filmov
tv
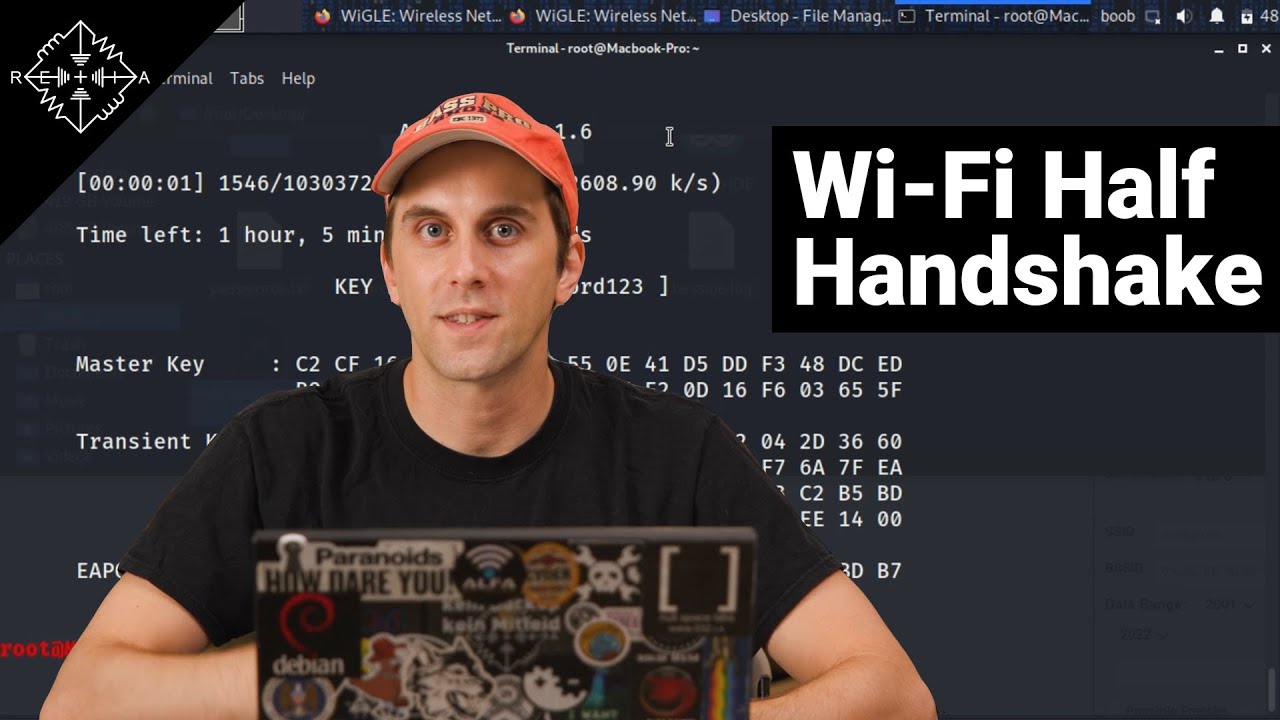
HakByte: Capture Wi-Fi Passwords From Smartphones with a Half-Handshake Attack
Показать описание
In this episode, we show how hackers can abuse convenience features of Wi-Fi to extract passwords from nearby smartphones belonging to Wi-Fi networks they've connected to in the past.
-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆
-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆
-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆
-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆
HakByte: Capture Wi-Fi Passwords From Smartphones with a Half-Handshake Attack
How to Hack Wi Fi Passwords
Hacking wifi with wireshark https://youtu.be/RWOPezHfZuM
Advanced WiFi Scanning with Aircrack-NG
HakByte: Build a Hackable Router with a $5 ESP32
How To Crack WPA2 WiFi Password With AirCrack-NG - WiFi Pentesting Video 2024
Grabbing Windows Wi-Fi Passwords with the O.MG Cable | HakByte
HakByte: Catch Hackers in Your Wi-Fi With a $3 FTP Honeypot
WIFI Pinapple Evil Portal #hak5
How Hackers Capture Wi-Fi Passwords From Smartphones
I Learned How To Hack WiFi In 2 Days...
Stealing Passwords Using Wireshark and Ettercap
HakByte: Create a $15 WarDriving Rig to Log WiFi Data w/ the ESP8266
Wi-Fi password hack: How to hack into WPA Wi-Fi and WPA2 | Free Cyber Work Applied series
WiFi hash purple monster Arduino capture EAPOL/PMKID PACKETS WiFi password hacking
It's too easy to own a WiFi network
HakByte: Gather WiFi Reconnaissance on this $5 MicroController
CRACKING WPA2 WIFI PASSWORDS [EASY] 🔒 | Bettercap & Aircrack
Cracking WPA2 Passwords With The Wi-Fi Pineapple Mark VII
HakByte: How to find anything on the internet with Google Dorks
WiFi Password Hacking
how Hackers crack any WiFi password?! set strong WiFi password now!
Getting a Handshake and Data Capture | Advanced wifi hacking Part 1 | Hackersploit
How To Crack WPS And WPA2 WiFi Password With Wifite2 - WiFi Pentesting Video 2023
Комментарии
 0:11:15
0:11:15
 0:03:56
0:03:56
 0:00:16
0:00:16
 0:17:59
0:17:59
 0:13:16
0:13:16
 0:10:19
0:10:19
 0:10:58
0:10:58
 0:12:21
0:12:21
 0:00:29
0:00:29
 0:34:16
0:34:16
 0:14:54
0:14:54
 0:08:03
0:08:03
 0:08:21
0:08:21
 0:08:18
0:08:18
 0:00:16
0:00:16
 0:05:34
0:05:34
 0:08:47
0:08:47
 0:02:16
0:02:16
 0:06:38
0:06:38
 0:18:52
0:18:52
 0:14:49
0:14:49
 0:09:11
0:09:11
 0:06:00
0:06:00
 0:13:15
0:13:15