filmov
tv
Exploit Development | Format Strings Series 6/6 - x64 exploitation + Final thoughts

Показать описание
Environment: Ubuntu 18.04 x64
References at end of video:
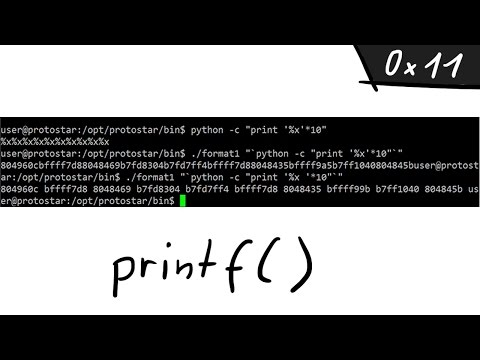
A simple Format String exploit example - bin 0x11
Global Offset Table (GOT) and Procedure Linkage Table (PLT) - bin 0x12
Format String Exploit and overwrite the Global Offset Table - bin 0x13
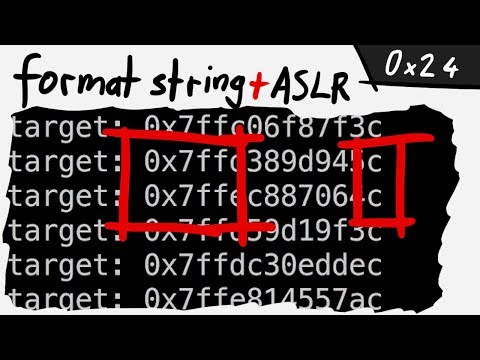
Playing around with a Format String vulnerability and ASLR. format0 - bin 0x24
If you enjoyed this video, feel free to donate to your favorite open source tool. There are some great people out there providing us with amazing tools that allow us to do these stuff.
References at end of video:
A simple Format String exploit example - bin 0x11
Global Offset Table (GOT) and Procedure Linkage Table (PLT) - bin 0x12
Format String Exploit and overwrite the Global Offset Table - bin 0x13
Playing around with a Format String vulnerability and ASLR. format0 - bin 0x24
If you enjoyed this video, feel free to donate to your favorite open source tool. There are some great people out there providing us with amazing tools that allow us to do these stuff.
A simple Format String exploit example - bin 0x11
Exploit Development | Format Strings Series 4/6 - Rewriting the GOT table
Exploit Development | Format Strings Series 1/6 - Intro and dumping sensitive data
Exploit Development | Format Strings Series 6/6 - x64 exploitation + Final thoughts
Exploit Development | Format Strings Series 2/6 - Redirecting code flow
Exploit Development | Format Strings Series 3/6 - More control over the writing process
Exploit Development | Format Strings Series 5/6 - Memory leak + ASLR bypass
format0 // protostar / A simple format string exploit exercise // exploit development../// writeup
Format String Attack | Exploit Development #Desafio02 Beco do Exploit #VM29 - Pegasus 1
Format String Exploits - Introduction
format2 ! Protostar // A simple format string exploit exercise // exploit dev/ writeup
Playing around with a Format String vulnerability and ASLR. format0 - bin 0x24
Intro Format String Vulnerability | PicoCTF 2017 [39] 'I've Got a Secret'
How To Scare C++ Programmer
why do hackers love strings?
What modern binary exploitation looks like
Ch 4 Format string bugs
Format string exploit Tamil | 0x0C
CNIT 127 Ch 4: Introduction to format string bugs
160 - Some Browser Exploitation and a Format String Bug? [Binary Exploitation Podcast]
Binary Exploit Development 4 - DEP Bypass with VirtualAlloc
Adapting the 32bit exploit to 64bit for format4 - bin 0x27
ED 204 Format String revisited
Arbitrary write using format string exploit | Binary Exploitation tamil | 0x0D
Комментарии
 0:10:01
0:10:01
 0:07:49
0:07:49
 0:11:12
0:11:12
 0:08:33
0:08:33
 0:07:17
0:07:17
 0:08:58
0:08:58
 0:09:28
0:09:28
 0:09:34
0:09:34
 0:48:40
0:48:40
 0:09:47
0:09:47
 0:06:21
0:06:21
 0:11:11
0:11:11
 0:16:31
0:16:31
 0:01:16
0:01:16
 0:05:42
0:05:42
 0:01:00
0:01:00
 0:43:20
0:43:20
 0:16:45
0:16:45
 0:42:14
0:42:14
 0:43:48
0:43:48
 0:12:49
0:12:49
 0:09:46
0:09:46
 0:19:37
0:19:37
 0:24:15
0:24:15