filmov
tv
How to proxy traffic and stay anonymous with ProxyChains
Показать описание
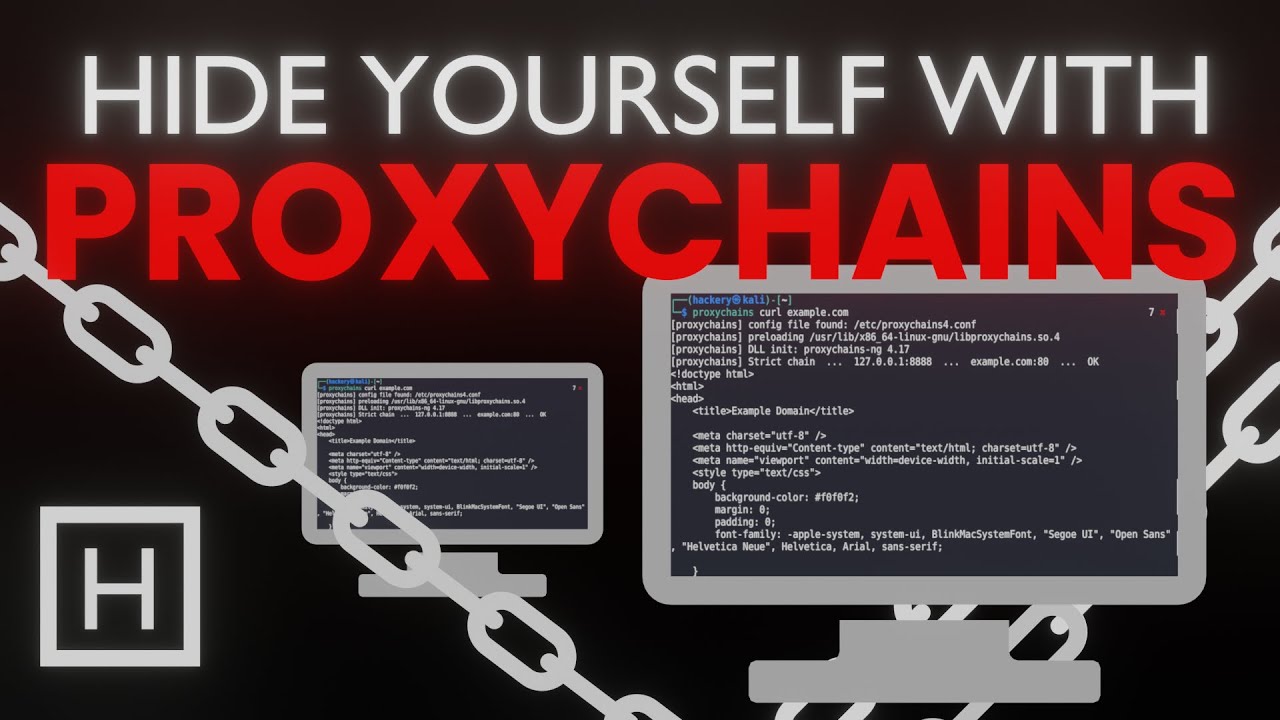
Hide your IP using Proxychains! Tunnel your traffic through not one but multiple proxies to ensure anonymity or to be able to send traffic through normally unreachable networks
By tunneling your connections through a chain of proxies. Proxychains acts as a network traffic anonymizer by routing your data through a series of intermediary proxy servers, shielding your identity from prying eyes on the internet.
In this comprehensive guide, we explore what Proxychains is and how it works, shedding light on the significance of proxy servers in maintaining anonymity online. We emphasize the importance of choosing reliable proxies and provide insights into configuring Proxychains effectively.
Join us as we demonstrate the practical application of Proxychains through step-by-step instructions. From configuring the Proxychains' configuration file to using it with popular command-line tools like Curl, we cover it all. Witness firsthand how Proxychains redirects network traffic, ensuring anonymity in action.
This video is part of the hacking tools series in which we explain how to use cybersecurity tools to secure your systems or your client systems.
00:00 What is ProxyChains
00:40 What is a proxy?
01:24 Configuring proxy chains
02:55 Using Proxychains
04:02 Tor and Proxychains
#cybersecuritytutorial #cybersecuritytools #bugbounty
By tunneling your connections through a chain of proxies. Proxychains acts as a network traffic anonymizer by routing your data through a series of intermediary proxy servers, shielding your identity from prying eyes on the internet.
In this comprehensive guide, we explore what Proxychains is and how it works, shedding light on the significance of proxy servers in maintaining anonymity online. We emphasize the importance of choosing reliable proxies and provide insights into configuring Proxychains effectively.
Join us as we demonstrate the practical application of Proxychains through step-by-step instructions. From configuring the Proxychains' configuration file to using it with popular command-line tools like Curl, we cover it all. Witness firsthand how Proxychains redirects network traffic, ensuring anonymity in action.
This video is part of the hacking tools series in which we explain how to use cybersecurity tools to secure your systems or your client systems.
00:00 What is ProxyChains
00:40 What is a proxy?
01:24 Configuring proxy chains
02:55 Using Proxychains
04:02 Tor and Proxychains
#cybersecuritytutorial #cybersecuritytools #bugbounty
Комментарии
 0:04:52
0:04:52
 0:02:57
0:02:57
 0:05:27
0:05:27
 0:05:17
0:05:17
 0:08:05
0:08:05
 0:04:17
0:04:17
 0:02:19
0:02:19
 0:04:26
0:04:26
 0:01:00
0:01:00
 0:08:56
0:08:56
 0:03:43
0:03:43
 0:15:05
0:15:05
 0:00:32
0:00:32
 0:10:02
0:10:02
 0:09:33
0:09:33
 0:03:25
0:03:25
 0:06:28
0:06:28
 0:03:07
0:03:07
 0:04:55
0:04:55
 0:15:34
0:15:34
 0:03:07
0:03:07
 0:11:57
0:11:57
 0:04:43
0:04:43
 0:00:55
0:00:55