filmov
tv
Quantum Key Distribution, BB84 - simply explained | Quantum 1x1

Показать описание
Our cell phones and computers are constantly sending and receiving information. To ensure that only the right recipients can read this information, it is encrypted. But we have to agree on a key beforehand. And how are we supposed to know that there isn't already someone listening in or reading along?
Exactly for this there is an ingenious trick, the quantum key exchange (QKD - #QuantumKeyDistribution). With it, we can create a key together, and can test whether someone has been eavesdropping. Instead of mathematical riddles, it is based on the exchange of photons. Since they have to obey the laws of physics, and so do we, the process is considered unbreakable. By the way, the method is called BB84 protocol and belongs to quantum cryptography, or quantum encryption. (#QuantumCryptography, #QuantumEncryption)
00:00 Why a quantum key exchange? - an example
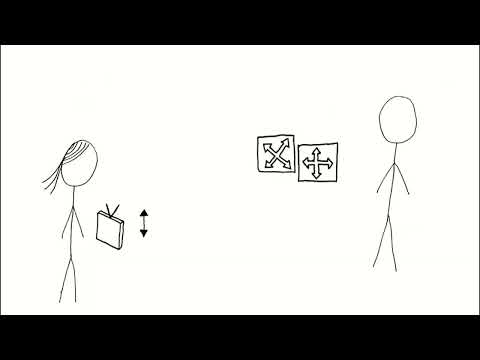
00:51 Photons, polarization and polarization filters
02:14 Quantum key exchange (QKD).
02:56 An attacker (man-in-the-middle)
03:53 Quantum key exchange evaluation
You can also create your own quantum key with our tinkering box Qey-Gen.
__________ The Quantum 1x1 __________
__________ About the channel __________
Dear teachers, educators, school administrators, parents, digital experts, technology enthusiasts, hobbyists and those who want to become one! Here in the TüftelLab channel you will always find the latest instructions and tinkering tricks. You can also subscribe to our newsletter or social media channels.
The TüftelLab is a hybrid learning space for young tinkerers
Exactly for this there is an ingenious trick, the quantum key exchange (QKD - #QuantumKeyDistribution). With it, we can create a key together, and can test whether someone has been eavesdropping. Instead of mathematical riddles, it is based on the exchange of photons. Since they have to obey the laws of physics, and so do we, the process is considered unbreakable. By the way, the method is called BB84 protocol and belongs to quantum cryptography, or quantum encryption. (#QuantumCryptography, #QuantumEncryption)
00:00 Why a quantum key exchange? - an example
00:51 Photons, polarization and polarization filters
02:14 Quantum key exchange (QKD).
02:56 An attacker (man-in-the-middle)
03:53 Quantum key exchange evaluation
You can also create your own quantum key with our tinkering box Qey-Gen.
__________ The Quantum 1x1 __________
__________ About the channel __________
Dear teachers, educators, school administrators, parents, digital experts, technology enthusiasts, hobbyists and those who want to become one! Here in the TüftelLab channel you will always find the latest instructions and tinkering tricks. You can also subscribe to our newsletter or social media channels.
The TüftelLab is a hybrid learning space for young tinkerers
 0:05:01
0:05:01
 0:10:00
0:10:00
 0:12:41
0:12:41
 0:03:45
0:03:45
 0:13:39
0:13:39
 0:21:53
0:21:53
 0:30:15
0:30:15
 0:07:12
0:07:12
 0:27:51
0:27:51
 0:15:09
0:15:09
 0:09:39
0:09:39
 0:28:18
0:28:18
 1:07:03
1:07:03
 0:04:47
0:04:47
 0:05:28
0:05:28
 0:02:56
0:02:56
 0:28:36
0:28:36
 0:59:35
0:59:35
 0:01:57
0:01:57
 0:12:07
0:12:07
 0:08:13
0:08:13
 0:20:05
0:20:05
 0:14:54
0:14:54
 0:08:20
0:08:20