filmov
tv
DEF CON 29 Blockchain Village - Gokul Alex, Tejaswa Rastogi - Preventing Sandwich Attacks

Показать описание
A sandwich attack is Upon observing a trade of asset X for asset Y, an attacker front runs the victim trade by also buying asset Y, lets the victim execute the trade, and then back runs (executes after) the victim by trading back the amount gained in the first trade. Intuitively, one uses the knowledge that someone’s going to buy an asset, and that this trade will increase its price, to make a profit. The attacker’s plan is to buy this asset cheap, let the victim buy at an increased price, and then sell the received amount again at a higher price afterwards.
Our solution is the convergence of our research work in the space of Ethereum Security, Zero Knowledge Proofs, Verifiable Delay Functions, Verifiable Random Functions, Hash Time Locks, Polynomial Commitments, Pedersen Hash Functions, Hash Time Locked Contracts , Ring Signatures, Lattice Cryptography, Super Singular Isogenies etc. over the last one year. We have come up with a one of the first solution architecture combining Ring Signatures, Zero Knowledge Databases, Super Singular Isogenies and Hash Time Locks to prevent the manipulation of block time, block header and block body indexes.
Our solution is the convergence of our research work in the space of Ethereum Security, Zero Knowledge Proofs, Verifiable Delay Functions, Verifiable Random Functions, Hash Time Locks, Polynomial Commitments, Pedersen Hash Functions, Hash Time Locked Contracts , Ring Signatures, Lattice Cryptography, Super Singular Isogenies etc. over the last one year. We have come up with a one of the first solution architecture combining Ring Signatures, Zero Knowledge Databases, Super Singular Isogenies and Hash Time Locks to prevent the manipulation of block time, block header and block body indexes.
 0:49:40
0:49:40
 0:39:22
0:39:22
 0:40:13
0:40:13
 0:45:18
0:45:18
 1:03:23
1:03:23
 0:25:15
0:25:15
 0:46:27
0:46:27
 1:05:20
1:05:20
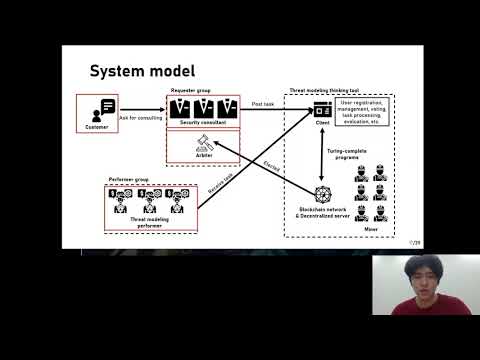 0:38:08
0:38:08
 0:44:45
0:44:45
 0:14:15
0:14:15
 8:36:52
8:36:52
 0:12:46
0:12:46
 1:05:20
1:05:20
 6:22:26
6:22:26
 0:41:05
0:41:05
 0:39:47
0:39:47
 0:41:07
0:41:07
 1:03:09
1:03:09
 0:47:07
0:47:07
 0:29:02
0:29:02
 0:51:55
0:51:55
 0:57:20
0:57:20
 0:32:22
0:32:22