filmov
tv
How To Use Proxychains In Kali Linux

Показать описание
Proxychains is a tool that allows you to run applications through a proxy server in Kali Linux. Here's a step-by-step guide on how to use Proxychains:
Step 1: Install Proxychains
Proxychains is not installed by default in Kali Linux, so you need to install it first. Open a terminal and run the following command:
sudo apt-get update
sudo apt-get install proxychains
Step 2: Configure Proxychains
Once Proxychains is installed, you need to configure it to use your desired proxy server. Open the Proxychains configuration file using a text editor:
Inside the configuration file, you'll see some commented out examples. Scroll down and find the [ProxyList] section. Uncomment one of the examples or add your own proxy server by providing the IP address, port number, and type of proxy (e.g., SOCKS4, SOCKS5, HTTP).
For example, to use a SOCKS5 proxy server at IP address 127.0.0.1 and port 1080, remove the "#" symbol from the beginning of the line:
# socks4 127.0.0.1 9050
socks5 127.0.0.1 1080
Save and exit the configuration file (in Nano, press Ctrl+X, then Y, and Enter).
Step 3: Use Proxychains
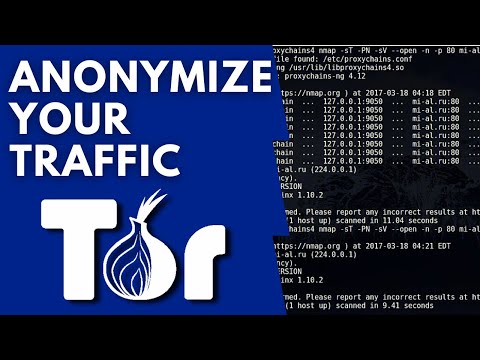
Now you can run applications through the configured proxy server using Proxychains. Open a terminal and type proxychains followed by the command you want to run.
For example, to run the nmap command through the proxy server, you would use:
proxychains nmap -sT -p 80 target_ip
This will run nmap through the configured proxy server and scan the target IP address using TCP SYN scanning on port 80.
Note: Proxychains will only work with applications that are compatible with proxy connections. Not all applications support proxies, so make sure to check the documentation or verify if the application you want to use is proxy-aware.
That's it! You've successfully configured and used Proxychains in Kali Linux. Remember to respect any legal and ethical guidelines when using proxies and conducting network activities.
Disclaimer: All demonstrations in this video are conducted on authorized systems with explicit permission. No support for illegal activities. Ethical hacking means responsible vulnerability discovery. Misusing techniques for unauthorized or malicious purposes is strictly discouraged. Exercise sound judgment and respect others' security and privacy. Seek permission for any hacking-related activities. Subscribe for more ethical hacking content!
Step 1: Install Proxychains
Proxychains is not installed by default in Kali Linux, so you need to install it first. Open a terminal and run the following command:
sudo apt-get update
sudo apt-get install proxychains
Step 2: Configure Proxychains
Once Proxychains is installed, you need to configure it to use your desired proxy server. Open the Proxychains configuration file using a text editor:
Inside the configuration file, you'll see some commented out examples. Scroll down and find the [ProxyList] section. Uncomment one of the examples or add your own proxy server by providing the IP address, port number, and type of proxy (e.g., SOCKS4, SOCKS5, HTTP).
For example, to use a SOCKS5 proxy server at IP address 127.0.0.1 and port 1080, remove the "#" symbol from the beginning of the line:
# socks4 127.0.0.1 9050
socks5 127.0.0.1 1080
Save and exit the configuration file (in Nano, press Ctrl+X, then Y, and Enter).
Step 3: Use Proxychains
Now you can run applications through the configured proxy server using Proxychains. Open a terminal and type proxychains followed by the command you want to run.
For example, to run the nmap command through the proxy server, you would use:
proxychains nmap -sT -p 80 target_ip
This will run nmap through the configured proxy server and scan the target IP address using TCP SYN scanning on port 80.
Note: Proxychains will only work with applications that are compatible with proxy connections. Not all applications support proxies, so make sure to check the documentation or verify if the application you want to use is proxy-aware.
That's it! You've successfully configured and used Proxychains in Kali Linux. Remember to respect any legal and ethical guidelines when using proxies and conducting network activities.
Disclaimer: All demonstrations in this video are conducted on authorized systems with explicit permission. No support for illegal activities. Ethical hacking means responsible vulnerability discovery. Misusing techniques for unauthorized or malicious purposes is strictly discouraged. Exercise sound judgment and respect others' security and privacy. Seek permission for any hacking-related activities. Subscribe for more ethical hacking content!
Комментарии
 0:12:48
0:12:48
 0:12:49
0:12:49
 0:08:58
0:08:58
 0:07:54
0:07:54
 0:12:27
0:12:27
 0:09:43
0:09:43
 0:53:16
0:53:16
 0:04:34
0:04:34
 0:10:59
0:10:59
 0:14:05
0:14:05
 0:05:27
0:05:27
 0:07:44
0:07:44
 0:02:54
0:02:54
 0:11:12
0:11:12
 0:10:49
0:10:49
 0:04:35
0:04:35
 0:11:38
0:11:38
 0:04:31
0:04:31
 0:29:36
0:29:36
 0:00:28
0:00:28
 0:03:48
0:03:48
 0:06:31
0:06:31
 0:10:48
0:10:48
 0:04:26
0:04:26