filmov
tv
Securing the Linux boot process

Показать описание
Matthew Garrett
Linux has had support for UEFI Secure Boot for some time, which helps secure part of the boot process - you can be reasonably sure that nobody's replaced your bootloader or kernel, and that's sufficient to cover a bunch of cases. But for various technical reasons there's still a number of security critical components that are entirely unverified and which can be replaced by an attacker, and that means anyone with access to your system can configure it to steal (say) your hard drive encryption password. That's suboptimal.
There are various solutions to this involving TPMs, but so far they've all involved a lot of manual configuration and run the risk of being locked out of your machine for upgrading your kernel at the wrong time. Surely we can do better?
Unsurprisingly, yes. This presentation will describe some light modifications to the way distributions ship components that will make it possible to ensure that systems boot without running the risk of sensitive credentials being stolen but also without compromising the flexibility of the existing Linux boot process.
Linux has had support for UEFI Secure Boot for some time, which helps secure part of the boot process - you can be reasonably sure that nobody's replaced your bootloader or kernel, and that's sufficient to cover a bunch of cases. But for various technical reasons there's still a number of security critical components that are entirely unverified and which can be replaced by an attacker, and that means anyone with access to your system can configure it to steal (say) your hard drive encryption password. That's suboptimal.
There are various solutions to this involving TPMs, but so far they've all involved a lot of manual configuration and run the risk of being locked out of your machine for upgrading your kernel at the wrong time. Surely we can do better?
Unsurprisingly, yes. This presentation will describe some light modifications to the way distributions ship components that will make it possible to ensure that systems boot without running the risk of sensitive credentials being stolen but also without compromising the flexibility of the existing Linux boot process.
Securing the Linux boot process
How Does Linux Boot Process Work?
What are the Steps of the Linux Boot Process?
Linux Security Course - 4. Securing The Linux Boot Process
Bootloaders 101: How Do Embedded Processors Start? - Bryan Brattlof, Texas Instruments
Mastering Linux Security: Securing the Boot Process|packtpub.com
The Linux Boot Process (Linux+ Objective 1.1.2)
Secure boot in embedded Linux systems, Thomas Perrot
Update At Your Peril - Microsoft Breaks Grub, Torvalds Talks Kernel, & Linux LLMs
Embedded Linux Booting Process (Multi-Stage Bootloaders, Kernel, Filesystem)
UEFI boot explained (for Linux users)
UEFI Linux Secure Boot Kernel Signing and Verification demo
Version 252 Of Systemd Locks Down The Linux Boot Process
Secure Boot from A to Z - Quentin Schulz & Mylène Josserand, Bootlin (formerly Free Electrons)
What is Secure Boot? (EXPLAINED)
Using the TPM NVRAM to Protect Secure Boot Keys in POWER9 OpenPOWER Systems - Claudio de Carvalho
Lecture 15: Booting Process
Computer Boot Process animation
Secure Boot Overview
How ARM Systems are Booted: An Introduction to the ARM Boot Flow - Rouven Czerwinski
Basics of the Linux Boot Process
Linux Internals: UEFI Boot Stages using Debian 11
How to use UEFI | Every other YouTube video is WRONG!
Securing Embedded Linux Systems with TPM 2.0 - Philip Tricca, Intel
Комментарии
 0:45:42
0:45:42
 0:04:44
0:04:44
 0:10:51
0:10:51
 0:19:22
0:19:22
 0:38:34
0:38:34
 0:07:44
0:07:44
 0:26:33
0:26:33
 0:21:47
0:21:47
 1:25:57
1:25:57
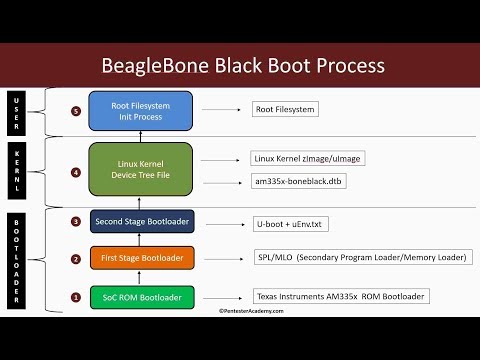 0:33:13
0:33:13
 0:08:06
0:08:06
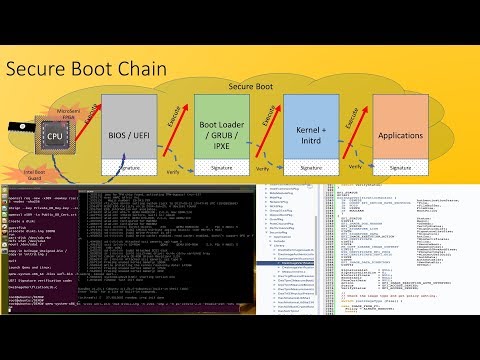 0:32:08
0:32:08
 0:04:49
0:04:49
 0:49:04
0:49:04
 0:02:58
0:02:58
 0:40:38
0:40:38
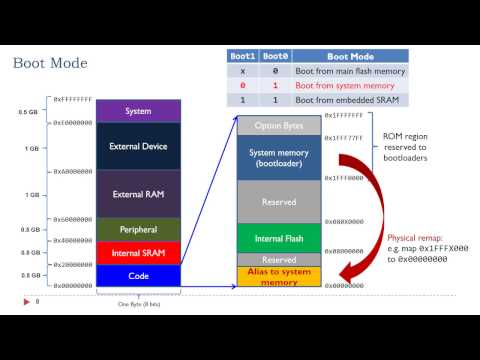 0:09:35
0:09:35
 0:02:37
0:02:37
 0:30:48
0:30:48
 0:36:47
0:36:47
 0:19:58
0:19:58
 0:28:14
0:28:14
 0:11:40
0:11:40
 0:51:17
0:51:17