filmov
tv
AWS Secrets Manager - Create Store and Retrieve a Secret
Показать описание
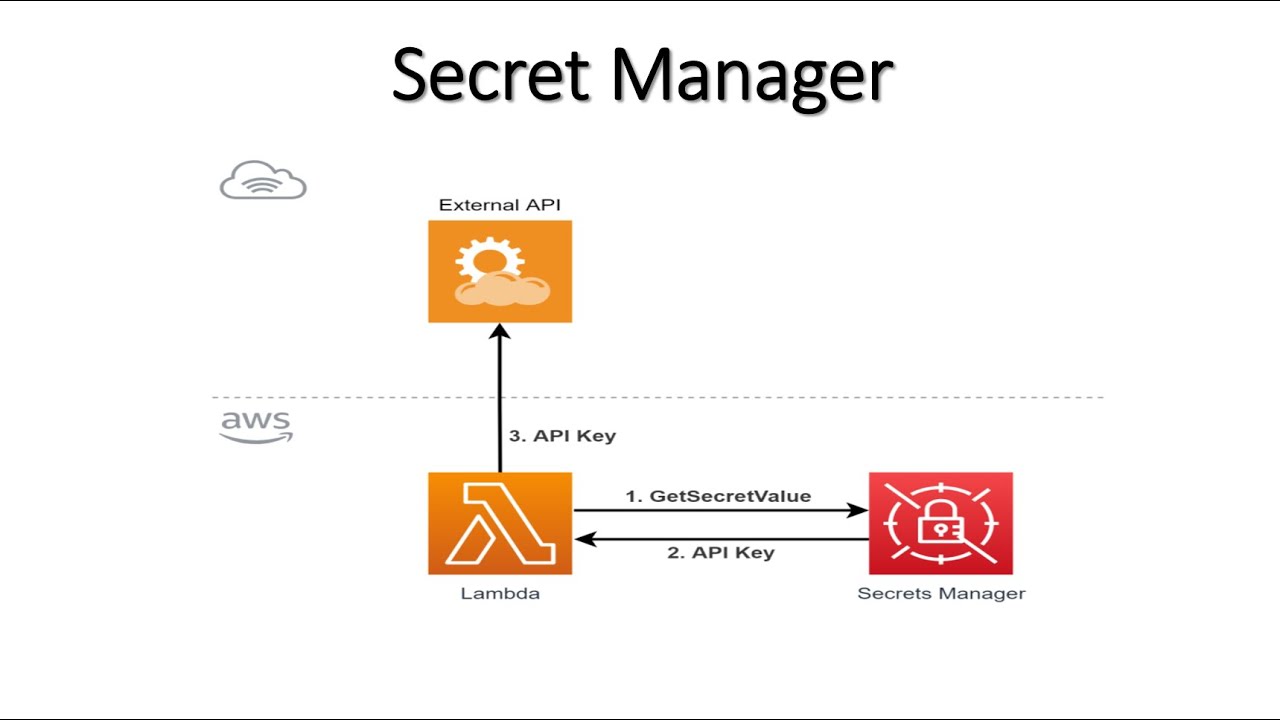
AWS Secrets Manager helps you protect secrets needed to access your applications, services, and IT resources.
The service enables you to easily rotate, manage, and retrieve database credentials, API keys, and other secrets throughout their lifecycle.
Users and applications retrieve secrets with a call to Secrets Manager APIs, eliminating the need to hardcode sensitive information in plain text.
Secrets Manager offers secret rotation with built-in integration for Amazon RDS, Amazon Redshift, and Amazon DocumentDB. Also, the service is extensible to other types of secrets, including API keys and OAuth tokens.
In addition, Secrets Manager enables you to control access to secrets using fine-grained permissions and audit secret rotation centrally for resources in the AWS Cloud, third-party services, and on-premises.
In my this video I have explained how to use AWS Secret Manager with AWS Lambda
Prerequisite:
Extract data from an API Python , Talend
Code:
import json
# Use this code snippet in your app.
# If you need more information about configurations or implementing the sample code, visit the AWS docs:
import boto3
import base64
import requests
def get_secret():
secret_name = "***********************************************************"
region_name = "us-east-1"
# Create a Secrets Manager client
service_name='secretsmanager',
region_name=region_name
)
# In this sample we only handle the specific exceptions for the 'GetSecretValue' API.
# We rethrow the exception by default.
get_secret_value_response=""
try:
SecretId=secret_name
)
except ClientError as e:
