filmov
tv
Hashing Algorithms + Coding up a File Integrity Monitor (FIM) | CYBER SECURITY PROJECTS

Показать описание
In this video we gain a better understanding of what integrity means in Cyber Security through a live example of file integrity monitoring via a live demo! I do some live/realistic coding and build a file Integrity monitor.
🙇♂️ - Patreon - 🙇♂️
📹 - Video Links - 📹
⌨️ - Coding - ⌨️
⭐️ - Social Media - ⭐️
🎥 - Equipment - 🎥
📄 - Sample Resumes - 📄
0:00 Intro
1:37 Application Overview (Flow Chart)
4:13 Pre-coding disclaimer (I'm not that fast)
4:41 Begin Coding
34:34 Begin Demo
35:25 Outro
What is INTEGRITY in Cyber Security (CIA Triad!) | LIVE DEMO
Realistic Coding Demo from CS Grad | Live Example of INTEGRITY in Cyber Security
DISCLAIMER: This video description has some affiliate links and I may receive a small commission. I only share stuff that I use and believe in. Thanks so much for your support 🥺
🙇♂️ - Patreon - 🙇♂️
📹 - Video Links - 📹
⌨️ - Coding - ⌨️
⭐️ - Social Media - ⭐️
🎥 - Equipment - 🎥
📄 - Sample Resumes - 📄
0:00 Intro
1:37 Application Overview (Flow Chart)
4:13 Pre-coding disclaimer (I'm not that fast)
4:41 Begin Coding
34:34 Begin Demo
35:25 Outro
What is INTEGRITY in Cyber Security (CIA Triad!) | LIVE DEMO
Realistic Coding Demo from CS Grad | Live Example of INTEGRITY in Cyber Security
DISCLAIMER: This video description has some affiliate links and I may receive a small commission. I only share stuff that I use and believe in. Thanks so much for your support 🥺
Hashing Algorithms + Coding up a File Integrity Monitor (FIM) | CYBER SECURITY PROJECTS
Learn Hash Tables in 13 minutes #️⃣
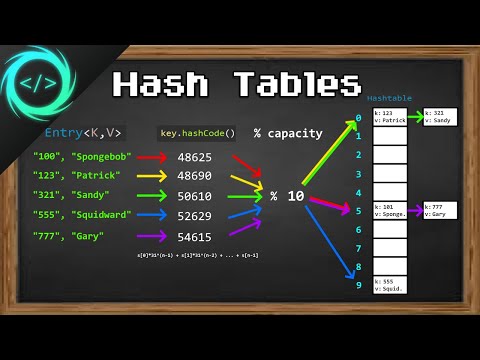
Hash Tables and Hash Functions
Hashing, Hashing Algorithms, and Collisions - Cryptography - Practical TLS
Five* non-cryptographic hash functions enter. One hash function leaves.
SHA: Secure Hashing Algorithm - Computerphile
How do dictionaries (hashmaps) actually work?
What Is Hashing? | What Is Hashing With Example | Hashing Explained Simply | Simplilearn
Crack Any coding interviews like this | Coding | Example - SOTI
Murmur Hash - Explained
Hashes 4 Hash Functions for Strings
Python MD5 implementation
Faster than Rust and C++: the PERFECT hash table
Python Hash Sets Explained & Demonstrated - Computerphile
Cuckoo Hashing: Visualization + Explanation
Top 6 Coding Interview Concepts (Data Structures & Algorithms)
4. Hashing
Hashing, explained in 50 seconds
Data Structures: Hash Tables
What is a Cryptographic Hashing Function? (Example + Purpose)
Hashing Explained
7 Cryptography Concepts EVERY Developer Should Know
SHA-256 | COMPLETE Step-By-Step Explanation (W/ Example)
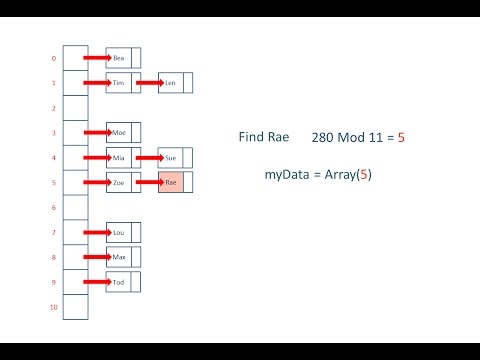
Understanding and implementing a Hash Table (in C)
Комментарии
 0:37:49
0:37:49
 0:13:26
0:13:26
 0:13:56
0:13:56
 0:11:42
0:11:42
 0:37:31
0:37:31
 0:10:21
0:10:21
 0:01:36
0:01:36
 0:09:45
0:09:45
 0:09:08
0:09:08
 0:18:33
0:18:33
 0:11:16
0:11:16
 0:10:27
0:10:27
 0:33:52
0:33:52
 0:18:39
0:18:39
 0:04:42
0:04:42
 0:10:51
0:10:51
 0:52:55
0:52:55
 0:00:50
0:00:50
 0:06:25
0:06:25
 0:07:08
0:07:08
 0:10:59
0:10:59
 0:11:55
0:11:55
 0:13:01
0:13:01
 0:24:54
0:24:54