filmov
tv
Decode JWT

Показать описание
00:00 How to decode a JWT
01:05 Decoding a JWT in the command line
01:50 you will rarely need to base64-decode parts of a token by yourself
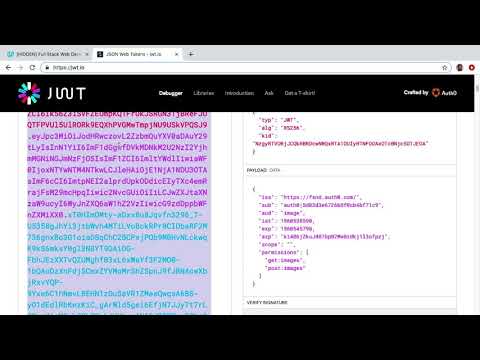
The individual parts of a JWT are base-64 url encoded. This is true for both the JSON Web Signature and the JSON Web Encryption token. Now before you can do anything with this token, you first need to decode the individual parts. Typically the library that you are using will take care of this for you. You will rarely have to bse64-url decode a token by yourself. All modern frameworks and programming languages like Spring, Spring Boot, Python, C# and so on offer libraries that can handle JWTs out of the box. For security reasons, it is recommended that you make use of these libraries and that you do not attempt to implement your own JWT logic.
When it comes to JSON Web Signature token, the content is just signed and not encrypted. This means that decoding the header and the claim set will give you the original data in plaintext. JSON Web Signature tokens only guarantee that you can detect if someone has tampered with the data. However, the data the token is carrying is not opaque because it is only base64-url encoded. To see the original data with JSON Web Encryption Tokens though you need to have the respective private key to see the original data.
Комментарии
 0:03:48
0:03:48
 0:02:01
0:02:01
 0:06:30
0:06:30
 0:01:07
0:01:07
 0:14:53
0:14:53
 0:03:48
0:03:48
 0:10:20
0:10:20
 0:02:39
0:02:39
 0:21:10
0:21:10
 0:15:20
0:15:20
 0:04:54
0:04:54
 0:05:13
0:05:13
 0:06:11
0:06:11
 0:16:59
0:16:59
 0:01:14
0:01:14
 0:10:20
0:10:20
 0:07:14
0:07:14
 0:00:17
0:00:17
 0:14:44
0:14:44
 0:17:23
0:17:23
 0:00:47
0:00:47
 0:01:10
0:01:10
 0:00:36
0:00:36
 0:17:46
0:17:46