filmov
tv
Understanding the OSI Model with Flipkart! | You Never Knew This! | Hacking | Part 1

Показать описание
Welcome to HackB4Hack! In this exciting video, we’re diving deep into the OSI Model using Flipkart as a real-world
🔍 Common Questions We’ll Address:
What is the OSI Model?
How does the OSI Model work?
Why is the OSI Model important in networking?
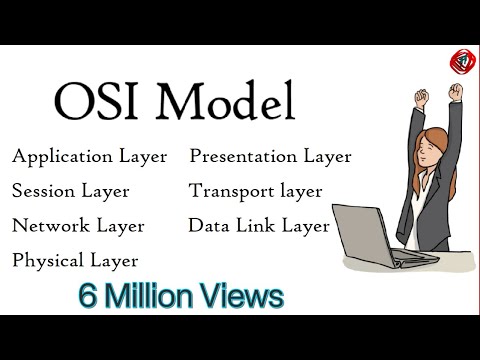
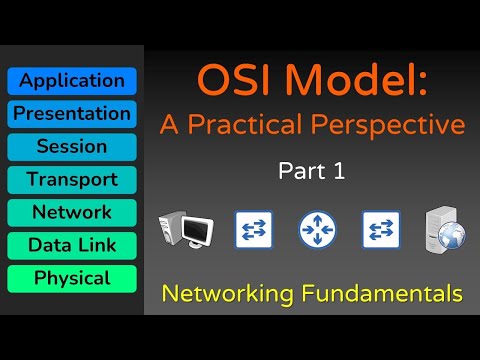
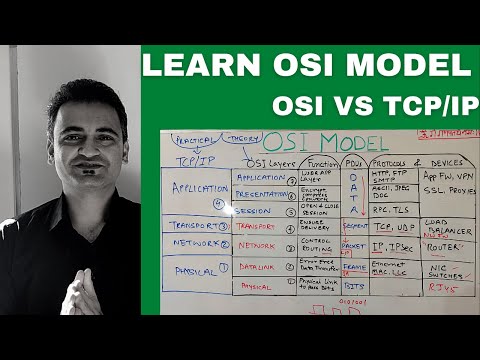
What are the seven layers of the OSI Model?
How does data travel through the OSI Model?
What is the difference between OSI and TCP/IP models?
What is a protocol in the context of the OSI Model?
How does SSL/TLS enhance security?
What happens during an SSL/TLS handshake?
What is an HTTP GET request?
How does HTTPS keep your information safe?
What are the main differences between HTTP and HTTPS?
Why is encryption important for data transmission?
What is a Man-in-the-Middle attack?
How does SSL prevent Man-in-the-Middle attacks?
What are the risks of using HTTP instead of HTTPS?
How can I tell if a website is using HTTPS?
What role does the Application Layer play in the OSI Model?
How does data encapsulation work in the OSI Model?
What is the Presentation Layer responsible for?
How do firewalls relate to the OSI Model?
What is a data packet, and how is it formed?
How does the Transport Layer ensure reliable communication?
What are TCP and UDP, and how do they fit into the OSI Model?
What is the function of the Session Layer?
How does the Network Layer route data?
What is the role of the Data Link Layer?
How does physical media affect data transmission?
What are the common protocols used at each layer of the OSI Model?
How does packet switching work?
What are common tools for analyzing network traffic?
How can I learn more about network security?
What certifications are available for aspiring ethical hackers?
How does the OSI Model apply to cloud computing?
What is a VPN, and how does it relate to the OSI Model?
How can businesses ensure secure data transmission?
What are the implications of not using HTTPS?
How does web hosting affect site security?
What is a public key infrastructure (PKI)?
What are SSL certificates, and how do they work?
How do browsers enforce HTTPS?
What are common vulnerabilities in web applications?
How can I perform a security audit on my website?
What tools can help with ethical hacking?
What is the difference between white-hat and black-hat hackers?
How can I protect my data online?
What is social engineering in cybersecurity?
How do phishing attacks work?
What should I do if I suspect a security breach?
What is the importance of regular software updates?
How does the OSI Model relate to IoT devices?
What is the role of DNS in web browsing?
How can I secure my home network?
What are the best practices for creating strong passwords?
How does data loss prevention (DLP) work?
What is penetration testing?
How can I start learning ethical hacking?
What resources are available for learning about the OSI Model?
How does encryption impact data transfer speeds?
What is network latency, and why does it matter?
How does packet fragmentation work?
What are the implications of GDPR for data security?
How do security policies protect businesses?
What is network segmentation?
How does a load balancer work?
What is the difference between a hub and a switch?
How do content delivery networks (CDNs) enhance performance?
What is a DDoS attack, and how can it be mitigated?
What are security best practices for web developers?
How do SSL and TLS differ?
What are the advantages of using HTTPS?
How do cookies impact web security?
What is cross-site scripting (XSS)?
How can I prevent SQL injection attacks?
What is a security information and event management (SIEM) system?
How can I implement two-factor authentication?
What is malware, and how can I protect against it?
What role does encryption play in protecting personal information?
How does remote work impact network security?
What are the challenges of securing mobile applications?
How does social media impact cybersecurity?
What is ethical hacking, and why is it important?
How can I conduct a risk assessment for my business?
What are the signs of a compromised system?
How do I choose the right cybersecurity tools?
What is a zero-day vulnerability?
How can I stay updated on cybersecurity trends?
What is the role of ethical hackers in improving security?
