filmov
tv
AWS VPC with Public and Private Subnets, NAT Instance/Bastion Host

Показать описание
Intro - 0:30
Why subnetting - 1:10
Creating a VPC - 7:35
VPC Wizard - 10:18
CIDR & subnets - 12:00
Using VPC Wizard - 17:20
NAT Gateway, NAT Instance, & Bastion Host - 19:00
Elastic IP - 24:30
Connecting to (NAT Instance) Bastion Host - 25:40
Why it doesn't connect - 28:00
Launching an instance in a private subnet - 32:40
Connecting to instance in private subnet - 38:20
SSH Agent Forwarding - 39:35
Allow instances in private subnet access to the Internet - 41:17
Logging in directly to instance in private subnet - 48:50
Shutting down your VPC to avoid charges - 55:45
Assignment intro - 59:30
Why subnetting - 1:10
Creating a VPC - 7:35
VPC Wizard - 10:18
CIDR & subnets - 12:00
Using VPC Wizard - 17:20
NAT Gateway, NAT Instance, & Bastion Host - 19:00
Elastic IP - 24:30
Connecting to (NAT Instance) Bastion Host - 25:40
Why it doesn't connect - 28:00
Launching an instance in a private subnet - 32:40
Connecting to instance in private subnet - 38:20
SSH Agent Forwarding - 39:35
Allow instances in private subnet access to the Internet - 41:17
Logging in directly to instance in private subnet - 48:50
Shutting down your VPC to avoid charges - 55:45
Assignment intro - 59:30
How to Create an AWS VPC with Public and Private Subnets
AWS VPC & Subnets For Beginners
AWS VPC Beginner to Pro - Virtual Private Cloud Tutorial
AWS how to setup VPC, Public, Private Subnet, NAT, Internet Gateway, Route Table? - (Part-5)
Create public and private subnets in AWS VPC to secure your containers
How to configure VPC with Public and Private Subnet on AWS
Amazon/AWS VPC (Virtual Private Cloud) Basics | VPC Tutorial | AWS for Beginners
How to create AWS VPC with Public and Private Subnet
How To Explain AWS DevOps Projects in an Interview | AWS DevOps Projects 08
AWS Networking: VPC Public Subnet vs Private Subnet
AWS VPC & Subnets | Amazon Web Services BASICS
Keep Your Network Traffic in AWS with VPC Endpoints | Overview and Tutorial
AWS Lab: Create a Virtual Private Cloud (VPC) with Public and Private Subnets
How to create a VPC with Public and Private Subnets
Mastering AWS: NAT Gateway Setup in Your VPC - A Step-by-Step Tutorial (Part-14)
Creating a VPC with Public and Private Subnets on AWS | Step-by-Step Guide |By 3xAWS Certified Ravan
Create AWS VPC with Private and Public Subnet | AWS Application Load Balancer | NAT Gateway
Public vs Private Subnets in AWS VPC: Setup, Use Cases, and Best Practices
AWS Tutorial - Scenario 2 VPC with Public & Private Subnets and NAT Gateway
How to Create a AWS VPC With Public and Private Subnets, NAT Gatways, NACLs, and MORE
AWS VPC: Public and Private Subnets
Master AWS VPC Endpoint | Step by Step Tutorial | Part-19
Introduction to AWS Networking
VPC with Public Subnet (Hands On) - AWS Certification Tutorial
Комментарии
 0:12:40
0:12:40
 0:16:39
0:16:39
 2:11:42
2:11:42
 0:35:41
0:35:41
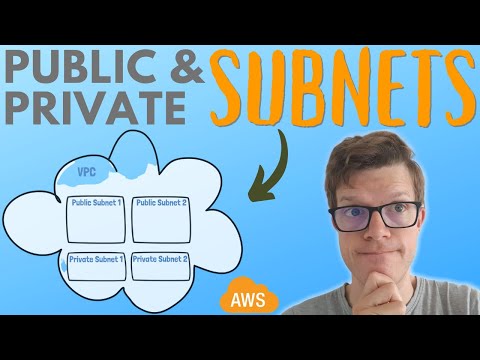 0:09:35
0:09:35
 0:19:57
0:19:57
 0:09:50
0:09:50
 0:18:17
0:18:17
 0:40:39
0:40:39
 0:05:21
0:05:21
 0:21:31
0:21:31
 0:16:56
0:16:56
 0:12:01
0:12:01
 0:02:25
0:02:25
 0:23:38
0:23:38
 0:16:37
0:16:37
 0:19:33
0:19:33
 0:04:05
0:04:05
 0:49:05
0:49:05
 0:27:33
0:27:33
 0:08:20
0:08:20
 0:32:23
0:32:23
 0:30:02
0:30:02
 0:10:29
0:10:29