filmov
tv
Using Yara & Strelka to Identify & Detect Malware

Показать описание
Speakers: Paul Hutelmyer (Target, US), Derek Thomas (Target, US)
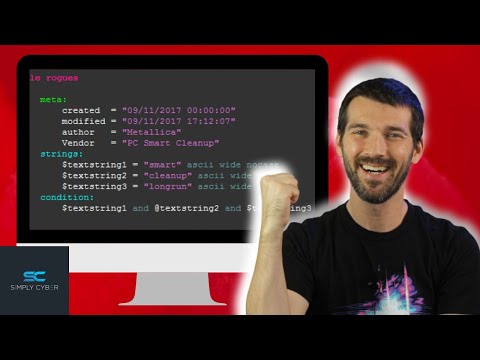
Adversaries try as much as possible to blend in with behavior that appears normal. However, their operations result in malicious activity, and therefore must at some point deviate from normalcy and develop specific patterns which can be identified over time. This workshop will focus on identifying, collecting, and detecting malware, using the Open Source projects "Yara" and "Strelka". The goal of the training is that the audience will be able to identify malware of interest to them, and develop enterprise level detection based on their own research.
About the Speakers
Paul Hutelmyer is a principal engineer with Target Corporation.
Derek Thomas is a lead information security analyst on Target Corporation’s Cyber Threat Intelligence (CTI) team in Brooklyn Park, Minnesota. After graduating college, Derek joined the US Army as an active duty intelligence officer where he developed a passion for intelligence analysis. After the military he worked as a contractor in Washington D.C supporting the FBI Cyber Division as a cyber-intelligence analyst pursuing financially motivated cybercriminals. Derek has since earned the PMP, GSEC, GCIH, GCIA, GPEN, and OSCP certifications and his Master’s in homeland security from Penn State. He joined Target’s CTI team in March 2018 and currently lives in the suburbs of Minneapolis with his wife, son, and golden retriever.
Adversaries try as much as possible to blend in with behavior that appears normal. However, their operations result in malicious activity, and therefore must at some point deviate from normalcy and develop specific patterns which can be identified over time. This workshop will focus on identifying, collecting, and detecting malware, using the Open Source projects "Yara" and "Strelka". The goal of the training is that the audience will be able to identify malware of interest to them, and develop enterprise level detection based on their own research.
About the Speakers
Paul Hutelmyer is a principal engineer with Target Corporation.
Derek Thomas is a lead information security analyst on Target Corporation’s Cyber Threat Intelligence (CTI) team in Brooklyn Park, Minnesota. After graduating college, Derek joined the US Army as an active duty intelligence officer where he developed a passion for intelligence analysis. After the military he worked as a contractor in Washington D.C supporting the FBI Cyber Division as a cyber-intelligence analyst pursuing financially motivated cybercriminals. Derek has since earned the PMP, GSEC, GCIH, GCIA, GPEN, and OSCP certifications and his Master’s in homeland security from Penn State. He joined Target’s CTI team in March 2018 and currently lives in the suburbs of Minneapolis with his wife, son, and golden retriever.
Комментарии
 1:41:55
1:41:55
 0:25:21
0:25:21
 0:05:43
0:05:43
 0:14:15
0:14:15
 0:09:49
0:09:49
 0:04:18
0:04:18
 0:25:18
0:25:18
 0:25:58
0:25:58
 0:17:57
0:17:57
 0:03:37
0:03:37
 0:26:33
0:26:33
 0:02:17
0:02:17
 0:07:55
0:07:55
 0:07:17
0:07:17
 0:10:00
0:10:00
 0:01:38
0:01:38
 0:25:53
0:25:53
 0:07:55
0:07:55
 0:03:04
0:03:04
 0:24:05
0:24:05
 0:00:20
0:00:20
 0:35:35
0:35:35
 1:12:02
1:12:02
 0:16:46
0:16:46