filmov
tv
Remote Desktop Protocol (RDP) Vulnerabilities and Security Best Practices

Показать описание
Remote Desktop Protocol (RDP), RDWeb, and RDGateway have legitimate uses for internal IT support. However, when they are used incorrectly or as a primary method for remote access, they can open organizations up to significant risks. If RDP is exposed and discoverable over the public internet, it can give potential attackers a direct path to steal data and money from the company. Accordingly, RDP is one of the top attack vectors threat actors are scanning for and looking to exploit.
#cybersecurity #riskmanagement #cyberrisk #RDP #remotedesktopprotocol #RDPvulnerability #remoteaccess
#cybersecurity #riskmanagement #cyberrisk #RDP #remotedesktopprotocol #RDPvulnerability #remoteaccess
 0:02:40
0:02:40
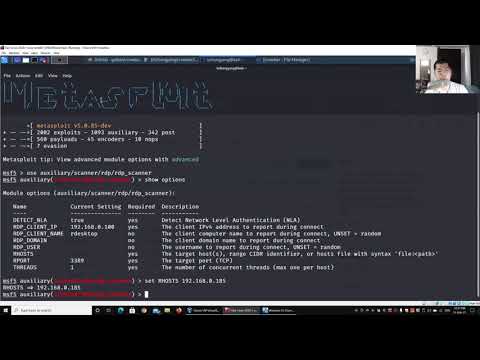 0:09:32
0:09:32
 0:00:47
0:00:47
 0:39:13
0:39:13
 0:04:41
0:04:41
 0:00:47
0:00:47
 0:00:22
0:00:22
 0:00:55
0:00:55
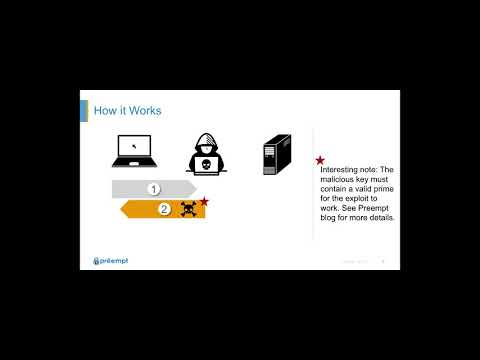 0:08:01
0:08:01
 0:01:43
0:01:43
 0:01:00
0:01:00
 0:01:11
0:01:11
 0:04:26
0:04:26
 0:02:57
0:02:57
 0:07:01
0:07:01
 0:28:44
0:28:44
 0:49:22
0:49:22
 0:13:19
0:13:19
 0:00:31
0:00:31
 0:00:15
0:00:15
 0:04:10
0:04:10
 0:02:12
0:02:12
 0:06:50
0:06:50
 0:09:47
0:09:47