filmov
tv
ARP protocol and ARP spoofing(ARP cache poisoning)

Показать описание
In this video i will be explaining you about ARP Protocol and ARP spoofing(ARP cache poisoning).
Do checkout my blog on it.
Here is the link to it-
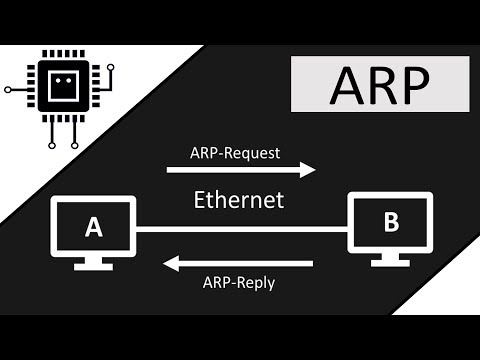
ARP-Address Resolution Protocol
-The second layer i.e. the Data Link Layer is the layer in which ARP protocol is used
-It is used to find the MAC address of a machine in LAN whose IP address is known
-As in Data Link Layer IP addresses are not much useful MAC addresses are used for communication within a LAN.
Steps involved:
-ARP Request
-ARP Response(ARP Reply)
ARP Table: Every machine in a LAN maintains an ARP Table which consists of two columns viz. IP address and MAC address. For faster communication MAC addresses are maintained for corresponding IP addresses so that every time ARP Request is not sent.
what is ARP Spoofing/ARP cache poisoning?
-Advantage of ARP is that it is simple to implement.
-Disadvantage of ARP is that it doesn't involve authentication i.e. it doesn't check that ARP Response is received from a valid source or not.
-This flaw is exploited by a technique we call as ARP spoofing or ARP cache poisoning.
-In ARP spoofing we poison the ARP cache or ARP Table by making a machine add wrong details in their ARP Table hence it is also called as ARP cache poisoning.
Do checkout my blog on it.
Here is the link to it-
ARP-Address Resolution Protocol
-The second layer i.e. the Data Link Layer is the layer in which ARP protocol is used
-It is used to find the MAC address of a machine in LAN whose IP address is known
-As in Data Link Layer IP addresses are not much useful MAC addresses are used for communication within a LAN.
Steps involved:
-ARP Request
-ARP Response(ARP Reply)
ARP Table: Every machine in a LAN maintains an ARP Table which consists of two columns viz. IP address and MAC address. For faster communication MAC addresses are maintained for corresponding IP addresses so that every time ARP Request is not sent.
what is ARP Spoofing/ARP cache poisoning?
-Advantage of ARP is that it is simple to implement.
-Disadvantage of ARP is that it doesn't involve authentication i.e. it doesn't check that ARP Response is received from a valid source or not.
-This flaw is exploited by a technique we call as ARP spoofing or ARP cache poisoning.
-In ARP spoofing we poison the ARP cache or ARP Table by making a machine add wrong details in their ARP Table hence it is also called as ARP cache poisoning.
 0:02:15
0:02:15
 0:04:22
0:04:22
 0:03:06
0:03:06
 0:01:32
0:01:32
 0:03:03
0:03:03
 0:11:35
0:11:35
 0:06:24
0:06:24
 0:07:28
0:07:28
 0:05:01
0:05:01
 0:00:38
0:00:38
 0:07:43
0:07:43
 0:03:42
0:03:42
 0:00:54
0:00:54
 0:08:40
0:08:40
 0:07:24
0:07:24
 0:00:49
0:00:49
 0:09:58
0:09:58
 0:09:07
0:09:07
 0:00:33
0:00:33
 0:10:02
0:10:02
 0:03:09
0:03:09
 0:02:08
0:02:08
 0:16:46
0:16:46
 0:12:02
0:12:02