filmov
tv
Cryptography | Cryptography Use-Cases | Data Security | Encryption | Decryption

Показать описание
*Cryptography Use-Cases | Public Key Cryptography | Hash Functions | Symmetric Key Cryptography*
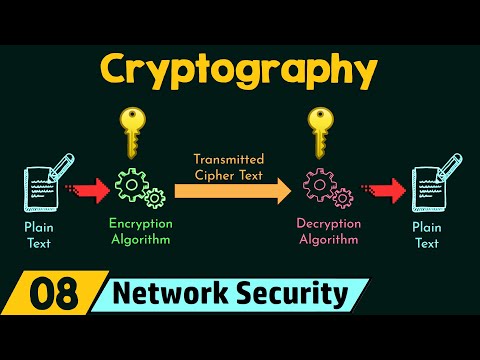
In any network communication topology, sending and receiving data is regular practice. Sending data over network channels are always prone to hacking threats. A plane data sent over network communication channels can be hacked and security of the data can be compromised. So sending data without proper security measures is a potential risk for data security.
Cryptography is a practice to send data over communication channels securely. For secure data data transmission, source data is encrypted using efficient algorithms and encrypted data is sent over communication channels.
In this TechTalk, we will discuss about different cryptography use cases. We will learn about typical transmission topology and how data security can be achieved in typical transmission topology. We will discuss different commonly available algorithms to provide data security and integrity and practical usage of them.
Note - In this tech talk, many times encoding/decoding term is used for encryption/decryption.
#cryptography #datasecurity #encryption #decryption #encoding #decoding #dataprivacy #dataintegrity #publickey
Chapters -
0:00 - Introduction
0:25 - Agenda
0:45 - Typical Data Transmission Topology
1:24 - Cryptographic Security Use-Cases
5:06 - Cryptography Algorithms
8:27 - Public Key Cryptography
9:49 - Public Key Cryptography - Encoding/Decoding workflow
13:25 - Cryptographic Hash Functions
17:10 - Cryptographic Hash Functions Practical Usage - Password Hashing
24:54 - Symmetric Key Cryptography
26:38 - Closing Note
In any network communication topology, sending and receiving data is regular practice. Sending data over network channels are always prone to hacking threats. A plane data sent over network communication channels can be hacked and security of the data can be compromised. So sending data without proper security measures is a potential risk for data security.
Cryptography is a practice to send data over communication channels securely. For secure data data transmission, source data is encrypted using efficient algorithms and encrypted data is sent over communication channels.
In this TechTalk, we will discuss about different cryptography use cases. We will learn about typical transmission topology and how data security can be achieved in typical transmission topology. We will discuss different commonly available algorithms to provide data security and integrity and practical usage of them.
Note - In this tech talk, many times encoding/decoding term is used for encryption/decryption.
#cryptography #datasecurity #encryption #decryption #encoding #decoding #dataprivacy #dataintegrity #publickey
Chapters -
0:00 - Introduction
0:25 - Agenda
0:45 - Typical Data Transmission Topology
1:24 - Cryptographic Security Use-Cases
5:06 - Cryptography Algorithms
8:27 - Public Key Cryptography
9:49 - Public Key Cryptography - Encoding/Decoding workflow
13:25 - Cryptographic Hash Functions
17:10 - Cryptographic Hash Functions Practical Usage - Password Hashing
24:54 - Symmetric Key Cryptography
26:38 - Closing Note
 0:03:36
0:03:36
 0:04:40
0:04:40
 1:16:21
1:16:21
 0:25:08
0:25:08
 0:03:51
0:03:51
 0:58:58
0:58:58
 0:53:56
0:53:56
 0:17:39
0:17:39
 0:19:03
0:19:03
 0:02:28
0:02:28
 0:13:58
0:13:58
 0:13:34
0:13:34
 0:04:21
0:04:21
 0:28:09
0:28:09
 0:12:33
0:12:33
 0:17:12
0:17:12
 0:11:41
0:11:41
 0:00:56
0:00:56
 0:28:28
0:28:28
 0:00:41
0:00:41
 0:00:44
0:00:44
 0:00:46
0:00:46
 0:08:43
0:08:43
 0:11:32
0:11:32