filmov
tv
How to automate Zero Trust: Step-by-Step Twingate + Terraform Guide?

Показать описание
Setting Up Twingate on AWS Using Terraform | Zero Trust Network Tutorial
Welcome to our comprehensive guide on setting up Twingate on AWS using Terraform! In this video, we delve into the essential concept of a Zero Trust Network and demonstrate how to leverage Twingate for securing your AWS environment.
What You'll Learn
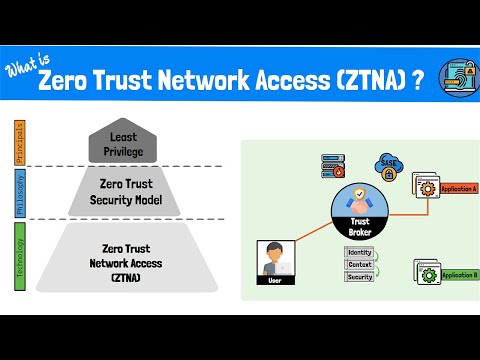
1. Understanding Zero Trust Network Model We'll start with a brief introduction to the Zero Trust Network model, explaining how it differs from traditional security approaches. You'll learn why adopting Zero Trust is crucial in today's cybersecurity landscape and how it ensures that every access request is authenticated and authorized.
2. Overview of Twingate Next, we’ll provide an overview of Twingate, a cutting-edge solution for secure remote access. You'll understand how Twingate facilitates the implementation of Zero Trust principles and simplifies network security management.
3. Setting Up Twingate Connector Using Terraform We’ll walk you through the process of setting up the Twingate Connector using Terraform. You'll learn how to write and apply Terraform configurations to deploy the Twingate Connector on your AWS infrastructure efficiently.
4. Configuring Twingate Resource on AWS In this section, we’ll demonstrate how to configure Twingate resources on AWS. You’ll see the steps involved in integrating Twingate with your AWS environment, ensuring secure access to your cloud resources.
5. Testing Connectivity from Mobile to AWS EC2 Once the setup is complete, we'll test the connectivity from a mobile device to an AWS EC2 instance. This practical demonstration will show you how to verify that your Twingate configuration is working correctly, ensuring secure access from your mobile device.
6. Verifying Secure Access from Laptop to EC2 Instance with Private IP Finally, we'll test secure access from a laptop to an EC2 instance with a private IP. This step ensures that your Zero Trust Network setup allows authorized devices to access private cloud resources securely.
Resources and Links
• Twingate Documentation: Twingate Documentation
• Terraform AWS Provider: Terraform AWS Provider
• Sample Terraform Code: (Link to your repository or sample code if available)
Connect with Me
Stay Connected
If you found this video helpful, please give it a thumbs up, subscribe to the channel for more tutorials, and hit the bell icon to get notified when new videos are released. Feel free to leave any questions or feedback in the comments below!
#Twingate #Terraform #AWS #ZeroTrust #CloudSecurity #DevOps #CyberSecurity #NetworkSecurity #RemoteAccess #InfrastructureAsCode
Welcome to our comprehensive guide on setting up Twingate on AWS using Terraform! In this video, we delve into the essential concept of a Zero Trust Network and demonstrate how to leverage Twingate for securing your AWS environment.
What You'll Learn
1. Understanding Zero Trust Network Model We'll start with a brief introduction to the Zero Trust Network model, explaining how it differs from traditional security approaches. You'll learn why adopting Zero Trust is crucial in today's cybersecurity landscape and how it ensures that every access request is authenticated and authorized.
2. Overview of Twingate Next, we’ll provide an overview of Twingate, a cutting-edge solution for secure remote access. You'll understand how Twingate facilitates the implementation of Zero Trust principles and simplifies network security management.
3. Setting Up Twingate Connector Using Terraform We’ll walk you through the process of setting up the Twingate Connector using Terraform. You'll learn how to write and apply Terraform configurations to deploy the Twingate Connector on your AWS infrastructure efficiently.
4. Configuring Twingate Resource on AWS In this section, we’ll demonstrate how to configure Twingate resources on AWS. You’ll see the steps involved in integrating Twingate with your AWS environment, ensuring secure access to your cloud resources.
5. Testing Connectivity from Mobile to AWS EC2 Once the setup is complete, we'll test the connectivity from a mobile device to an AWS EC2 instance. This practical demonstration will show you how to verify that your Twingate configuration is working correctly, ensuring secure access from your mobile device.
6. Verifying Secure Access from Laptop to EC2 Instance with Private IP Finally, we'll test secure access from a laptop to an EC2 instance with a private IP. This step ensures that your Zero Trust Network setup allows authorized devices to access private cloud resources securely.
Resources and Links
• Twingate Documentation: Twingate Documentation
• Terraform AWS Provider: Terraform AWS Provider
• Sample Terraform Code: (Link to your repository or sample code if available)
Connect with Me
Stay Connected
If you found this video helpful, please give it a thumbs up, subscribe to the channel for more tutorials, and hit the bell icon to get notified when new videos are released. Feel free to leave any questions or feedback in the comments below!
#Twingate #Terraform #AWS #ZeroTrust #CloudSecurity #DevOps #CyberSecurity #NetworkSecurity #RemoteAccess #InfrastructureAsCode
Комментарии
 0:35:34
0:35:34
 0:09:57
0:09:57
 0:01:56
0:01:56
 0:19:31
0:19:31
 0:01:00
0:01:00
 0:44:12
0:44:12
 0:06:19
0:06:19
 0:41:54
0:41:54
 0:53:12
0:53:12
 0:40:06
0:40:06
 0:07:44
0:07:44
 0:41:45
0:41:45
 0:09:56
0:09:56
 0:06:41
0:06:41
 0:57:11
0:57:11
 0:52:23
0:52:23
 0:19:26
0:19:26
 0:00:58
0:00:58
 0:08:57
0:08:57
 0:51:39
0:51:39
 0:06:57
0:06:57
 0:03:36
0:03:36
 0:21:46
0:21:46
 0:10:31
0:10:31