filmov
tv
Exploiting Format String vulnerabilities tutorial - pwn106 - PWN101 | TryHackMe

Показать описание
Understanding the format string vulnerability step by step in this thorough tutorial explaining its very foundations, the underlying concepts. How do format string vulnerabilities happen, why and how can we abuse them. Format String vulnerabilities allow an attacker to both leak memory and corrupt it by writing arbitrary values. In this video we will learn how to leak memory by abusing a Format String vulnerability, aside from understanding what is happening internally. Step-by-step tutorial solving pwn106 from PWN101 binary exploitation room on TryHackMe.
Golden Format String papers and posts:
My post about 32-bit format string:
00:00 - Intro
00:12 - Checking binary protections
00:43 - Executing the binary
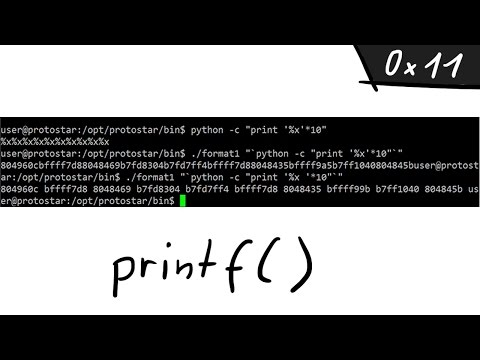
01:16 - Spotting the vuln: Format String
01:48 - Format String vulnerability
02:41 - Best Format String exploitation resources
04:53 - Explaining Format String vulnerability
07:25 - Playing with an example
07:54 - Testing and understanding the vulnerability
11:35 - Debugging the vulnerability
12:51 - Calling convention for 64-bit architectures
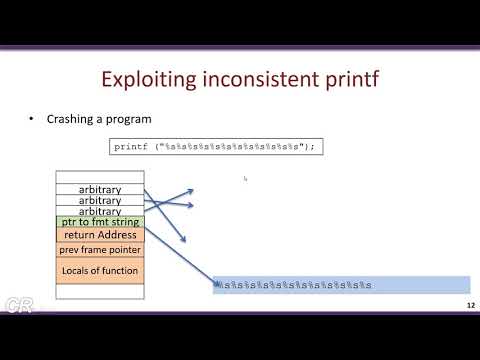
14:00 - Understanding the vulnerability
18:30 - Format specifiers and sub-specifiers
19:45 - Debugging again
22:07 - Recap
23:23 - Positional argument
25:50 - Leaking the toy secret
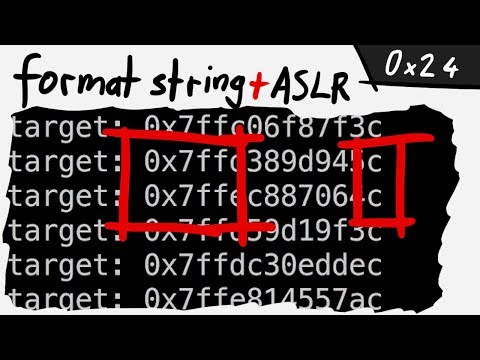
26:59 - Differences 32 and 64 bits
27:30 - Disassembling the binary
27:55 - Spotting the vulnerability
29:23 - Writing the exploit
31:50 - Spotting the position of the flag
32:30 - Exploiting locally
34:20 - Exploiting remotely
34:55 - Reading the flag
35:15 - Outro[*]
Exploit code, not people.
Twitter: @Razvieu
Did you like the video? Found it useful? If you feel like lending a hand consider buying me a coffee (or three ☕), it really helps!
*Outro track: Etsu - Selcouth
GG
Golden Format String papers and posts:
My post about 32-bit format string:
00:00 - Intro
00:12 - Checking binary protections
00:43 - Executing the binary
01:16 - Spotting the vuln: Format String
01:48 - Format String vulnerability
02:41 - Best Format String exploitation resources
04:53 - Explaining Format String vulnerability
07:25 - Playing with an example
07:54 - Testing and understanding the vulnerability
11:35 - Debugging the vulnerability
12:51 - Calling convention for 64-bit architectures
14:00 - Understanding the vulnerability
18:30 - Format specifiers and sub-specifiers
19:45 - Debugging again
22:07 - Recap
23:23 - Positional argument
25:50 - Leaking the toy secret
26:59 - Differences 32 and 64 bits
27:30 - Disassembling the binary
27:55 - Spotting the vulnerability
29:23 - Writing the exploit
31:50 - Spotting the position of the flag
32:30 - Exploiting locally
34:20 - Exploiting remotely
34:55 - Reading the flag
35:15 - Outro[*]
Exploit code, not people.
Twitter: @Razvieu
Did you like the video? Found it useful? If you feel like lending a hand consider buying me a coffee (or three ☕), it really helps!
*Outro track: Etsu - Selcouth
GG
Комментарии
 0:10:01
0:10:01
 0:36:24
0:36:24
 0:11:58
0:11:58
 0:18:32
0:18:32
 0:19:44
0:19:44
 0:09:47
0:09:47
 0:07:41
0:07:41
 0:11:11
0:11:11
 1:02:32
1:02:32
 0:13:02
0:13:02
 0:02:01
0:02:01
 0:13:25
0:13:25
 0:25:40
0:25:40
 0:17:42
0:17:42
 0:25:24
0:25:24
 0:05:47
0:05:47
 0:17:05
0:17:05
 0:00:57
0:00:57
 0:13:45
0:13:45
 0:24:59
0:24:59
 0:27:27
0:27:27
 0:11:53
0:11:53
 0:36:48
0:36:48
 0:22:51
0:22:51