filmov
tv
5 Must Have Tweaks to Secure OpenSSH

Показать описание
OpenSSH is a fantastic tool for remotely managing Linux servers, but with great power comes great responsibility! If a threat actor is able to gain access to OpenSSH on your Linux server, then they have full access to cause all kinds of mischief. In this video, Jay goes over 5 must-have tweaks to strengthen the security of OpenSSH on your server.
Thanks yet again to Linode for sponsoring this video!
*LEARN LINUX TV - YOUR HOME FOR LINUX-RELATED FUN AND LEARNING!*
Note: Affiliate revenue is earned from that URL
*💬 CHECK OUT OUR FORUMS*
Have a Linux question? Want to share a tip? Or maybe just hang out?
*🐧 SUPPORT LINUX LEARNING!*
_Note: Royalties and/or commission is earned from each of the above links_
*⏰ TIME CODES*
00:00 - intro
03:12 - Tweak 0: Disable the OpenSSH service if you don't plan on using it
05:07 - Tweak 1: Change the default port that SSH listens on
10:05 - Tweak 2: Preventing access to ssh from the root account
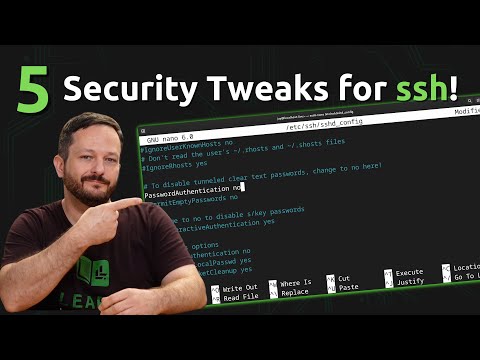
14:07 - Tweak 3: Disabling password authentication completely
17:09 - Tweak 4: Suggestion: Use a firewall rule to further protect SSH
19:21 - Tweak 5: Suggestion: Use a hardware key for extra security*🎓 FULL LINUX COURSES FROM LEARN LINUX TV*
*🌐 LEARN LINUX TV ON THE WEB*
*⚠️ DISCLAIMER*
Learn Linux TV provides technical content that will hopefully be helpful to you and teach you something new. However, this content is provided without any warranty (expressed or implied). Learn Linux TV is not responsible for any damages that may arise from any use of this content. Always make sure you have written permission before working with any infrastructure and that you are compliant with all company rules, change control procedures, and local laws.
#LinuxServer #DevOps #OpenSSH
Thanks yet again to Linode for sponsoring this video!
*LEARN LINUX TV - YOUR HOME FOR LINUX-RELATED FUN AND LEARNING!*
Note: Affiliate revenue is earned from that URL
*💬 CHECK OUT OUR FORUMS*
Have a Linux question? Want to share a tip? Or maybe just hang out?
*🐧 SUPPORT LINUX LEARNING!*
_Note: Royalties and/or commission is earned from each of the above links_
*⏰ TIME CODES*
00:00 - intro
03:12 - Tweak 0: Disable the OpenSSH service if you don't plan on using it
05:07 - Tweak 1: Change the default port that SSH listens on
10:05 - Tweak 2: Preventing access to ssh from the root account
14:07 - Tweak 3: Disabling password authentication completely
17:09 - Tweak 4: Suggestion: Use a firewall rule to further protect SSH
19:21 - Tweak 5: Suggestion: Use a hardware key for extra security*🎓 FULL LINUX COURSES FROM LEARN LINUX TV*
*🌐 LEARN LINUX TV ON THE WEB*
*⚠️ DISCLAIMER*
Learn Linux TV provides technical content that will hopefully be helpful to you and teach you something new. However, this content is provided without any warranty (expressed or implied). Learn Linux TV is not responsible for any damages that may arise from any use of this content. Always make sure you have written permission before working with any infrastructure and that you are compliant with all company rules, change control procedures, and local laws.
#LinuxServer #DevOps #OpenSSH
Комментарии
 0:21:48
0:21:48
 0:03:59
0:03:59
 0:04:48
0:04:48
 0:13:27
0:13:27
 0:03:37
0:03:37
 0:11:36
0:11:36
 0:05:36
0:05:36
 0:20:42
0:20:42
 0:07:12
0:07:12
 0:05:02
0:05:02
 0:04:30
0:04:30
 0:03:20
0:03:20
 0:03:56
0:03:56
 0:09:44
0:09:44
 0:02:06
0:02:06
 0:04:28
0:04:28
 0:07:03
0:07:03
 0:05:34
0:05:34
 0:00:53
0:00:53
 0:15:39
0:15:39
 0:06:33
0:06:33
 0:06:34
0:06:34
 0:04:54
0:04:54
 0:06:17
0:06:17