filmov
tv
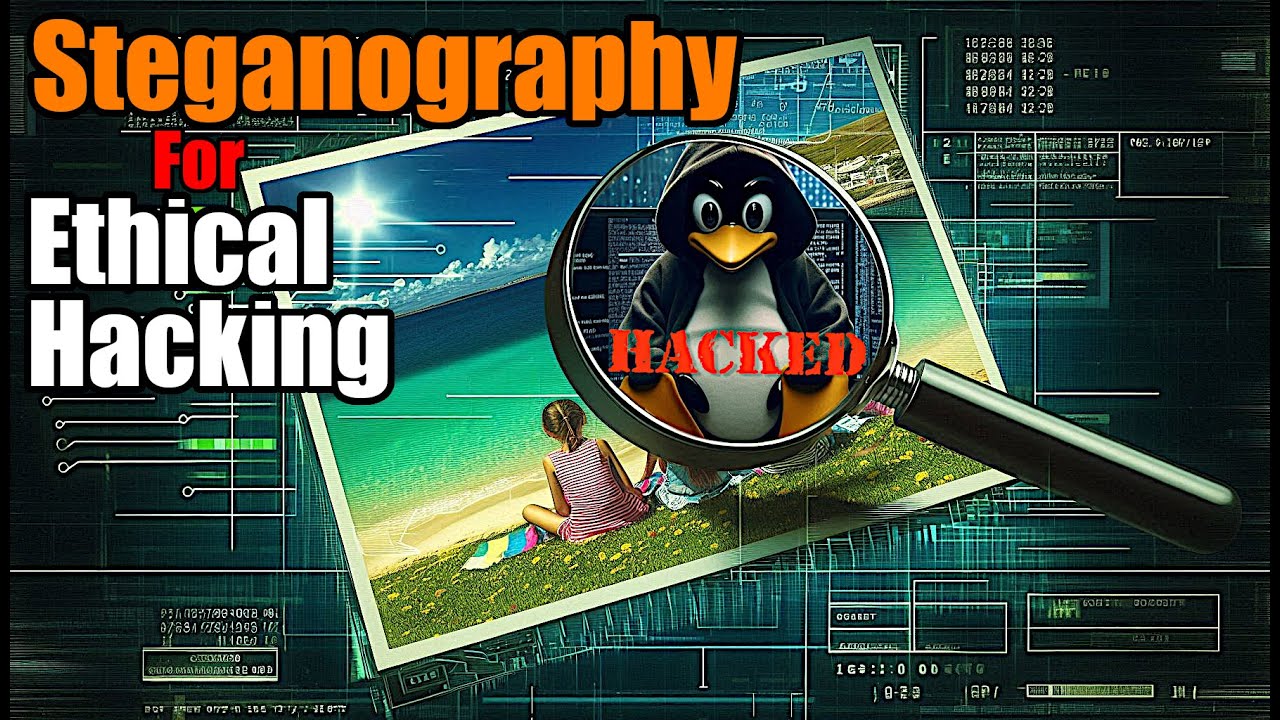
How to Hide Data in Images: Steganography for Ethical Hacking
Показать описание
In this video, we explore steganography—the technique of hiding data within other files. You’ll see how attackers can conceal messages, password files, scripts, and even malware inside seemingly innocent images, all while bypassing antivirus, Data loss protection, Intrusion detection systems, and other security controls. We’ll walk through how steganography is used in ethical hacking and penetration testing to simulate data exfiltration, deliver hidden payloads, or avoid detection. Plus, you'll learn how to uncover hidden data using tools like Steghide and Stegcracker.
If you're interested in enhancing your cybersecurity skills, especially in ethical hacking, this video will show you how steganography plays a critical role in real-world attack simulations.
Key Topics Covered:
Introduction to Steganography
How attackers hide malicious payloads
Steghide for embedding and detecting hidden data
Real-world examples of steganography in use
Chapters:
00:00 Introduction
01:56 Steghide Installation
03:20 Embedding Data into Images
6:10 Extracting Hidden Data
9:18 Stegcracker Installation and Use for Brute force with Wordlists
13:11 File for Identifying File Type
---
--
Disclaimer: Hacking without permission is illegal. This channel is strictly for educational purposes only. We cover cybersecurity in the areas of ethical hacking and penetration testing to help make others aware and be better prepared to defend against cyber threats.
If you're interested in enhancing your cybersecurity skills, especially in ethical hacking, this video will show you how steganography plays a critical role in real-world attack simulations.
Key Topics Covered:
Introduction to Steganography
How attackers hide malicious payloads
Steghide for embedding and detecting hidden data
Real-world examples of steganography in use
Chapters:
00:00 Introduction
01:56 Steghide Installation
03:20 Embedding Data into Images
6:10 Extracting Hidden Data
9:18 Stegcracker Installation and Use for Brute force with Wordlists
13:11 File for Identifying File Type
---
--
Disclaimer: Hacking without permission is illegal. This channel is strictly for educational purposes only. We cover cybersecurity in the areas of ethical hacking and penetration testing to help make others aware and be better prepared to defend against cyber threats.
Комментарии
 0:19:17
0:19:17
 0:01:32
0:01:32
 0:00:26
0:00:26
 0:00:12
0:00:12
 0:00:32
0:00:32
 0:01:02
0:01:02
 0:14:45
0:14:45
 0:01:33
0:01:33
 0:00:31
0:00:31
 0:00:55
0:00:55
 0:00:48
0:00:48
 0:00:19
0:00:19
 0:08:49
0:08:49
 0:00:42
0:00:42
 0:14:25
0:14:25
 0:01:00
0:01:00
 0:04:44
0:04:44
 0:11:03
0:11:03
 0:01:25
0:01:25
 0:03:48
0:03:48
 0:17:52
0:17:52
 0:00:17
0:00:17
 0:33:30
0:33:30
 0:00:35
0:00:35