filmov
tv
Brute Force Attack on SSH and how to secure it

Показать описание
This is my first video in Penetration Testing series. In this video I have used metasploit framework to brute force SSH. And I have also given the solution how you can secure it.
DISCLAIMER: This video is only for educational and research purpose only. I won't be held responsible for the misuse of knowledge shared in this video. During the video, if I say *Hacking*, that only means *Ethical Hacking*. You can perform the knowledge gained from video on your own computers which isn't illegal. Without permission, doing such hack attempts on other people's computers is illegal and I strongly condemn it.
#BruteForce
DISCLAIMER: This video is only for educational and research purpose only. I won't be held responsible for the misuse of knowledge shared in this video. During the video, if I say *Hacking*, that only means *Ethical Hacking*. You can perform the knowledge gained from video on your own computers which isn't illegal. Without permission, doing such hack attempts on other people's computers is illegal and I strongly condemn it.
#BruteForce
how to brute force attack a SSH server
50 Attacking SSH - Bruteforce Attack
How Hackers Could Brute-Force SSH Credentials to Gain Access to Servers
How to Brute Force SSH Like a Pro | Ethical Hacking Guide
SSH Brute-Force Attack - Wir hacken uns jetzt ein.. (Parrot OS) #kali
Brute Force Attack on SSH: Understanding the Risks and How to Protect Yourself
Ten Minute Tutorials : How to Brute Force SSH!
10 Attacking SSH Bruteforce Attack
Ethical Hacking Essentials: I Let Hackers Attack My Server SSH Brute Force, Cache Poisoning & Mo...
ssh bruteforce by hydra & Linux Privilege Escalation
Bruteforcing SSH with Hydra!
Brute Forcing SSH | Brute Force Attack Testing
How Easy Is It For Hackers To Brute Force Login Pages?!
Brute force SSH attack | Ethical Hacking Tutorial(2025) #SSH#BruteForce#EthicalHacking#CyberSecurity
Intro to Metasploit: SSH Brute Force Attack
Python Brute Force Password hacking (Kali Linux SSH)
Investigate SSH Brute Force Attack | Day 26
SSH Attack | Gain SSH Access to Servers by Brute-Forcing Credentials
Brute Force Attack on SSH and how to secure it
SSH Brute Force Attack detection using Wazuh
How Hackers Could Brute-Force SSH Credentials to Gain Access to Servers
Brute Forcing SSH with Hydra
How to exploit SSH with Metsaploit? | Kali Linux
Brute-Force Attacks on SSH? Here’s How to Defend! 🛡️|| #ethicalhacking #cyberawareness #howto...
Комментарии
 0:04:11
0:04:11
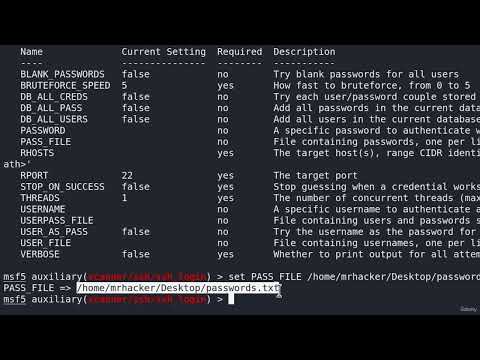 0:11:57
0:11:57
 0:17:15
0:17:15
 0:06:28
0:06:28
 0:10:24
0:10:24
 0:25:10
0:25:10
 0:10:20
0:10:20
 0:11:57
0:11:57
 1:06:55
1:06:55
 0:05:20
0:05:20
 0:04:43
0:04:43
 0:03:23
0:03:23
 0:04:29
0:04:29
 0:08:13
0:08:13
 0:10:58
0:10:58
 0:10:45
0:10:45
 0:15:27
0:15:27
 0:03:23
0:03:23
 0:20:21
0:20:21
 0:06:11
0:06:11
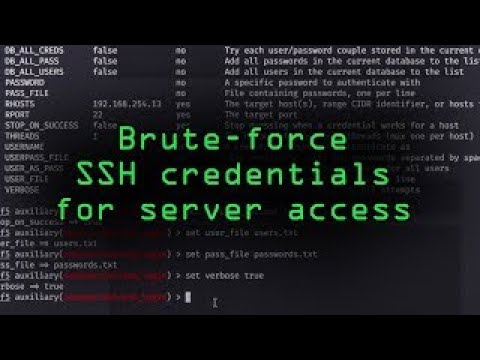 0:15:41
0:15:41
 0:02:25
0:02:25
 0:07:48
0:07:48
 0:02:36
0:02:36