filmov
tv
Resolving the unsafe-eval Error in JavaScript via Content Security Policy

Показать описание
Learn how to tackle the `unsafe-eval` Content Security Policy error in JavaScript with effective solutions and tips for improved security.
---
Visit these links for original content and any more details, such as alternate solutions, latest updates/developments on topic, comments, revision history etc. For example, the original title of the Question was: Refused to evaluate a string as JavaScript because 'unsafe-eval' is not an allowed source of script Content Security Policy directive:default-src self
If anything seems off to you, please feel free to write me at vlogize [AT] gmail [DOT] com.
---
Tackling the unsafe-eval Content Security Policy Error in JavaScript
If you’ve encountered the error message stating the refusal to evaluate a string as JavaScript due to unsafe-eval not being allowed in your Content Security Policy (CSP), you’re not alone. This message can cause frustration as it indicates a violation of security policies you've set for your application. In this guide, we will explore this problem, what it means, and how to effectively solve it.
Understanding the Problem
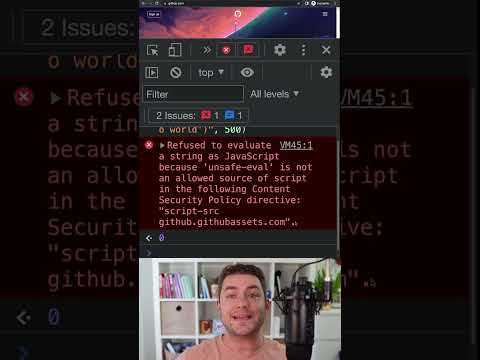
When setting up a Content Security Policy, the directive typically controls where resources such as scripts and styles can be loaded from. The error you see may look something like this:
[[See Video to Reveal this Text or Code Snippet]]
This message indicates several issues related to your CSP:
Inline Scripts: The browser has refused to execute inline scripts because your CSP does not permit inline execution without additional permissions like unsafe-inline.
External Stylesheets: The browser also blocks external resources like stylesheets from, in this case, Google Fonts due to strict CSP rules.
In essence, your CSP settings may need to be updated to allow some scripting and loading behaviors without compromising security entirely.
Solution Overview
To resolve this issue, you will need to adjust your Content Security Policy directives. Here's a breakdown of how to make sure everything runs smoothly and securely:
Step 1: Update Your Content Security Policy
You need to specifically define the script-src and style-src settings in your CSP. Below is a recommended structure for your CSP header:
[[See Video to Reveal this Text or Code Snippet]]
Key Components
default-src 'self': This directive allows loading resources from the same origin as your site, enhancing security.
script-src 'self' 'unsafe-eval': Adding unsafe-eval allows JavaScript to evaluate strings as code, which is commonly used in many libraries. It's important to note that using this option can expose your application to security vulnerabilities, as it allows the execution of potentially unsafe code.
Step 2: Test Your Application
After updating the CSP:
Check Console Errors: Open your browser’s developer console to check for any ongoing CSP violations.
Load Your Application: Make sure to test the functionality and ensure styles and scripts are being applied correctly.
Adjust as Necessary: If errors persist, you may need to reevaluate the needed sources and adjust your CSP further, still keeping an eye on security.
Important Considerations
Security Risks: Using unsafe-eval reduces your application's security by allowing the execution of dynamic code. Consider refactoring your codebase to avoid the need for eval or similar JavaScript functions if possible.
Content Security Policy Reporting: Utilize the report-uri directive in CSP to get notified about security violations. This can be an invaluable way to improve your policies over time.
Conclusion
By carefully adjusting your CSP directives, you can eliminate the unsafe-eval error and keep your application secure at the same time. It's crucial to balance functionality with security and always be mindful of the implications of the settings you choose. Avoid unnecessary use of unsafe-eval and consider alternative approaches to scripting.
Embrace a more secure web development approach and continuously iterate on your CSP to protect your application from emerging threats.