# Secrets Manager can't decrypt the protected secret text using the provided KMS key.
# Deal with the exception here, and/or rethrow at your discretion.
raise e
# An error occurred on the server side.
# Deal with the exception here, and/or rethrow at your discretion.
raise e
# You provided an invalid value for a parameter.
# Deal with the exception here, and/or rethrow at your discretion.
raise e
# You provided a parameter value that is not valid for the current state of the resource.
# Deal with the exception here, and/or rethrow at your discretion.
raise e
# We can't find the resource that you asked for.
# Deal with the exception here, and/or rethrow at your discretion.
raise e
else:
# Decrypts secret using the associated KMS CMK.
# Depending on whether the secret is a string or binary, one of these fields will be populated.
if 'SecretString' in get_secret_value_response:
secret = get_secret_value_response['SecretString']
else:
decoded_binary_secret = base64.b64decode(get_secret_value_response['SecretBinary'])
# Your code goes here.
return get_secret_value_response
def lambda_handler(event, context):
ms=get_secret()['SecretString'];
api_key=processed['api_key']
city_name=processed['city']
temp_city=data_extracted['main']['temp']
message="The temperature of {} city : {}".format(city_name,temp_city)
print(message)
Check this playlist for more AWS Concepts & Projects in Big Data domain:
The service enables you to easily rotate, manage, and retrieve database credentials, API keys, and other secrets throughout their lifecycle.
Users and applications retrieve secrets with a call to Secrets Manager APIs, eliminating the need to hardcode sensitive information in plain text.
Secrets Manager offers secret rotation with built-in integration for Amazon RDS, Amazon Redshift, and Amazon DocumentDB. Also, the service is extensible to other types of secrets, including API keys and OAuth tokens.
In addition, Secrets Manager enables you to control access to secrets using fine-grained permissions and audit secret rotation centrally for resources in the AWS Cloud, third-party services, and on-premises.
In my this video I have explained how to use AWS Secret Manager with AWS Lambda
Prerequisite:
Extract data from an API Python , Talend
Code:
import json
# Use this code snippet in your app.
# If you need more information about configurations or implementing the sample code, visit the AWS docs:
import boto3
import base64
import requests
def get_secret():
secret_name = "***********************************************************"
region_name = "us-east-1"
# Create a Secrets Manager client
service_name='secretsmanager',
region_name=region_name
)
# In this sample we only handle the specific exceptions for the 'GetSecretValue' API.
# We rethrow the exception by default.
get_secret_value_response=""
try:
SecretId=secret_name
)
except ClientError as e:
# Secrets Manager can't decrypt the protected secret text using the provided KMS key.
# Deal with the exception here, and/or rethrow at your discretion.
raise e
# An error occurred on the server side.
# Deal with the exception here, and/or rethrow at your discretion.
raise e
# You provided an invalid value for a parameter.
# Deal with the exception here, and/or rethrow at your discretion.
raise e
# You provided a parameter value that is not valid for the current state of the resource.
# Deal with the exception here, and/or rethrow at your discretion.
raise e
# We can't find the resource that you asked for.
# Deal with the exception here, and/or rethrow at your discretion.
raise e
else:
# Decrypts secret using the associated KMS CMK.
# Depending on whether the secret is a string or binary, one of these fields will be populated.
if 'SecretString' in get_secret_value_response:
secret = get_secret_value_response['SecretString']
else:
decoded_binary_secret = base64.b64decode(get_secret_value_response['SecretBinary'])
# Your code goes here.
return get_secret_value_response
def lambda_handler(event, context):
ms=get_secret()['SecretString'];
api_key=processed['api_key']
city_name=processed['city']
temp_city=data_extracted['main']['temp']
message="The temperature of {} city : {}".format(city_name,temp_city)
print(message)
Check this playlist for more AWS Concepts & Projects in Big Data domain:
Комментарии
 0:19:48
0:19:48
 0:17:12
0:17:12
 0:24:12
0:24:12
 0:33:50
0:33:50
 0:12:45
0:12:45
 0:06:16
0:06:16
 0:04:35
0:04:35
 0:13:15
0:13:15
 0:13:50
0:13:50
 0:26:39
0:26:39
 0:12:56
0:12:56
 0:08:44
0:08:44
 0:11:24
0:11:24
 0:06:22
0:06:22
 0:05:31
0:05:31
 0:14:05
0:14:05
 0:07:54
0:07:54
 0:20:32
0:20:32
 0:05:27
0:05:27
 0:15:29
0:15:29
 0:08:15
0:08:15
 0:08:13
0:08:13
 0:17:19
0:17:19
 0:03:37
0:03:37