filmov
tv
Towards Discovering Remote Code Execution Vulnerabilities in Apple FaceTime

Показать описание
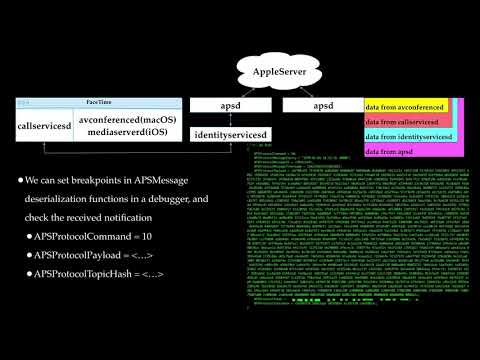
In this talk, we will share reverse engineering results of FaceTime, with a focus on the process of the initialization and connection of a FaceTime call. Along with the attacker-controlled data propagation path, we will discuss different attack surfaces for FaceTime.
By Tao Huang and Tielei Wang
By Tao Huang and Tielei Wang
 0:33:30
0:33:30
 0:33:30
0:33:30
 0:27:06
0:27:06
 0:35:58
0:35:58
 0:00:32
0:00:32
 0:00:27
0:00:27
 0:00:27
0:00:27
 0:00:39
0:00:39
 10:43:02
10:43:02
 0:03:43
0:03:43
 0:48:18
0:48:18
 0:00:59
0:00:59
 0:00:33
0:00:33
 0:02:19
0:02:19
 0:04:45
0:04:45
 0:00:57
0:00:57
 0:01:35
0:01:35
 0:12:58
0:12:58
 0:00:17
0:00:17
 0:01:11
0:01:11
 0:43:04
0:43:04
 0:00:34
0:00:34
 0:03:08
0:03:08
 0:01:52
0:01:52