filmov
tv
DEF CON 31 - certmitm Automatic Exploitation of TLS Certificate Validation Vulns - Aapo Oksman

Показать описание
TLS is the de facto way of securing network connections. It provides an easy way of ensuring confidentiality, integrity and authentication for any type of communication. However, like most things in life, this is also too good to be true.
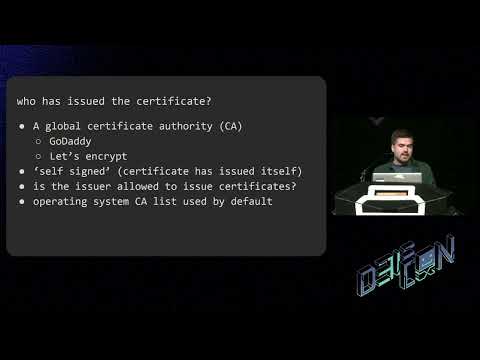
TLS allows communicating parties to uniquely authenticate each other by validating each other's certificate. However, many TLS libraries and frameworks have insecure default settings or allow for the developers to skip important aspects of certificate validation in their client implementations.
This talk explores issues in TLS client certificate validation and the underlying reasons why developers still fail to implement TLS correctly. Most importantly, we hack all the things with a new TLS mitm tool: certmitm.
certmitm automatically discovers and exploits insecure certificate validation vulnerabilities in TLS clients. Let's use the tool to hack iOS, Windows 11 and more while we deep dive into the world of insecure TLS certificate validation.
TLS allows communicating parties to uniquely authenticate each other by validating each other's certificate. However, many TLS libraries and frameworks have insecure default settings or allow for the developers to skip important aspects of certificate validation in their client implementations.
This talk explores issues in TLS client certificate validation and the underlying reasons why developers still fail to implement TLS correctly. Most importantly, we hack all the things with a new TLS mitm tool: certmitm.
certmitm automatically discovers and exploits insecure certificate validation vulnerabilities in TLS clients. Let's use the tool to hack iOS, Windows 11 and more while we deep dive into the world of insecure TLS certificate validation.
Комментарии
 0:50:09
0:50:09
 0:37:23
0:37:23
 0:19:45
0:19:45
 0:44:24
0:44:24
![[Disobey 2023] Exploiting](https://i.ytimg.com/vi/vZvL6ZRiKls/hqdefault.jpg) 1:01:43
1:01:43