filmov
tv
Advanced WiFi Scanning with Aircrack-NG

Показать описание
Hak5 -- Cyber Security Education, Inspiration, News & Community since 2005:
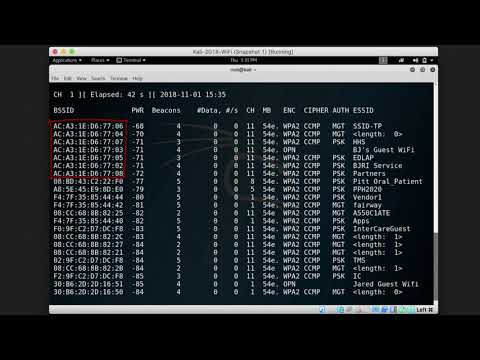
In this episode of HakByte, Alex Lynd demonstrates how to gather wireless reconnaissance using the Airodump-ng tool, and a monitor-mode-enabled WiFi dongle. Following along, you can learn how to use advanced features and filters with Airodump-ng to hone in your WiFi attacks or recon, as well as how to output capture files that can later be analyzed w/ tools like Wireshark.
Links:
Chapters:
Intro: 00:00
How WiFi Can be Sniffed: 00:16
Install AirCrack for WiFi Hacking: 01:08
AirCrack Tool Overview: 01:45
Enabling Monitor Mode 02:20
Basic WiFi Recon 03:22
Airodump Parameters 04:25
Filtering out Client Devices 04:58
Probe Requests: 05:56
Finding Device Manufacturers: 06:45
Associate Devices w/ Networks: 08:31
Adding Color Markers: 09:05
Sorting for WiFi Attributes 09:57
Inverting the Sort Algorithm: 10:50
Further Interface Options: 11:07
Capturing a WiFi Handshake: 11:55
Target a WiFi Channel: 12:21
Target a WiFi Device: 13:34
Saving a Capture File: 14:19
FileType Overview: 14:57
Capturing Dual Band: 15:50
Capturing on 5GHz: 16:33
Future Episodes: 17:19
Outro: 17:40
-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆
-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆
____________________________________________
Founded in 2005, Hak5's mission is to advance the InfoSec industry. We do this through our award winning educational podcasts, leading pentest gear, and inclusive community – where all hackers belong.
In this episode of HakByte, Alex Lynd demonstrates how to gather wireless reconnaissance using the Airodump-ng tool, and a monitor-mode-enabled WiFi dongle. Following along, you can learn how to use advanced features and filters with Airodump-ng to hone in your WiFi attacks or recon, as well as how to output capture files that can later be analyzed w/ tools like Wireshark.
Links:
Chapters:
Intro: 00:00
How WiFi Can be Sniffed: 00:16
Install AirCrack for WiFi Hacking: 01:08
AirCrack Tool Overview: 01:45
Enabling Monitor Mode 02:20
Basic WiFi Recon 03:22
Airodump Parameters 04:25
Filtering out Client Devices 04:58
Probe Requests: 05:56
Finding Device Manufacturers: 06:45
Associate Devices w/ Networks: 08:31
Adding Color Markers: 09:05
Sorting for WiFi Attributes 09:57
Inverting the Sort Algorithm: 10:50
Further Interface Options: 11:07
Capturing a WiFi Handshake: 11:55
Target a WiFi Channel: 12:21
Target a WiFi Device: 13:34
Saving a Capture File: 14:19
FileType Overview: 14:57
Capturing Dual Band: 15:50
Capturing on 5GHz: 16:33
Future Episodes: 17:19
Outro: 17:40
-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆
-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆
____________________________________________
Founded in 2005, Hak5's mission is to advance the InfoSec industry. We do this through our award winning educational podcasts, leading pentest gear, and inclusive community – where all hackers belong.
Комментарии
 0:17:59
0:17:59
 0:13:29
0:13:29
 0:00:16
0:00:16
 0:10:19
0:10:19
 0:02:54
0:02:54
 0:02:54
0:02:54
 0:00:54
0:00:54
 0:00:18
0:00:18
 0:12:15
0:12:15
 0:03:08
0:03:08
 0:19:35
0:19:35
 0:22:12
0:22:12
 0:00:21
0:00:21
 0:00:28
0:00:28
 0:05:46
0:05:46
 0:00:15
0:00:15
 0:00:18
0:00:18
 0:00:28
0:00:28
 0:07:29
0:07:29
 0:00:17
0:00:17
 0:00:18
0:00:18
 0:03:08
0:03:08
 0:00:06
0:00:06
 0:01:49
0:01:49