
This video explains the Caesar Cipher (cryptosystem) and walks through the process of implementing it in Java.
One of the simplest examples of a substitution cipher is the Caesar cipher, which is said to have been used by Julius Caesar to communicate with his army. Caesar is considered to be one of the first persons to have ever employed encryption for the sake of securing messages. Caesar decided that shifting each letter in the message would be his standard algorithm, and so he informed all of his generals of his decision, and was then able to send them secured messages.
One of the simplest examples of a substitution cipher is the Caesar cipher, which is said to have been used by Julius Caesar to communicate with his army. Caesar is considered to be one of the first persons to have ever employed encryption for the sake of securing messages. Caesar decided that shifting each letter in the message would be his standard algorithm, and so he informed all of his generals of his decision, and was then able to send them secured messages.
Caesar Cipher (Part 1)
How to Use the Caesar (Shift) Cipher
Symmetric Key Cryptography: The Caesar Cipher
Cryptograph: Substitution Cipher (Caesar Cipher)
SHIFT CIPHER / JULIUS CAESAR CIPHER EXPLAINED!!!
The Science of Codes: An Intro to Cryptography
Applied Cryptography: Caesar Cipher Example 1 (2/3)
Introduction to Cryptography - Caesar Cipher
Crack the Code: The Caesar Cipher
Cryptography | Intro to Encryption | Caesar Cipher Code Example
Caesar Cipher Encryption & Decryption | Substitution Cipher Technique
Caesar Cipher in network security | Shift Cipher in cryptography | Caesar Cipher example
Crypto: Caesar Cipher explained | Java implementation
Cryptography: Crash Course Computer Science #33
Crack the Code Caesar Cipher Explained! #facts #arandomhashtag
Applied Cryptography: Caesar Cipher Example 1 (1/3)
Break a Caesar Cipher – One of the Oldest Known Encryption Method of the Ancient World
Beaufort Cipher Explained and Broken
Caesar Cipher in Under 60 Seconds
Introduction to cryptography - Caesar cipher
Caesar Cipher in Cryptography | Information Security
Vigenere CIpher
Secret Codes: A History of Cryptography (Part 1)
Applied Cryptography: Caesar Cipher Example 1 (3/3)
Комментарии
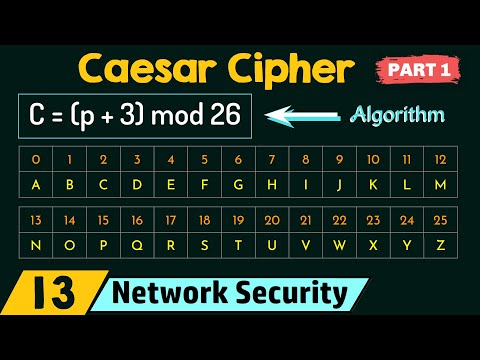 0:13:23
0:13:23
 0:02:06
0:02:06
 0:07:13
0:07:13
 0:09:40
0:09:40
 0:10:34
0:10:34
 0:08:21
0:08:21
 0:06:44
0:06:44
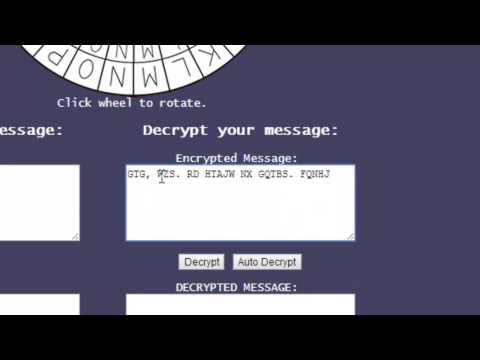 0:07:51
0:07:51
 0:09:35
0:09:35
 0:12:40
0:12:40
 0:05:13
0:05:13
 0:04:30
0:04:30
 0:40:10
0:40:10
 0:12:33
0:12:33
 0:00:45
0:00:45
 0:07:56
0:07:56
 0:07:54
0:07:54
 0:20:56
0:20:56
 0:00:57
0:00:57
 0:08:49
0:08:49
 0:15:29
0:15:29
 0:02:02
0:02:02
 0:12:09
0:12:09
 0:07:43
0:07:43