filmov
tv
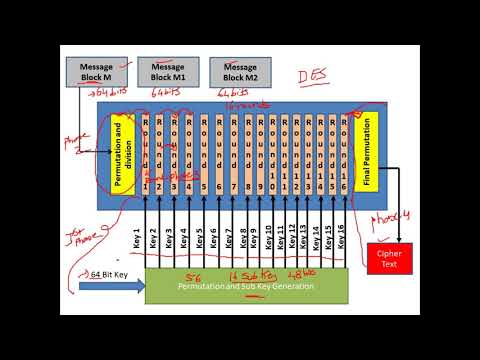
2DES and Meet in the Middle Attack

Показать описание
2DES and Meet in the Middle Attack
Double DES and Meet in the middle attack in 2DES | DES part-3
Kryptographie #26 - Der Meet-in-the-Middle-Angriff auf 2-DES
Block Ciphers and KR Security: 2DES, Meet-in-Middle-Attack, 3DES, AES
What is a Man-in-the-Middle Attack? (In About A Minute)
Saison 2 des Pyjamasques - Nouvel épisode 16 - Dessin Animé
DROIT DE RÉPONSE DU DIMANCHE 12 JANVIER 2025 - ÉQUINOXE TV
Data Encryption Standard (DES) - Explained with an Example - Cryptography - CyberSecurity - CSE4003
Le nouveau coup de pression de Trump sur l'OTAN|LCI
Saison 2 des Pyjamasques - Épisode 13 - Dessin Animé
Maria Zakharova Démolit Zelensky et Encense Trump : Une Déclaration Qui Fait Trembler le Monde !
Phase 2 of Dry Stone Walling and lots of Digging - Here’s What Happened!
Kombuis - Chef Dino - Eend Gestop met Opgestopde Lam - 2 Des 2016
Last to Stop Swinging Wins $1,000,000 (Part 2)
All About Toucans
DES Algorithm (Data Encryption Standard algorithm) | Complete Working | Types - Double & Triple ...
Beginners Guide to Team Tutberidze (drama)
Meet-up #2 des impropreneurs
If you have 2 Potatoes and 1 egg! Simple and so delicious breakfast in minutes! Easy Potato Recipes!
Faits Étranges sur le Corps Humain qui Vous Émerveilleront
La chanson des Alphas
La presse espagnole FLINGUE les COUPABLES du Real mais S’EXTASIE pour Mbappé | Revue de presse
Saison 2 des Pyjamasques - Épisode 12 - Dessin Animé
LES SISTERS - Extrait 'Mon trésor !' - CANAL+kids
Комментарии
 0:07:33
0:07:33
 0:14:57
0:14:57
 0:11:14
0:11:14
 0:47:13
0:47:13
 0:01:20
0:01:20
 0:11:23
0:11:23
 1:50:22
1:50:22
 0:51:39
0:51:39
 0:10:58
0:10:58
 0:23:05
0:23:05
 0:21:46
0:21:46
 0:13:37
0:13:37
 0:08:51
0:08:51
 0:13:03
0:13:03
 0:02:14
0:02:14
 0:27:29
0:27:29
 0:29:22
0:29:22
 0:01:46
0:01:46
 0:06:56
0:06:56
 1:48:55
1:48:55
 0:02:29
0:02:29
 0:05:46
0:05:46
 0:23:05
0:23:05
 0:03:10
0:03:10