filmov
tv
Intrusion Detection and Prevention Systems (IDS/IPS): Computer Security Lectures 2014/15 S1

Показать описание
The slides themselves are creative commons licensed CC-BY-SA, and images used are licensed as individually attributed.
Topics covered in this lecture include:
Intrusion Detection and Prevention Systems
Detection
Test Your Awareness: Do The Test
Terminology: True positive, False positive, True negative, False negative
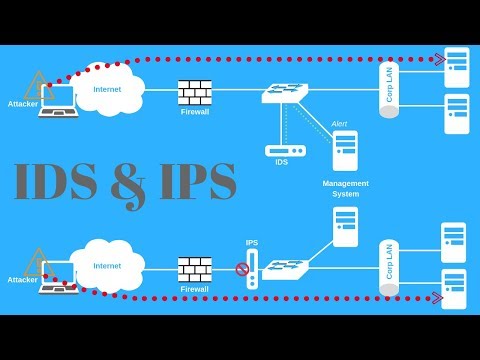
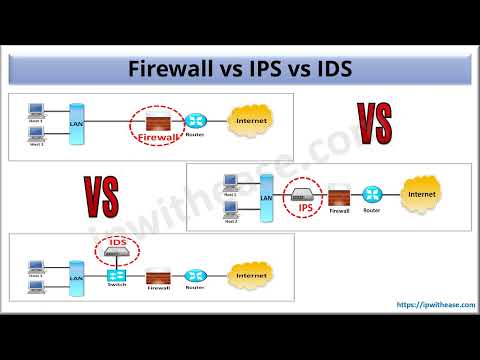
Intrusion Detection Systems
Network-based IDS
Host-based IDS monitors system activity
Intrusion Prevention Systems
Intrusion detection and prevention system (IDPS)
Network design
Signature-based detection
String or pattern matching
Anomaly-based detection
Statistical anomaly: activity differs from the baseline (heuristics of what normally happens on your network)
Protocol anomaly: traffic that does not conform to the protocol specifications (for example, something on port 80 that is not HTTP)
There are various ways that attacks can avoid being detected by an IDS
Anomaly-based: normal changes in activity can cause false positives
Signature-based: must be kept up-to-date
Encryption, alternative encoding, and so on
Packet fragmentation
Limitations
Snort
Simple signature-based rule language
Rules are prioritised based on complexity
Snort rules
Actions, Protocols, Directions, Pattern matching options, content
Alerts and logging
Snort commands
Snort rule sets
Other Snort tools
Monitoring Snort: ACARM-ng, Snortsnarf, SnortALog, Snort_stat, ACID
Responding
Other IDS
Bro, Suricata
Other IDS vendors
Recommended reading
Комментарии
 0:06:31
0:06:31
 0:10:50
0:10:50
 0:05:39
0:05:39
 0:07:58
0:07:58
 0:10:27
0:10:27
 0:03:19
0:03:19
 0:05:47
0:05:47
 0:06:16
0:06:16
 0:00:59
0:00:59
 0:11:23
0:11:23
 0:18:20
0:18:20
 0:03:45
0:03:45
 0:05:13
0:05:13
 0:58:10
0:58:10
 0:05:14
0:05:14
 0:28:00
0:28:00
 0:06:02
0:06:02
 0:06:58
0:06:58
 0:07:51
0:07:51
 0:05:30
0:05:30
 0:27:58
0:27:58
 0:21:00
0:21:00
 0:19:52
0:19:52
 0:05:39
0:05:39