filmov
tv
22. Cryptography: Encryption

Показать описание
MIT 6.046J Design and Analysis of Algorithms, Spring 2015
Instructor: Srinivas Devadas
In this lecture, Professor Devadas continues with cryptography, introducing encryption methods.
License: Creative Commons BY-NC-SA
Instructor: Srinivas Devadas
In this lecture, Professor Devadas continues with cryptography, introducing encryption methods.
License: Creative Commons BY-NC-SA
22. Cryptography: Encryption
7 Cryptography Concepts EVERY Developer Should Know
Kryptographie #22 - Verschlüsselung und Authentifikation in Einem
Basics of Cryptology – Part 22 (Cryptography – Kerckhoffs' Principle & Modern Cryptographic...
Basics of Cryptology – Part 23 (Cryptography – Modern Hybrid Encryption)
How Cryptography Works in Real Life ?
Cryptography MindMap (6 of 9) | CISSP Domain 3
Learn Cryptography | Part 4 - Encryption Modes and Attacks
Exercise 2.6 Q:9,10 class 11 NBF Ex 2.6 class11 National book foundation Question:9,10 New Book 2024
Public Key Cryptography - Computerphile
#22 Block Cipher Modes Of Operation - Part 1 |CNS|
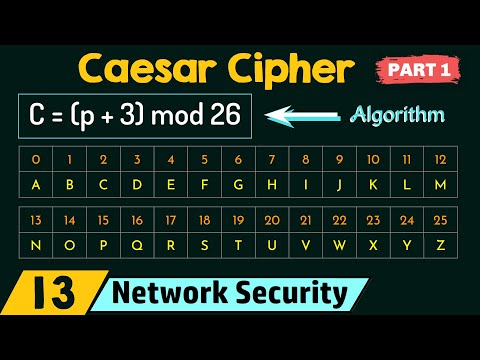
Caesar Cipher (Part 1)
AES Explained (Advanced Encryption Standard) - Computerphile
Break RSA Encryption in 10 Lines of Python Code | #Shorts Quantum Computing with Shor's Algorit...
CSS #22 Vigenère cipher🔥 | Kasiski Test | Solved Example | Cryptography | CSS | BTB | Be The Best...
Hill Cipher (Encryption)
Everyday Cryptography (fundamentals principles and applications) by Keith M Martin
Introduction to Cryptography - Encryption and Decryption
Cryptography and Network Security: #2 Modulo Arithmetic and Basic Concept
Cryptography – Key Terms
Cryptography: Crash Course Computer Science #33
Cryptography | Cryptography Use-Cases | Data Security | Encryption | Decryption
Cryptography: Secret Key Encryption
Encoding and Decoding || Application of Linear Algebra || Encryption and Decryption #cryptography
Комментарии
 1:24:15
1:24:15
 0:11:55
0:11:55
 0:08:57
0:08:57
 0:23:33
0:23:33
 0:22:43
0:22:43
 0:00:45
0:00:45
 0:22:51
0:22:51
 0:22:42
0:22:42
 0:36:58
0:36:58
 0:06:20
0:06:20
 0:08:44
0:08:44
 0:13:23
0:13:23
 0:14:14
0:14:14
 0:00:39
0:00:39
 0:12:03
0:12:03
 0:17:39
0:17:39
 0:00:08
0:00:08
 0:05:52
0:05:52
 0:10:04
0:10:04
 0:09:39
0:09:39
 0:12:33
0:12:33
 0:26:51
0:26:51
 0:30:14
0:30:14
 0:14:45
0:14:45