filmov
tv
NTFS file system explained: understanding resident and non-resident files - Computer forensics

Показать описание
The goal of the Computer forensics course is to teach you how to collect evidence in case of an incident and to investigate how the intruders came in, what data they have stolen, if they have harmed your system.
In addition we will give you advice on what you can do to block the next attack.
The Computer forensics course will cover:
- Recovering NTFS file system and looking for evidence
- Recovering FAT16 and FAT32 file system
- Acquiring saved passwords from the password managers of browsers
- Browser history and cache file recovery to investigate the users’ internet usage
- Getting the content (e.g. emails, contacts) from an encrypted Outlook PST file
- Recovery of Exchange MDB, Active Directory NTDS.DIT and similar files
- ZIP file recovery
- RAM analysis of Windows and Linux servers with Volatility
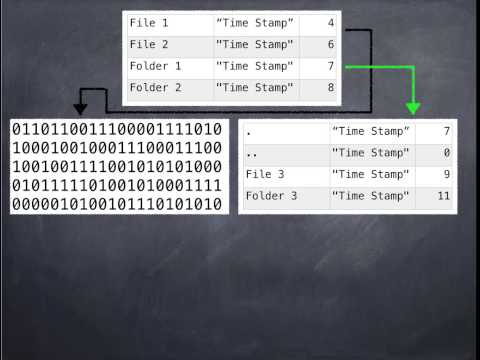
IN THIS TUTORIAL of the Computer forensics course you will learn the inner workings of the NTFS file system to be able to recover files and look for evidence later.
For this we will cover:
01:21 Role of the resident files and how to retrieve them
24:36 Non-resident files in NTFS and their role in the file system
Please note that this computer forensics tutorial is for educational purposes only.
SUBSCRIBE NOW FOR NEW FREE IT TUTORIALS!
SUBSCRIBE TO OUR EMAIL LIST!
FOLLOW US!
----------------------------------------------------------------------------------------------------------
Комментарии
 0:11:05
0:11:05
 0:08:01
0:08:01
 0:32:13
0:32:13
 0:44:30
0:44:30
 0:14:16
0:14:16
 0:11:45
0:11:45
 0:12:03
0:12:03
 0:05:46
0:05:46
 0:00:49
0:00:49
 0:34:32
0:34:32
 0:21:56
0:21:56
 0:01:14
0:01:14
 0:07:54
0:07:54
 0:11:37
0:11:37
 0:02:44
0:02:44
 0:26:51
0:26:51
 0:08:39
0:08:39
 0:06:16
0:06:16
 0:02:55
0:02:55
 0:03:32
0:03:32
 0:04:28
0:04:28
 0:06:04
0:06:04
 0:02:53
0:02:53
 0:16:03
0:16:03