filmov
tv
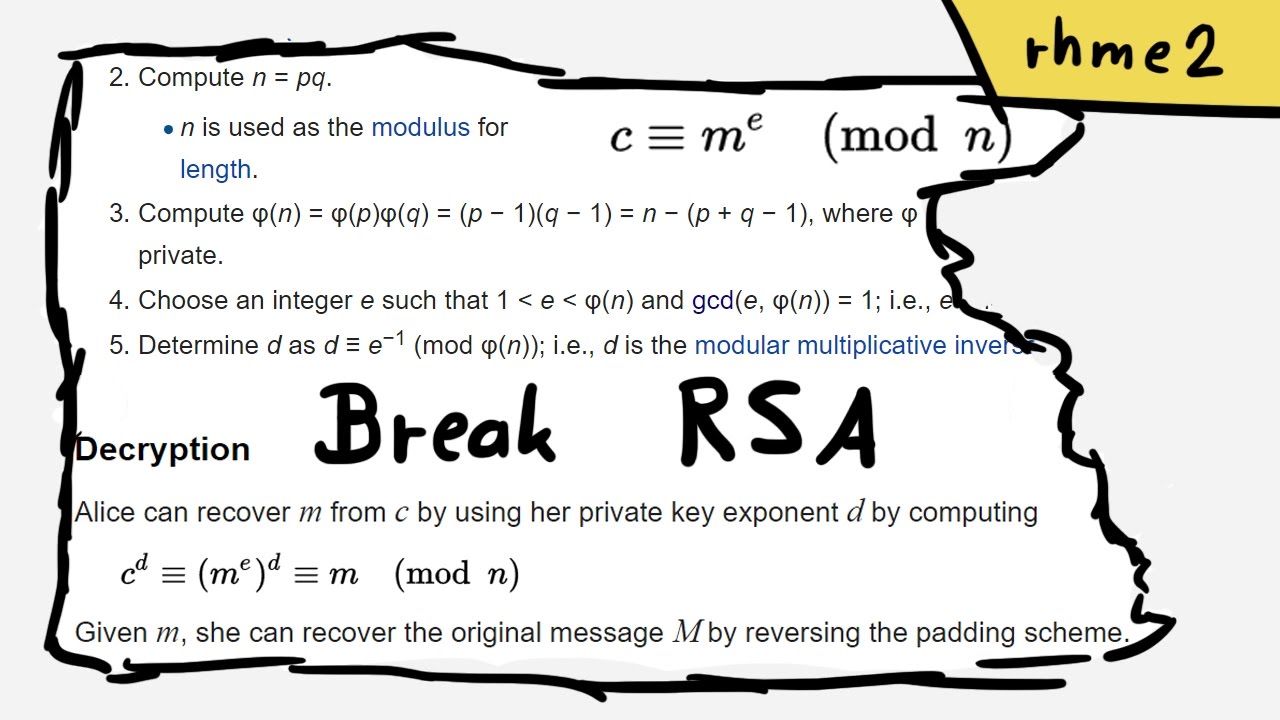
Recover RSA private key from public keys - rhme2 Key Server (crypto 200)
Показать описание
Using the greatest common divisor (GCD) to factorize the public modulo into the secret primes, so we can forge a RSA signature.
-=[ 🔴 Stuff I use ]=-
-=[ ❤️ Support ]=-
-=[ 🐕 Social ]=-
-=[ 📄 P.S. ]=-
All links with "*" are affiliate links.
LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
#CTF #Cryptography
-=[ 🔴 Stuff I use ]=-
-=[ ❤️ Support ]=-
-=[ 🐕 Social ]=-
-=[ 📄 P.S. ]=-
All links with "*" are affiliate links.
LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
#CTF #Cryptography
Recover RSA private key from public keys - rhme2 Key Server (crypto 200)
Recover a RSA Private Key From a TLS Session With Perfect Forward Secrecy
RECOVER WALLET PRIVATE KEY FROM ADDRESS (PUBLIC KEY) Easy Tutorial 2023
CONFidence 2016: Recover a RSA private key from a TLS session (Marco Ortisi)
Cracking RSA Get Private key with Public Key from python
How to decrypt RSA Private Key using OpenSSL
Retrieving the Private key and Certificate from a PFX
Recover a RSA Private Key From a TLS Session With Perfect Forward Secrecy
Password Cracking: Cracking Private Key Passphrase
Black Hat USA 2016 Recover a RSA Private Key From a TLS Session With Perfect Forward Secrecy
Unlocking the Secrets of RSA Encryption Privacy Made Possible
How To Generate RSA Public and Private Key Pair with OpenSSL
Hack The Box Beginner Track Weak RSA | Cracking Weak RSA Keys with the RSACtfTool
Breaking RSA - Computerphile
The RSA Encryption Algorithm (1 of 2: Computing an Example)
How to Encrypt with RSA (but easy)
Bitcoin Private Keys Recover Shell Exploit 2019
How to Recover your private keys using Ave.ai app. #aveai #blockchain
How to retrieve RSA private key from wrapped key blob?
John the Ripper: How to Recover Your PGP Private Key Password
Why not to derive an AES key from an RSA private key?
Generate public private key in Windows 10 using openssl
Private Key Finder, Get private key and withdraw from any wallet address
RSA Algorithm
Комментарии
 0:12:42
0:12:42
 0:42:25
0:42:25
 0:04:50
0:04:50
 0:37:18
0:37:18
 0:04:12
0:04:12
 0:00:59
0:00:59
 0:00:46
0:00:46
 0:42:25
0:42:25
 0:00:59
0:00:59
 0:42:25
0:42:25
 0:00:49
0:00:49
 0:04:11
0:04:11
 0:17:11
0:17:11
 0:14:50
0:14:50
 0:08:40
0:08:40
 0:06:01
0:06:01
 0:07:10
0:07:10
 0:03:24
0:03:24
 0:02:43
0:02:43
 0:03:22
0:03:22
 0:21:31
0:21:31
 0:04:59
0:04:59
 0:06:35
0:06:35
 0:10:45
0:10:45