filmov
tv
What is INTEGRITY in Cyber Security (CIA Triad!) | LIVE DEMO (FIM/File Integrity Monitor)

Показать описание
In this video we gain a better understanding of what integrity means in Cyber Security through a live example of file integrity monitoring via a live demo!
🙇♂️ - Patreon - 🙇♂️
📹 - Video Links - 📹
⌨️ - Coding - ⌨️
⭐️ - Social Media - ⭐️
🎥 - Equipment - 🎥
📄 - Sample Resumes - 📄
0:00 Intro
0:45 Overview
2:06 Begin Integrity / FIM demonstration
5:25 Manual Hash Checking
6:10 Outro
What is INTEGRITY in Cyber Security (CIA Triad!) | LIVE DEMO
DISCLAIMER: This video description has some affiliate links and I may receive a small commission. I only share stuff that I use and believe in. Thanks so much for your support 🥺
🙇♂️ - Patreon - 🙇♂️
📹 - Video Links - 📹
⌨️ - Coding - ⌨️
⭐️ - Social Media - ⭐️
🎥 - Equipment - 🎥
📄 - Sample Resumes - 📄
0:00 Intro
0:45 Overview
2:06 Begin Integrity / FIM demonstration
5:25 Manual Hash Checking
6:10 Outro
What is INTEGRITY in Cyber Security (CIA Triad!) | LIVE DEMO
DISCLAIMER: This video description has some affiliate links and I may receive a small commission. I only share stuff that I use and believe in. Thanks so much for your support 🥺
What is INTEGRITY in Cyber Security (CIA Triad!) | LIVE DEMO (FIM/File Integrity Monitor)
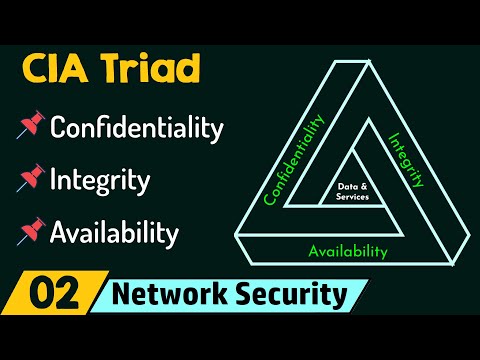
What is Integrity , Key Security Principle of Cyber Security
What is the CIA Triad? (See Description)
CIA Triad
Data Integrity and Cyber Recovery: Dell EMC and VMware
What is Cyber Security?
What is The CIA Triad in Cyber Security? Confidentiality, Integrity, Availability Explained
CIA triad - confident cyber security
CyberQuest 1.0: Cyber Resilience in the Digital Age; Preparing for the Inevitable
02 - What is CIA in Cyber Security
What is non-repudiation in cyber security?
Hashing Algorithms + Coding up a File Integrity Monitor (FIM) | CYBER SECURITY PROJECTS
cyber security goals- CIA confidentiality,integrity,availability in hindi | MCA/btech/bca/bsc it
Introduction to Cyber Security part 1 | Beginners guide to Security by design
What is a Cyber Security Audit and why it’s important
File and Data Integrity Checks with Cisco Skills For All (Cyber)
CIA Triad is the most fundamental principle in Cyber Security
Cyber Security Awareness - Think before click - Funny But Serious
What Is Hashing? | What Is Hashing With Example | Hashing Explained Simply | Simplilearn
Cybersecurity Awareness Training FY 22-23
What Is The CIA Triad In Cyber Security? #ciatriad #confidentiality #integrity #availability
Security Services
Basics Of Cyber Security|| Confidentiality, Integrity And Availability
What is CIA Triad | CIA Triad in Cyber Security | CIA Triad Explained | Intellipaat
Комментарии
 0:07:06
0:07:06
 0:02:50
0:02:50
 0:02:06
0:02:06
 0:16:08
0:16:08
 0:43:54
0:43:54
 0:08:34
0:08:34
 0:01:28
0:01:28
 0:04:16
0:04:16
 2:29:28
2:29:28
 0:06:02
0:06:02
 0:03:28
0:03:28
 0:37:49
0:37:49
 0:04:18
0:04:18
 0:04:17
0:04:17
 0:01:51
0:01:51
 0:18:21
0:18:21
 0:00:56
0:00:56
 0:01:16
0:01:16
 0:09:45
0:09:45
 0:27:42
0:27:42
 0:01:08
0:01:08
 0:08:56
0:08:56
 0:21:20
0:21:20
 0:06:57
0:06:57