How do I report a security vulnerability I discover?
What are the consequences of ignoring cybersecurity?
How do I create an incident response plan?
What are the benefits of security awareness training?
How does encryption work in cloud storage?
What is the role of compliance in cybersecurity?
How can I secure my online accounts?
What is a firewall, and how does it function?
How do phishing scams operate?
What should I know about ransomware?
How can I identify suspicious online activity?
📱 Follow Us:
Instagram: @hackb4hack
🔗 Stay Tuned:
Subscribe to HackB4Hack for more tutorials on cybersecurity, web security, and ethical hacking. Our mission is to empower you with the skills you need to succeed in the tech world!
🔍 Common Questions We’ll Address:
What is the OSI Model?
How does the OSI Model work?
Why is the OSI Model important in networking?
What are the seven layers of the OSI Model?
How does data travel through the OSI Model?
What is the difference between OSI and TCP/IP models?
What is a protocol in the context of the OSI Model?
How does SSL/TLS enhance security?
What happens during an SSL/TLS handshake?
What is an HTTP GET request?
How does HTTPS keep your information safe?
What are the main differences between HTTP and HTTPS?
Why is encryption important for data transmission?
What is a Man-in-the-Middle attack?
How does SSL prevent Man-in-the-Middle attacks?
What are the risks of using HTTP instead of HTTPS?
How can I tell if a website is using HTTPS?
What role does the Application Layer play in the OSI Model?
How does data encapsulation work in the OSI Model?
What is the Presentation Layer responsible for?
How do firewalls relate to the OSI Model?
What is a data packet, and how is it formed?
How does the Transport Layer ensure reliable communication?
What are TCP and UDP, and how do they fit into the OSI Model?
What is the function of the Session Layer?
How does the Network Layer route data?
What is the role of the Data Link Layer?
How does physical media affect data transmission?
What are the common protocols used at each layer of the OSI Model?
How does packet switching work?
What are common tools for analyzing network traffic?
How can I learn more about network security?
What certifications are available for aspiring ethical hackers?
How does the OSI Model apply to cloud computing?
What is a VPN, and how does it relate to the OSI Model?
How can businesses ensure secure data transmission?
What are the implications of not using HTTPS?
How does web hosting affect site security?
What is a public key infrastructure (PKI)?
What are SSL certificates, and how do they work?
How do browsers enforce HTTPS?
What are common vulnerabilities in web applications?
How can I perform a security audit on my website?
What tools can help with ethical hacking?
What is the difference between white-hat and black-hat hackers?
How can I protect my data online?
What is social engineering in cybersecurity?
How do phishing attacks work?
What should I do if I suspect a security breach?
What is the importance of regular software updates?
How does the OSI Model relate to IoT devices?
What is the role of DNS in web browsing?
How can I secure my home network?
What are the best practices for creating strong passwords?
How does data loss prevention (DLP) work?
What is penetration testing?
How can I start learning ethical hacking?
What resources are available for learning about the OSI Model?
How does encryption impact data transfer speeds?
What is network latency, and why does it matter?
How does packet fragmentation work?
What are the implications of GDPR for data security?
How do security policies protect businesses?
What is network segmentation?
How does a load balancer work?
What is the difference between a hub and a switch?
How do content delivery networks (CDNs) enhance performance?
What is a DDoS attack, and how can it be mitigated?
What are security best practices for web developers?
How do SSL and TLS differ?
What are the advantages of using HTTPS?
How do cookies impact web security?
What is cross-site scripting (XSS)?
How can I prevent SQL injection attacks?
What is a security information and event management (SIEM) system?
How can I implement two-factor authentication?
What is malware, and how can I protect against it?
What role does encryption play in protecting personal information?
How does remote work impact network security?
What are the challenges of securing mobile applications?
How does social media impact cybersecurity?
What is ethical hacking, and why is it important?
How can I conduct a risk assessment for my business?
What are the signs of a compromised system?
How do I choose the right cybersecurity tools?
What is a zero-day vulnerability?
How can I stay updated on cybersecurity trends?
What is the role of ethical hackers in improving security?
How do I report a security vulnerability I discover?
What are the consequences of ignoring cybersecurity?
How do I create an incident response plan?
What are the benefits of security awareness training?
How does encryption work in cloud storage?
What is the role of compliance in cybersecurity?
How can I secure my online accounts?
What is a firewall, and how does it function?
How do phishing scams operate?
What should I know about ransomware?
How can I identify suspicious online activity?
📱 Follow Us:
Instagram: @hackb4hack
🔗 Stay Tuned:
Subscribe to HackB4Hack for more tutorials on cybersecurity, web security, and ethical hacking. Our mission is to empower you with the skills you need to succeed in the tech world!
 0:08:23
0:08:23
 0:04:45
0:04:45
 0:16:39
0:16:39
 0:12:17
0:12:17
 0:04:08
0:04:08
 0:03:14
0:03:14
 0:19:20
0:19:20
 0:21:56
0:21:56
 0:01:44
0:01:44
 0:12:04
0:12:04
 0:09:24
0:09:24
 0:00:37
0:00:37
 0:31:52
0:31:52
 0:09:37
0:09:37
 0:13:51
0:13:51
 0:13:25
0:13:25
 0:06:09
0:06:09
 0:00:40
0:00:40
 0:00:57
0:00:57
 0:14:36
0:14:36
 0:00:39
0:00:39
 0:24:43
0:24:43
 0:13:55
0:13:55
 0:08:29
0:08:29