filmov
tv
Use THIS For More SECURE Password Handling In Python

Показать описание
Use this for more secure password handling in Python. #python #code #shorts
Use THIS For More SECURE Password Handling In Python
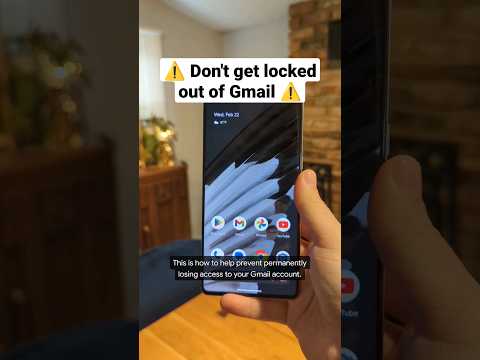
Make your Gmail account even more secure! 🔐 #Shorts
Use THIS For More SECURE Database Access in Python
Secret iPhone security feature you NEED to know about
High security locks easily defeated w/ this method. #lockpicking #homeowner #tools #city #security
12 ESSENTIAL Security Tools I Use Daily
HTTP Secure Headers for Web App Security | CORS, CSP, HSTS and more
Make your Gmail account even more secure with account recovery and 2-step authentication #shorts
AWS re:Inforce 2025 -Move fast & stay secure: Lessons learned from the AWS prototyping team (APS...
How to enable always use secure connections #shorts
Question: Is Tails a More Secure Way to Use TOR?
Don't Use Face ID: Why Passcode is More Secure
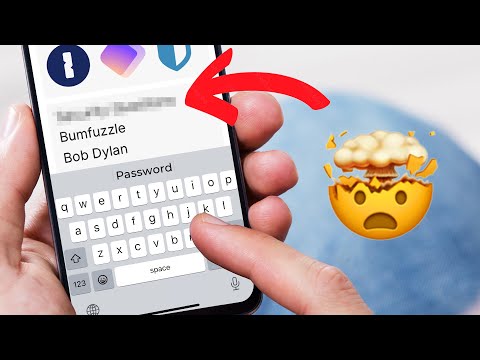
6 hacks to secure ANY password manager you use!
5miles Tips: Use the S.E.A.L. for More Secure Exchange
Former national security adviser analyzes U.S. airstrikes on Iran
Are password managers actually SAFE to use? Honest opinion...
How to use Cursor AI to make your web app more secure than Fort Knox
5 ILLEGAL gadgets that will get you ARRESTED
Which security key should you use?
Trump is 'ready to use force,' but does he 'want' to?
DON'T USE GMAIL until You Change these Security Settings
Don't Lose Your Security Deposit - How Much is the Security Deposit for Medical Counselling 202...
Don't Use Gmail Until You Make these Security Changes!
The Worlds MOST TRUSTED knot.
Комментарии
 0:00:18
0:00:18
 0:00:27
0:00:27
 0:00:16
0:00:16
 0:00:40
0:00:40
 0:00:25
0:00:25
 0:06:14
0:06:14
 0:08:06
0:08:06
 0:00:27
0:00:27
 0:54:16
0:54:16
 0:00:14
0:00:14
 0:07:49
0:07:49
 0:01:05
0:01:05
 0:06:47
0:06:47
 0:01:33
0:01:33
 0:06:09
0:06:09
 0:09:00
0:09:00
 1:40:09
1:40:09
 0:00:47
0:00:47
 0:00:50
0:00:50
 0:04:48
0:04:48
 0:05:03
0:05:03
 0:14:35
0:14:35
 0:10:20
0:10:20
 0:00:25
0:00:25