filmov
tv
Lecture 10: Multiple Encryption and Brute-Force Attacks by Christof Paar

Показать описание
Lecture 10: Multiple Encryption and Brute-Force Attacks by Christof Paar
Multiple Encryption and Triple DES
INS: Unit-3 Multiple Encryption
The Security of Multiple Encryption in the Ideal Cipher Model
Computer Architecture - Lecture 10: Memory Controllers (Fall 2024)
Lecture 9: Security and Cryptography (2020)
Lecture 8: Advanced Encryption Standard (AES) by Christof Paar
CIS27 Unit 10 Lecture: Encryption
Lecture 14 and 15 | Double DES, Triple DES and Advanced Encryption Standard | Sridhar Iyer
CIS27 Unit 10 Lecture: Encryption, Hash, Digital Signature and Certificates
Ins Chap -3 Multiple Encryption and Modes
CSS322, Lecture 21, 25 Jan 2013 - Key Management with Symmetric Encryption
Symmetric Key Encryption and Authentiction (ITS335, Lecture 4, 2013)
Lec-114: What is RAID? RAID 0, RAID 1, RAID 4, RAID 5, RAID 6, Nested RAID 10 Explained
Computer Networks Lecture 32: Public Key Encryption
Chapter5, part 2, Multiple Encryption and Brute-Force Attacks (Arabic)
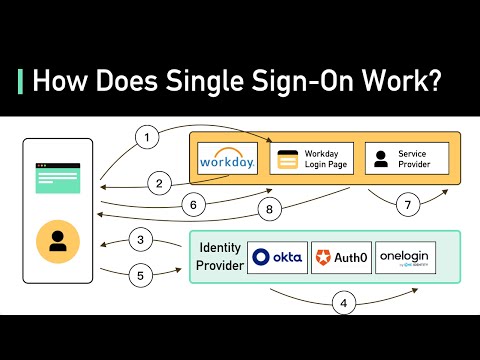
What Is Single Sign-on (SSO)? How It Works
CppCon 2015: Jens Weller “An Overview on Encryption in C++'
Introduction to Encryption Techniques (CSS322, Lecture 2, 2013)
File Encryption - Applied Cryptography
Blockchain In 7 Minutes | What Is Blockchain | Blockchain Explained|How Blockchain Works|Simplilearn
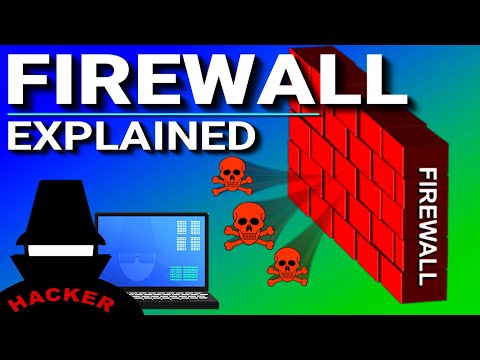
What is a Firewall?
CIS27 Unit 10 Lecture: Encryption, Hash and Certificates
How exactly does binary code work? - José Américo N L F de Freitas
Комментарии
 1:27:48
1:27:48
 0:20:54
0:20:54
 0:11:51
0:11:51
 0:18:57
0:18:57
 2:30:54
2:30:54
 1:01:00
1:01:00
 1:33:19
1:33:19
 1:00:20
1:00:20
 1:36:59
1:36:59
 1:42:18
1:42:18
 0:30:04
0:30:04
 1:12:39
1:12:39
 1:21:34
1:21:34
 0:14:35
0:14:35
 1:28:14
1:28:14
 1:08:10
1:08:10
 0:04:54
0:04:54
 0:44:35
0:44:35
 1:21:39
1:21:39
 0:02:33
0:02:33
 0:07:03
0:07:03
 0:06:26
0:06:26
 1:31:36
1:31:36
 0:04:40
0:04:40