filmov
tv
Leaking Values with printf (Format String Vuln) - Search Engine - [Intigriti 1337UP LIVE CTF 2022]

Показать описание
2nd Pwn video from @intigriti 1337UP LIVE CTF 2022: "Search Engine". We'll take a quick look at format string vulnerabilities (printf) to see how we can leak values off the stack and make a PwnTools fuzzing script to automate the process. Write-ups/tutorials aimed at beginners - Hope you enjoy 🙂 #BinaryExploitation #BufferOverflow #BinExp #RE #Pwn #PwnTools
↢Social Media↣
↢Intigriti↣
↢Resources↣
↢Chapters↣
Start: 0:00
Basic File Checks: 0:22
Disassemble with Ghidra: 0:59
Dynamic Analysis with GDB-PwnDbg: 3:12
Leaking Values off the Stack with printf(): 4:34
PwnTools Script (Fuzzing): 6:25
End: 9:07
↢Social Media↣
↢Intigriti↣
↢Resources↣
↢Chapters↣
Start: 0:00
Basic File Checks: 0:22
Disassemble with Ghidra: 0:59
Dynamic Analysis with GDB-PwnDbg: 3:12
Leaking Values off the Stack with printf(): 4:34
PwnTools Script (Fuzzing): 6:25
End: 9:07
Leaking Values with printf (Format String Vuln) - Search Engine - [Intigriti 1337UP LIVE CTF 2022]
Format String printf Vulnerabilities (PicoCTF 2022 #46 'flag-leak')
A simple Format String exploit example - bin 0x11
7: Format String Vulnerabilities (printf) - Buffer Overflows - Intro to Binary Exploitation (Pwn)
Leaking the Stack / Printf Format Vulnerability | echooo [32] picoCTF 2018
printf leak - CTF Cookbook - pwn
Format String to dump binary and gain RCE - 33c3ctf ESPR (pwn 150)
Format String Exploits - Writing Data
9: Overwriting Global Offset Table (GOT) Entries with printf() - Intro to Binary Exploitation (Pwn)
10: Bypassing Stack Canaries (leak + write) - Buffer Overflows - Intro to Binary Exploitation (Pwn)
Format String Vulnerabilities – The Impact Of A Leaky Program
Format String Exploit and overwrite the Global Offset Table - bin 0x13
Triple printf exploit for libc leak and one_gadget - LACTF2023 - pwn/rickroll
Introduction to format string vulnerabilities
Exploiting Format String vulnerabilities tutorial - pwn106 - PWN101 | TryHackMe
printf exploit in the data section - UTCTF 2023 - pwn/printfail
you need to stop using print debugging (do THIS instead)
8: Leak PIE (bypass) and Lib-C (ret2system) - Buffer Overflows - Intro to Binary Exploitation (Pwn)
Format String Exploit Troubleshooting Over Twitter - bin 0x11 b
Format String Exploits - Introduction
Format String Vulnerability: Leak Content from the Stack
pwn/rut-roh-relro - LACTF2023 - Challenge Writeup (printf libc leak + printf to stack ROP)
Leet Test [easy]: HackTheBox Pwn Challenge (format string write exploit with pwntools)
Why Printf is Magically Breaking Your Program.
Комментарии
 0:09:31
0:09:31
 0:19:44
0:19:44
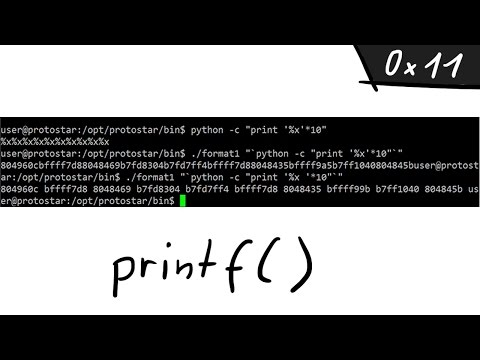 0:10:01
0:10:01
 0:18:32
0:18:32
 0:13:01
0:13:01
 0:04:49
0:04:49
 0:13:25
0:13:25
 0:17:05
0:17:05
 0:26:56
0:26:56
 0:14:49
0:14:49
 1:03:32
1:03:32
 0:11:58
0:11:58
 0:20:04
0:20:04
 0:11:21
0:11:21
 0:36:24
0:36:24
 0:20:45
0:20:45
 0:07:07
0:07:07
 0:31:12
0:31:12
 0:24:59
0:24:59
 0:09:47
0:09:47
 0:10:44
0:10:44
 0:13:31
0:13:31
![Leet Test [easy]:](https://i.ytimg.com/vi/NOY_dc2fRbU/hqdefault.jpg) 1:01:15
1:01:15
 0:08:06
0:08:06