filmov
tv
Format String Vulnerabilities | Binary Exploitation | PicoCTF Stonks

Показать описание
In this video walk-through, we demonstrated how to spot a format string vulnerability in a C program. We used a sample code from PicoCTF Stonks challenge.
*****************
Receive Cyber Security Field Notes and Special Training Videos
**********
Room Link
*********
Patreon
Backup channel
My Movie channel:
******
*****************
Receive Cyber Security Field Notes and Special Training Videos
**********
Room Link
*********
Patreon
Backup channel
My Movie channel:
******
A simple Format String exploit example - bin 0x11
Format String Vulnerabilities | Binary Exploitation | PicoCTF Stonks
7: Format String Vulnerabilities (printf) - Buffer Overflows - Intro to Binary Exploitation (Pwn)
Format String printf Vulnerabilities (PicoCTF 2022 #46 'flag-leak')
Format String to dump binary and gain RCE - 33c3ctf ESPR (pwn 150)
Binary Exploitation: Integer Overflows & Format String Vulnerabilities
Understanding Format String Vulnerability || Binary Exploitation - 0x11
Playing around with a Format String vulnerability and ASLR. format0 - bin 0x24
Introduction to format string vulnerabilities
Format String Exploit and overwrite the Global Offset Table - bin 0x13
Format String Exploit Troubleshooting Over Twitter - bin 0x11 b
Binary Explotation! Format String Vulnerability Challenge! Narnia5!
Cracking the Code: picoCTF Binary Exploitation - Format String 0 Walkthrough (Beginner Friendly)
Hack The Box - Introduction to Binary Exploitation - Leet Test - Format Strings [Walkthrough]
why do hackers love strings?
W4_1 - Format string vulnerabilities
160 - Some Browser Exploitation and a Format String Bug? [Binary Exploitation Podcast]
Binary Exploitation - Format String Vulnerabilities | MetaCTF April 2024 Walkthrough | CyberPranava
What is a Buffer Overflow Attack?
10: Bypassing Stack Canaries (leak + write) - Buffer Overflows - Intro to Binary Exploitation (Pwn)
Remote format string exploit in syslog() - bin 0x1E
Arbitrary Write Using Format String Vulnerability || Binary Exploitation - 0x13
coding in c until my program is unsafe
Global Offset Table (GOT) and Procedure Linkage Table (PLT) - bin 0x12
Комментарии
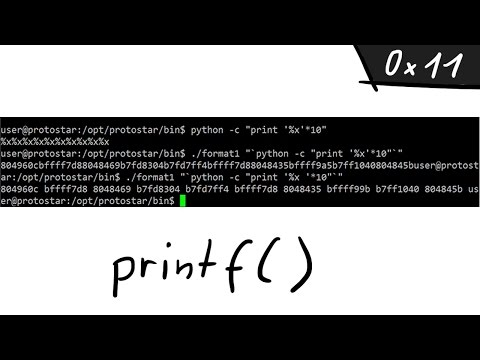 0:10:01
0:10:01
 0:13:02
0:13:02
 0:18:32
0:18:32
 0:19:44
0:19:44
 0:13:25
0:13:25
 1:23:13
1:23:13
 0:15:50
0:15:50
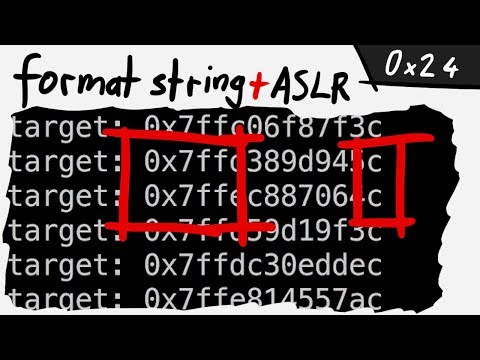 0:11:11
0:11:11
 0:11:21
0:11:21
 0:11:58
0:11:58
 0:24:59
0:24:59
 0:01:54
0:01:54
 0:02:01
0:02:01
 0:27:52
0:27:52
 0:05:42
0:05:42
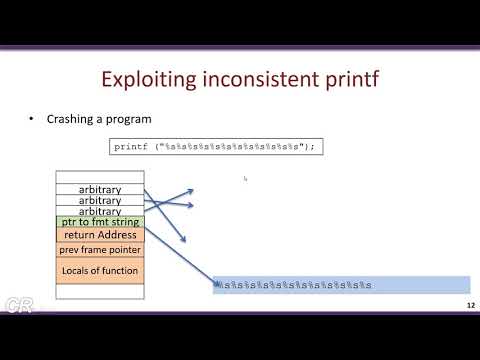 0:25:24
0:25:24
 0:43:48
0:43:48
 0:37:38
0:37:38
 0:02:24
0:02:24
 0:14:49
0:14:49
 0:13:45
0:13:45
 0:09:05
0:09:05
 0:00:48
0:00:48
 0:06:58
0:06:58