---
Visit these links for original content and any more details, such as alternate solutions, latest updates/developments on topic, comments, revision history etc. For example, the original title of the Question was: Refused to evaluate a string as JavaScript because 'unsafe-eval' is not an allowed source of script Content Security Policy directive:default-src self
If anything seems off to you, please feel free to write me at vlogize [AT] gmail [DOT] com.
---
Tackling the unsafe-eval Content Security Policy Error in JavaScript
If you’ve encountered the error message stating the refusal to evaluate a string as JavaScript due to unsafe-eval not being allowed in your Content Security Policy (CSP), you’re not alone. This message can cause frustration as it indicates a violation of security policies you've set for your application. In this guide, we will explore this problem, what it means, and how to effectively solve it.
Understanding the Problem
When setting up a Content Security Policy, the directive typically controls where resources such as scripts and styles can be loaded from. The error you see may look something like this:
[[See Video to Reveal this Text or Code Snippet]]
This message indicates several issues related to your CSP:
Inline Scripts: The browser has refused to execute inline scripts because your CSP does not permit inline execution without additional permissions like unsafe-inline.
External Stylesheets: The browser also blocks external resources like stylesheets from, in this case, Google Fonts due to strict CSP rules.
In essence, your CSP settings may need to be updated to allow some scripting and loading behaviors without compromising security entirely.
Solution Overview
To resolve this issue, you will need to adjust your Content Security Policy directives. Here's a breakdown of how to make sure everything runs smoothly and securely:
Step 1: Update Your Content Security Policy
You need to specifically define the script-src and style-src settings in your CSP. Below is a recommended structure for your CSP header:
[[See Video to Reveal this Text or Code Snippet]]
Key Components
default-src 'self': This directive allows loading resources from the same origin as your site, enhancing security.
script-src 'self' 'unsafe-eval': Adding unsafe-eval allows JavaScript to evaluate strings as code, which is commonly used in many libraries. It's important to note that using this option can expose your application to security vulnerabilities, as it allows the execution of potentially unsafe code.
Step 2: Test Your Application
After updating the CSP:
Check Console Errors: Open your browser’s developer console to check for any ongoing CSP violations.
Load Your Application: Make sure to test the functionality and ensure styles and scripts are being applied correctly.
Adjust as Necessary: If errors persist, you may need to reevaluate the needed sources and adjust your CSP further, still keeping an eye on security.
Important Considerations
Security Risks: Using unsafe-eval reduces your application's security by allowing the execution of dynamic code. Consider refactoring your codebase to avoid the need for eval or similar JavaScript functions if possible.
Content Security Policy Reporting: Utilize the report-uri directive in CSP to get notified about security violations. This can be an invaluable way to improve your policies over time.
Conclusion
By carefully adjusting your CSP directives, you can eliminate the unsafe-eval error and keep your application secure at the same time. It's crucial to balance functionality with security and always be mindful of the implications of the settings you choose. Avoid unnecessary use of unsafe-eval and consider alternative approaches to scripting.
Embrace a more secure web development approach and continuously iterate on your CSP to protect your application from emerging threats.
 0:01:41
0:01:41
 0:01:47
0:01:47
 0:05:35
0:05:35
 0:01:07
0:01:07
 0:02:10
0:02:10
 0:01:09
0:01:09
 0:02:26
0:02:26
 0:08:53
0:08:53
 0:00:58
0:00:58
 0:10:32
0:10:32
 0:02:36
0:02:36
 0:01:07
0:01:07
 0:02:14
0:02:14
 0:01:38
0:01:38
 0:06:49
0:06:49
 0:00:36
0:00:36
 0:06:11
0:06:11
 0:01:23
0:01:23
 0:01:39
0:01:39
 0:02:01
0:02:01
 0:01:22
0:01:22
 0:01:48
0:01:48
 0:05:05
0:05:05
 0:01:03
0:01:03