filmov
tv
GitOps - Feat. Flux, Argo CD, and kapp-controller (You Choose!, Ch. 2, Ep. 2)

Показать описание
Choose Your Own Adventure: The Treacherous Trek to Production
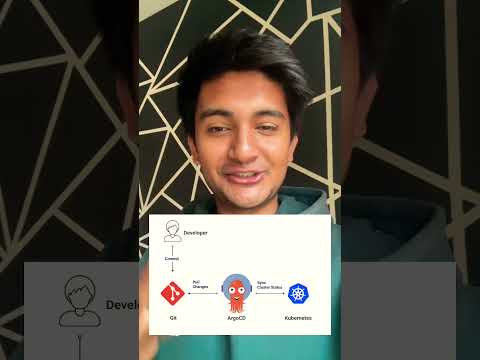
In this episode, we'll figure out how to reconcile the actual state (Kubernetes resources) into the desired state stored in Git (Kubernetes manifests). This time, the choice will be between Flux, Argo CD, and Carvel kapp-controller.
#argocd #fluxcd #carvel #kubernetes
▬▬▬▬▬▬ 🔗 Additional Info 🔗 ▬▬▬▬▬▬
In this episode, we'll figure out how to reconcile the actual state (Kubernetes resources) into the desired state stored in Git (Kubernetes manifests). This time, the choice will be between Flux, Argo CD, and Carvel kapp-controller.
#argocd #fluxcd #carvel #kubernetes
▬▬▬▬▬▬ 🔗 Additional Info 🔗 ▬▬▬▬▬▬
GitOps - Feat. Flux, Argo CD, and kapp-controller (You Choose!, Ch. 2, Ep. 2)
Flux GitOps Tutorial - DevOps and GitOps for Kubernetes
The GitOps Dilemma: Flux or Argo?
Flux Vs Argo CD| Which is best|Similarities vs Differences
Mastering Argo CD Sync Waves: A Deep Dive into Effective GitOps Synchronization Strategies
Applying GitOps To Infrastructure With Flux And Crossplane
How to migrate from Flux to Argo CD | Stream Highlights
Combining Argo CD (GitOps), Crossplane (Control Plane), And KubeVela (OAM)
GitOps with Flux and OCI Registries - Soulé Ba & Scott Rigby, Weaveworks
Using GitOps for Infrastructure and Applications with Crossplane & Argo CD
GitOps Days 2022: Applying GitOps to Everything with Crossplane + Flux by Viktor Farcic
Continuous Delivery With GitOps (Using Kubernetes) - Concepts + Code Walkthrough
How To Apply GitOps To Everything Using Crossplane And Flux
GitOps on AKS with the Flux v2 Extension
How to Preview and Diff Your Argo CD Deployments - Kostis Kapelonis, Codefresh
Intro: Flux - Stefan Prodan, Weaveworks & Alexis Richardson, Weaveworks
Implementing GitOps best practices with Crossplane and ArgoCD
vSphere 7 With Kubernetes - Declarative GitOps with Argo CD
Kubernetes Continuous Deployment using Argo CD and GitOps on AWS EKS
The Future of DevOps is Here: GitOps Explained! 🔥
Implementing GitOps best practices with Crossplane and ArgoCD - Anaïs Urlichs
Is GitOps Replacing DevOps?
Flux Beyond Git: Harnessing the Power of OCI - Stefan Prodan & Hidde Beydals, Weaveworks
GitOps for Beginners! | ArgoCD
Комментарии
 1:11:13
1:11:13
 0:11:55
0:11:55
 1:35:25
1:35:25
 0:01:39
0:01:39
 0:18:27
0:18:27
 0:14:45
0:14:45
 0:20:39
0:20:39
 0:15:46
0:15:46
 0:33:15
0:33:15
 0:56:09
0:56:09
 0:23:52
0:23:52
 0:58:52
0:58:52
 0:20:08
0:20:08
 0:26:07
0:26:07
 0:21:16
0:21:16
 0:41:59
0:41:59
 0:58:40
0:58:40
 0:05:46
0:05:46
 0:27:40
0:27:40
 0:00:39
0:00:39
 1:02:10
1:02:10
 1:00:28
1:00:28
 0:39:51
0:39:51
 0:13:20
0:13:20