filmov
tv
What is Single Sign-on (SSO) System ? How it Works? | Example | InterviewDOT

Показать описание
Tamil What is Single Sign-on (SSO) System ? How it Works? | Example | InterviewDOT
Single sign-on ( SSO , sometimes also translated as " single sign-on ") means that after a single authentication at a workstation , a user can access all computers and services for which he is locally authorized ( authorized ) from the same workstation, without having to log on to the individual services each time. If the user changes workplaces, authentication and local authorization become obsolete.
This possibility has certain advantages for the user, especially with portals . Within portals, it is also possible for the identity of the registered user to be passed on to the layers constituting the portal, without this having been made known to the user himself.
An SSO system relies on a user always having exactly one physical identity (which is copied from the real world). Within a system, however, the user can be saved as an individual under different user names (logical identity). These are merged and linked in the SSO system - this makes it impossible to appear under a pseudonym (without disclosing the other user IDs).
The aim of single sign-on is that the user only has to identify himself once using a single authentication procedure (e.g. by entering a password ). The SSO mechanism then takes over the task of authenticating the user (confirming the identified identity). The use of SSO is forbidden if a user acts on behalf of different people who should not be linked.
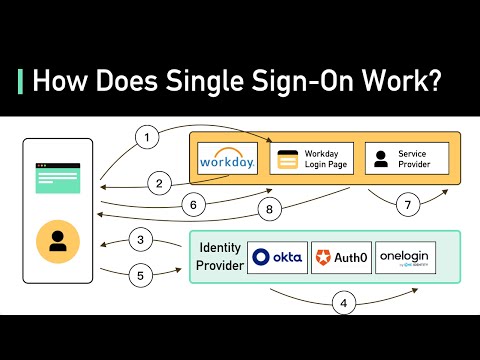
Single sign-on (SSO) enables access to services, applications or resources through a single authentication process. SSO replaces individual registration procedures with different user data and uses a comprehensive identity of the user.
Single sign-on, abbreviated SSO, means single sign-on and describes a procedure with which a user receives access to several services and resources after a single authentication . This eliminates the need for separate registrations for the different services. The user has an identity to the SSO system that is also valid for other services. The SSO system takes on the task of confirming this identity to the various services and authenticating the user for all services and applications for which access is to be granted.
Single sign-on is intended to prevent users from having to set up and know different IDs and passwords for the multitude of different applications and services. Depending on the system, single sign-on mechanisms can be implemented differently. In the web environment, the user often receives a kind of digital ID in the form of a token or cookie after successfully logging on to the SSO system . This data packet acts as an access key for the various services and authenticates the user. The SSO system keeps this access key ready and makes it available at the requested time. Single sign-on differs from the same user same password-Procedure (SUSP) basic. Although SUSP uses the same login data for different services, in contrast to single sign-on, each service requires a separate login including the entry of user data. SSO is not only used in the company to authenticate employees against various company applications and resources, but is also becoming more and more popular in the web and cloud environment.
Single sign-out is the opposite of single sign-on. With single sign-out, the user is logged out of all other services that were used during a session by a single logout. Depending on the type, single sign-out processes work automatically at defined times or can be triggered manually.
What are the advantages and disadvantages of single sign-on (SSO)?
Compared to separate registration procedures, SSO offers a whole range of advantages. Since only one authentication is required, the user saves time and benefits from an increase in productivity. At the same time, security increases since the password only has to be transmitted once and the user does not have to remember a large number of different, possibly insecure passwords. If access is to be changed or blocked for a user, only a single user account needs to be edited in a central location. The error-prone and time-consuming configuration of several identifiers in different databases is eliminated. Single sign-on also reduces the risk of phishing-Attacks, since the same login interface means that users can hardly be tempted to enter their ID and password on other systems.
Комментарии
 0:04:54
0:04:54
 0:06:20
0:06:20
 0:07:58
0:07:58
 0:07:23
0:07:23
 0:04:00
0:04:00
 0:18:30
0:18:30
 0:04:13
0:04:13
 0:02:08
0:02:08
 0:53:12
0:53:12
 0:02:23
0:02:23
 0:01:45
0:01:45
 0:02:37
0:02:37
 0:01:25
0:01:25
 0:02:53
0:02:53
 0:00:29
0:00:29
 0:09:31
0:09:31
 0:00:47
0:00:47
 0:15:00
0:15:00
 0:02:01
0:02:01
 0:05:05
0:05:05
 0:04:31
0:04:31
 0:02:40
0:02:40
 0:17:20
0:17:20
 0:01:53
0:01:53