filmov
tv
AddressSanitizer Tutorial 1 - Understanding the output (Stack Overflow)
Показать описание
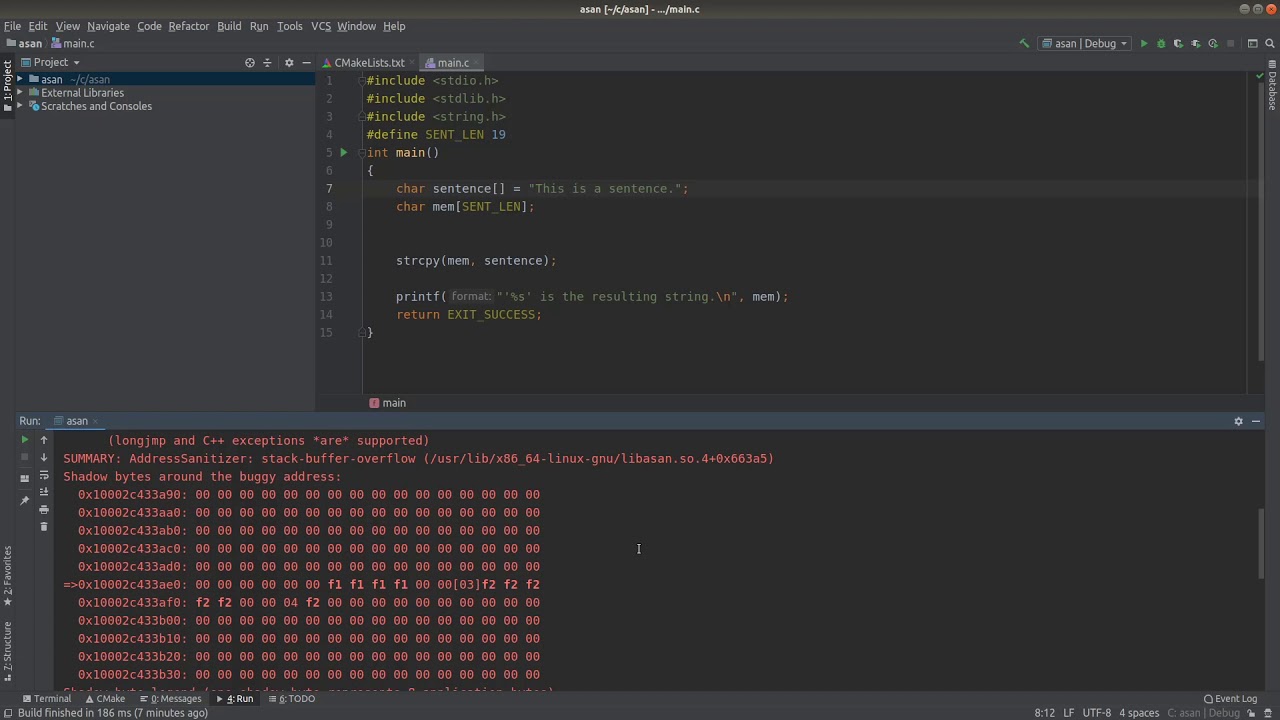
AddressSanitizer AKA ASAN is a very useful C/C++ memory debugging tool. In this video we examine a simple stack buffer overflow using AddressSanitizer. The focus here is on understanding the output that AddressSanitizer provides.
AddressSanitizer Tutorial 1 - Understanding the output (Stack Overflow)
find memory errors quickly. (-fsanitize, addresssanitizer)
AddressSanitizer Tutorial 3 - Heap Buffer Overflow
What is Address Sanitizer (ASAN), why use them and how it works?
AddressSanitizer Tutorial 4 - How it works under the hood
AddressSanitizer Tutorial #5 - Building real applications (Vim) with AddressSanitizer on Linux
Debugging with AddressSanitizer and UndefinedBehaviorSanitizer (UBSAN)
AddressSanitizer (ASan)
Address Sanitizer (ASan) Demonstration
AddressSanitizer Tutorial 2 - Moving to GDB (Coredump)
AddressSanitizer on Windows - Victor Ciura [ ACCU 2021 ]
Address Sanitizer in C++ (A Tutorial)
Tools of the Trade: Sanitizers
Root Cause Analysis With AddressSanitizer (ASan) | Ep. 06
The C++ memory leak detector no one told me about | address sanitizer
OSDI '21 - SANRAZOR: Reducing Redundant Sanitizer Checks in C/C++ Programs
Software Development with C++: Debugging with AddressSanitizer
Tech-ASan: Two-stage check for Address Sanitizer
Understanding AddressSanitizer: stack-use-after-scope in C++
Fuzzing 0x02 - Sanitizers, Virtual Memory and Paging
25-Spring, SW Testing, Homework 1
Finding hard to find bugs with Address Sanitizer - Marshall Clow - Meeting C++ 2019
Solving the ASan Leak Detection Issue on WSL 2
Fuzzing 0x02 - Sanitizers, Virtual Memory and Paging
Комментарии
 0:18:05
0:18:05
 0:09:44
0:09:44
 0:09:18
0:09:18
 0:09:12
0:09:12
 0:29:57
0:29:57
 0:07:53
0:07:53
 0:12:54
0:12:54
 0:14:09
0:14:09
 0:07:29
0:07:29
 0:07:23
0:07:23
 1:29:24
1:29:24
 0:18:17
0:18:17
 0:09:56
0:09:56
 0:09:32
0:09:32
 0:03:03
0:03:03
 0:14:09
0:14:09
 0:11:32
0:11:32
 0:08:19
0:08:19
 0:02:00
0:02:00
 1:26:53
1:26:53
 0:14:43
0:14:43
 0:06:50
0:06:50
 0:01:51
0:01:51
 0:33:31
0:33:31