filmov
tv
OAuth 2.0 Auth Code Injection Attack in Action

Показать описание
Here are some useful/foundational links for learning about OAuth 2.0:
Okta is a developer API service that stores user accounts for your web apps, mobile apps, and APIs.
Okta is a developer API service that stores user accounts for your web apps, mobile apps, and APIs.
Visualizing the OAuth Flow and Why PKCE is Needed
OAuth PKCE | OAuth Proof Key for Code Exchange explained
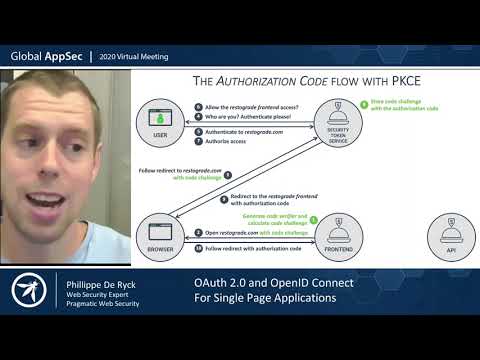
OAuth 2 0 and OpenID Connect for Single Page Applications Philippe De Ryck
Auth0 in 100 Seconds // And beyond with a Next.js Authentication Tutorial
OAUTH MISCONFIGURATION | PROCESS | BUG BOUNTY POC
Samit Anwer - Oh! Auth Implementation pitfalls of OAuth 2 0 & the Auth Providers who have fell
Introduction to OAuth 2.0 and OpenID Connect By Philippe De Ryck
OAuth2 Login Made Easy in Java: A Spring Boot & Spring Security Walkthrough
HACKING OAuth 2.0 FOR BEGINNERS!
OAuth 2.0 Hacking for Beginners with Farah Hawa
More Secure JavaScript Single-Page Applications with MSAL 2.0 and OAuth 2.0 Auth Code Flow with PKCE
alert‘OAuth 2 0’; // The impact of XSS on OAuth 2 0 in SPAs
OAuth implicit flow
OAuth 2.0 Authorization code flow for explained with example | Single Sign On
Authentication Explained: What is OAuth2? | Tokyo Bootcamp Tech Talk
Authentication done right: Consuming (and serving) Oauth 2.0
Top 12 Tips For API Security
OAuth 2 0 Threat Landscape
[Spring Security] Mastering JWT with OAuth2 and JPA for Secure User Authentication & Authorizati...
Rest Assured API Testing Session # 11 - Authorization | OAuth 2.0
OAuth Introduction And OAuth 2.0 authentication vulnerabilities | What is OAuth? #1
Stealing Users OAuth authorization code via redirect_uri | POC | P1 | $2000
Python FastAPI Secure your service with OAuth2 easily
The insecurity of OAuth 2.0 in frontends - Philippe de Ryck - NDC Security 2023
Комментарии
 0:01:42
0:01:42
 0:09:39
0:09:39
 0:36:53
0:36:53
 0:08:24
0:08:24
 0:02:00
0:02:00
 0:44:34
0:44:34
 2:43:46
2:43:46
 0:13:05
0:13:05
 0:10:26
0:10:26
 0:45:38
0:45:38
 0:20:20
0:20:20
 1:00:34
1:00:34
 0:06:41
0:06:41
 0:24:43
0:24:43
 0:26:01
0:26:01
 0:38:49
0:38:49
 0:09:47
0:09:47
 0:38:58
0:38:58
![[Spring Security] Mastering](https://i.ytimg.com/vi/Wg6qWcDpoZU/hqdefault.jpg) 2:01:24
2:01:24
 0:44:23
0:44:23
 0:01:53
0:01:53
 0:00:52
0:00:52
 0:14:40
0:14:40
 0:57:18
0:57:18